本文最后更新于629 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
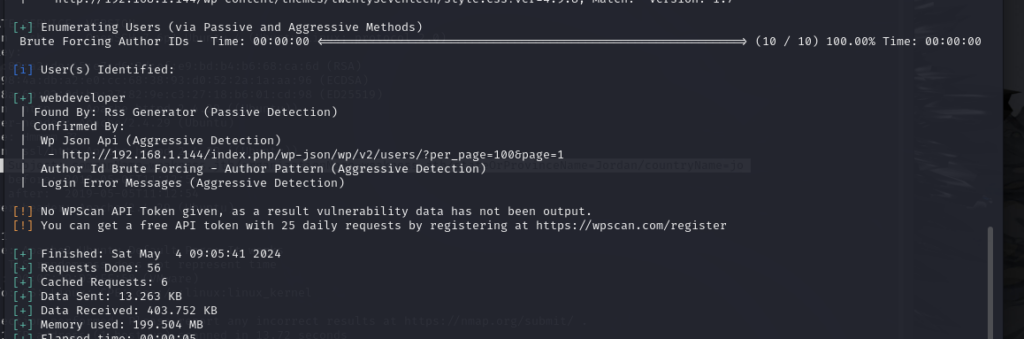
一、在当前网页搜索可疑文件
按F12 查看当前页面加载的图片 然后下载看一下
wget http://192.168.1.137/Challenge.png
exiftool challenge.png 可以看到有可以字符串
35:31:3a:35:33:3a:34:36:3a:35:37:3a:36:34:3a:35:38:3a:33:35:3a:37:31:3a:36:34:3a:34:35:3a:36:37:3a:36:61:3a:34:65:3a:37:61:3a:34:39:3a:33:35:3a:36:33:3a:33:30:3a:37:38:3a:34:32:3a:34:66:3a:33:32:3a:36:37:3a:33:30:3a:34:61:3a:35:31:3a:33:64:3a:33:64
ExifTool Version Number : 12.76
File Name : Challenge.png
Directory : .
File Size : 85 kB
File Modification Date/Time : 2015:09:01 14:25:59+08:00
File Access Date/Time : 2024:04:26 16:32:24+08:00
File Inode Change Date/Time : 2024:04:26 16:32:24+08:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 540
Image Height : 540
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Background Color : 255 255 255
Pixels Per Unit X : 2835
Pixels Per Unit Y : 2835
Pixel Units : meters
Comment : 35:31:3a:35:33:3a:34:36:3a:35:37:3a:36:34:3a:35:38:3a:33:35:3a:37:31:3a:36:34:3a:34:35:3a:36:37:3a:36:61:3a:34:65:3a:37:61:3a:34:39:3a:33:35:3a:36:33:3a:33:30:3a:37:38:3a:34:32:3a:34:66:3a:33:32:3a:36:37:3a:33:30:3a:34:61:3a:35:31:3a:33:64:3a:33:64
Image Size : 540x540
Megapixels : 0.292
处理一下 这些字符 首先判断是 十六进制数 可以尝试转十进制 然后转字符
可以使用 https://ctf.mzy0.com/CyberChef3/ cyberchef 在线转换
也可以尝试使用ipython3
f="35:31:3a:35:33:3a:34:36:3a:35:37:3a:36:34:3a:35:38:3a:33:35:3a:37:31:3a:36:34:3a:34:35:3a:36:37:3a:36:61:3a:34:65:3a:37:61:3a:34:39:3a:33:35:3a:36:33:3a:33:30:3a:37:38:3a:34:32:3a:34:66:3a:33:32:3a:36:37:3a:33:30:3a:34:61:3a:35:31:3a:33:64:3a:33:64"
f1=f.split(':')
data=''.join( [ chr(int(i,16)) for i in f1 ])
print(data) 51:53:46:57:64:58:35:71:64:45:67:6a:4e:7a:49:35:63:30:78:42:4f:32:67:30:4a:51:3d:3d
data1=''.join( [ chr(int(i,16)) for i in data.split(':') ])
print(data1)
QSFWdX5qdEgjNzI5c0xBO2g0JQ==
破解出来一个base64编码的字符串 解码 得到 A!Vu~jtH#729sLA;h4%
二、查看页面源代码
可以看到 存在一个js代码块 拿出来运行一下
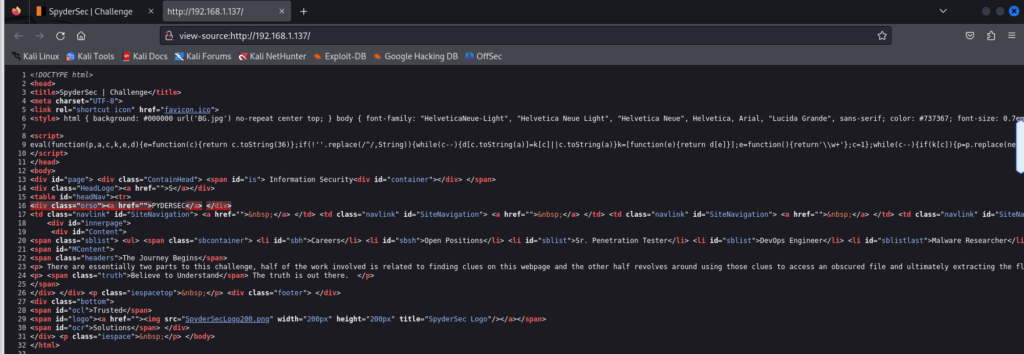
eval(function(p,a,c,k,e,d){e=function(c){return c.toString(36)};if(!''.replace(/^/,String)){while(c--){d[c.toString(a)]=k[c]||c.toString(a)}k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('7:0:1:2:8:6:3:5:4:0:a:1:2:d:c:b:f:3:9:e',16,16,'6c|65|72|27|75|6d|28|61|74|29|64|62|66|2e|3b|69'.split('|'),0,{}))
运行报错了 看着像是被混淆了 反混淆一下 在线JS反混淆解密还原工具 – 爱图工具箱 (itutool.com)
61:6c:65:72:74:28:27:6d:75:6c:64:65:72:2e:66:62:69:27:29:3b
alert('mulder.fbi');
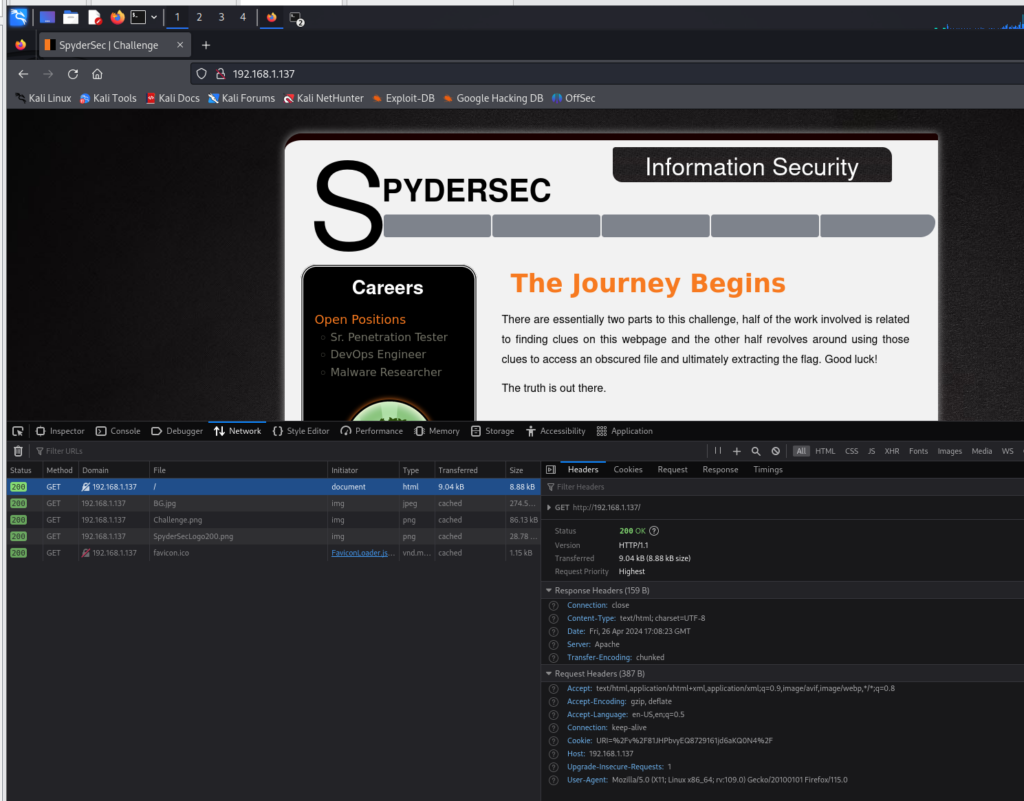
三、F12查看响应包的内容
可以看到 cookie中有一个url
Cookie URI=%2Fv%2F81JHPbvyEQ8729161jd6aKQ0N4%2F
直接访问不了 加上上面的mulder.fbi 可以下载一个mp4文件
wget http://192.168.1.137/v/81JHPbvyEQ8729161jd6aKQ0N4/mulder.fbi